Sailing the Seven Seas Securely from Port to Port – OT Access Security for Ships and Cranes
by nlqip
Oct 28, 2024The Hacker NewsOperational Technology / Cybersecurity Operational Technology (OT) security has affected marine vessel and port operators, since both ships and industrial cranes are being digitalized and automated at a rapid pace, ushering in new types of security challenges. Ships come to shore every six months on average. Container cranes are mostly automated.…
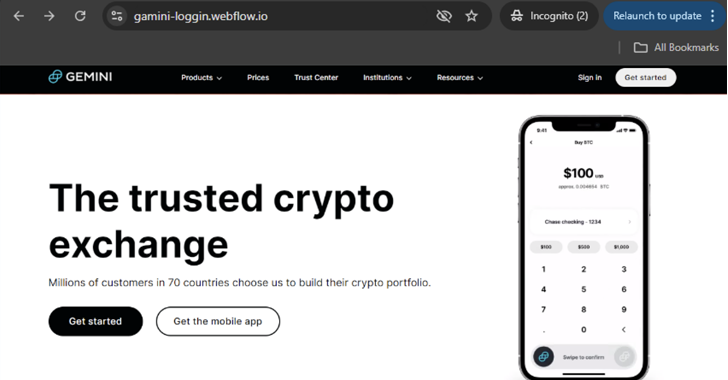
Read MoreCybersecurity researchers have warned of a spike in phishing pages created using a website builder tool called Webflow, as threat actors continue to abuse legitimate services like Cloudflare and Microsoft Sway to their advantage. “The campaigns target sensitive information from different crypto wallets, including Coinbase, MetaMask, Phantom, Trezor, and Bitbuy, as well as login credentials…
Read MoreSecurity Information and Event Management (SIEM) systems play a crucial role in modern cybersecurity strategies. These powerful tools collect, analyze, and correlate data from various sources across an organization’s IT infrastructure to detect and respond to security threats. However, the effectiveness of a SIEM solution heavily depends on how well an organization manages and retains…
Read MoreOct 28, 2024Ravie LakshmananVulnerability / Windows Security A new attack technique could be used to bypass Microsoft’s Driver Signature Enforcement (DSE) on fully patched Windows systems, leading to operating system (OS) downgrade attacks. “This bypass allows loading unsigned kernel drivers, enabling attackers to deploy custom rootkits that can neutralize security controls, hide processes and network…
Read MoreFog and Akira ransomware operators are increasingly breaching corporate networks through SonicWall VPN accounts, with the threat actors believed to be exploiting CVE-2024-40766, a critical SSL VPN access control flaw. SonicWall fixed the SonicOS flaw in late August 2024, and roughly a week later, it warned that it was already under active exploitation. At the…
Read MoreWindows 11 24H2 is unavailable for thousands of users due to safeguard or compatibility holds Microsoft has placed on specific device and software configurations. Microsoft places compatibility holds on specific devices using hardware or applications that may conflict with Windows 11 24H2, causing crashes, performance issues, freezes, or other unusual behavior. These holds will prevent…
Read MoreA threat actor claimed that they have and are selling 280 million U.S. citizens’ personal data on dark web. According to the post of the threat actor, the data includes; First_Name、Last_Name Address、City、State、ZIP Ind_Date_Of_Birth_Year、Ind_Age Home_Value_Code、Home_Median_Value_Code、Median_Income_Code Email、Phone They are also claiming that they can provide sample data to the prospects. Meanwhile, they did not mention the source…
Read MoreCisco has added new security features that significantly mitigate brute-force and password spray attacks on Cisco ASA and Firepower Threat Defense (FTD), helping protect the network from breaches and reducing resource utilization on devices. Password spray and brute force attacks are similar in that they both attempt to gain unauthorized access to an online account by guessing…
Read MoreAttackers can downgrade Windows kernel components to bypass security features such as Driver Signature Enforcement and deploy rootkits on fully patched systems. This is possible by taking control of the Windows Update process to introduce outdated, vulnerable software components on an up-to-date machine without the operating system changing the fully patched status. Downgrading Windows SafeBreach…
Read MoreThe fourth day of Pwn2Own Ireland 2024 marked the end of the hacking competition with more than $1 million in prizes for over 70 unique zero-day vulnerabilities in fully patched devices. The hacking contest pits security researchers against various software and hardware products, in an attempt earn the “Master of Pwn” title by compromising targets in eight categories…
Read MoreRecent Posts
- Five HPE GreenLake Game Changers: A Look At Pay-Per-Use Cloud Service Improvements
- Multiple Vulnerabilities in Adobe Products Could Allow for Arbitrary Code Execution
- Critical Patches Issued for Microsoft Products, January 14, 2025
- CISA Releases Four Industrial Control Systems Advisories | CISA
- Ivanti Releases Security Updates for Multiple Products | CISA