Tag: computer security
May 30, 2024NewsroomLinux / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a security flaw impacting the Linux kernel to the Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. Tracked as CVE-2024-1086 (CVSS score: 7.8), the high-severity issue relates to a use-after-free bug in the netfilter component that permits…
Read MoreMay 30, 2024NewsroomCyber Attack / Malware Cloudflare on Thursday said it took steps to disrupt a month-long phishing campaign orchestrated by a Russia-aligned threat actor called FlyingYeti targeting Ukraine. “The FlyingYeti campaign capitalized on anxiety over the potential loss of access to housing and utilities by enticing targets to open malicious files via debt-themed lures,”…
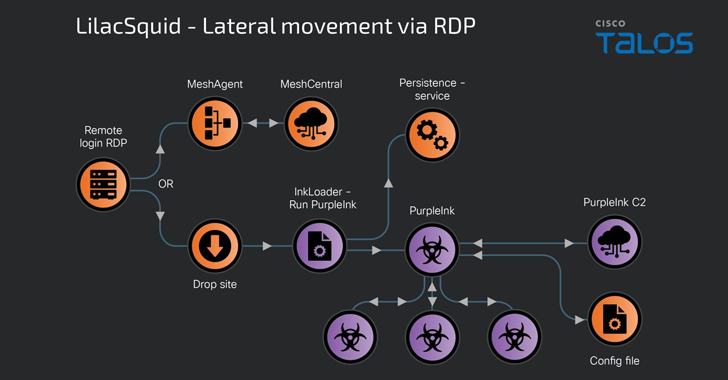
Read MoreMay 30, 2024NewsroomCyber Espionage / Threat Intelligence A previously undocumented cyber espionage-focused threat actor named LilacSquid has been linked to targeted attacks spanning various sectors in the United States (U.S.), Europe, and Asia as part of a data theft campaign since at least 2021. “The campaign is geared toward establishing long-term access to compromised victim…
Read MoreMay 30, 2024NewsroomVulnerability / Cryptocurrency The threat actors behind the RedTail cryptocurrency mining malware have added a recently disclosed security flaw impacting Palo Alto Networks firewalls to its exploit arsenal. The addition of the PAN-OS vulnerability to its toolkit has been complemented by updates to the malware, which now incorporates new anti-analysis techniques, according to…
Read MoreMay 30, 2024NewsroomWordPress / Website Security Cybersecurity researchers have warned that multiple high-severity security vulnerabilities in WordPress plugins are being actively exploited by threat actors to create rogue administrator accounts for follow-on exploitation. “These vulnerabilities are found in various WordPress plugins and are prone to unauthenticated stored cross-site scripting (XSS) attacks due to inadequate input…
Read MoreSecurity leaders are in a tricky position trying to discern how much new AI-driven cybersecurity tools could actually benefit a security operations center (SOC). The hype about generative AI is still everywhere, but security teams have to live in reality. They face constantly incoming alerts from endpoint security platforms, SIEM tools, and phishing emails reported…
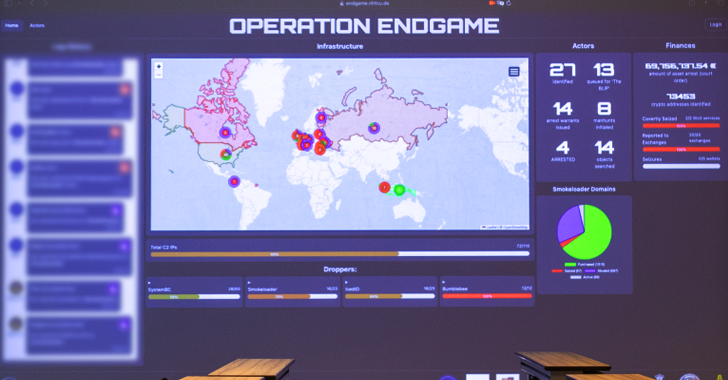
Read MoreMay 30, 2024NewsroomMalware / Cyber Crime Europol on Thursday said it shut down the infrastructure associated with several malware loader operations such as IcedID, SystemBC, PikaBot, SmokeLoader, Bumblebee, and TrickBot as part of a coordinated law enforcement effort codenamed Operation Endgame. “The actions focused on disrupting criminal services through arresting High Value Targets, taking down…
Read MoreThe U.S. Department of Justice (DoJ) on Wednesday said it dismantled what it described as “likely the world’s largest botnet ever,” which consisted of an army of 19 million infected devices that was leased to other threat actors to commit a wide array of offenses. The botnet, which has a global footprint spanning more than…
Read MoreMay 30, 2024NewsroomCredential Stuffing / Incident Response Okta is warning that a cross-origin authentication feature in Customer Identity Cloud (CIC) is susceptible to credential stuffing attacks orchestrated by threat actors. “We observed that the endpoints used to support the cross-origin authentication feature being attacked via credential stuffing for a number of our customers,” the Identity…
Read MoreMay 29, 2024NewsroomSoftware Security / Supply Chain Cybersecurity researchers have warned of a new malicious Python package that has been discovered in the Python Package Index (PyPI) repository to facilitate cryptocurrency theft as part of a broader campaign. The package in question is pytoileur, which has been downloaded 316 times as of writing. Interestingly, the…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm