Tag: computer security
״Defenders think in lists, attackers think in graphs,” said John Lambert from Microsoft, distilling the fundamental difference in mindset between those who defend IT systems and those who try to compromise them. The traditional approach for defenders is to list security gaps directly related to their assets in the network and eliminate as many as…
Read MoreMay 08, 2024NewsroomEncryption / Information Stealer A newer version of a malware loader called Hijack Loader has been observed incorporating an updated set of anti-analysis techniques to fly under the radar. “These enhancements aim to increase the malware’s stealthiness, thereby remaining undetected for longer periods of time,” Zscaler ThreatLabz researcher Muhammed Irfan V A said…
Read MoreMay 08, 2024NewsroomWeb Security / Vulnerability A high-severity flaw impacting the LiteSpeed Cache plugin for WordPress is being actively exploited by threat actors to create rogue admin accounts on susceptible websites. The findings come from WPScan, which said that the vulnerability (CVE-2023-40000, CVSS score: 8.3) has been leveraged to set up bogus admin users with…
Read MoreThe U.K. National Crime Agency (NCA) has unmasked the administrator and developer of the LockBit ransomware operation, revealing it to be a 31-year-old Russian national named Dmitry Yuryevich Khoroshev. In addition, Khoroshev has been sanctioned by the U.K. Foreign, Commonwealth and Development Office (FCD), the U.S. Department of the Treasury’s Office of Foreign Assets Control…
Read MoreMay 07, 2024NewsroomVulnerability / Network Security The MITRE Corporation has offered more details into the recently disclosed cyber attack, stating that the first evidence of the intrusion now dates back to December 31, 2023. The attack, which came to light last month, singled out MITRE’s Networked Experimentation, Research, and Virtualization Environment (NERVE) through the exploitation…
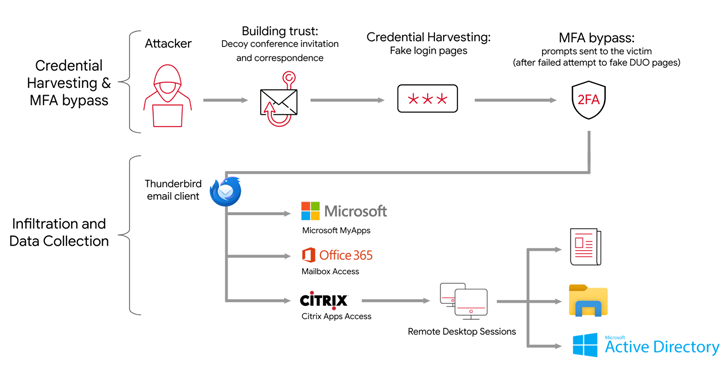
Read MoreThe Iranian state-backed hacking outfit called APT42 is making use of enhanced social engineering schemes to infiltrate target networks and cloud environments. Targets of the attack include Western and Middle Eastern NGOs, media organizations, academia, legal services and activists, Google Cloud subsidiary Mandiant said in a report published last week. “APT42 was observed posing as…
Read MoreMay 07, 2024The Hacker NewsRegulatory Compliance / Cyber Threat How safe is your comments section? Discover how a seemingly innocent ‘thank you’ comment on a product page concealed a malicious vulnerability, underscoring the necessity of robust security measures. Read the full real-life case study here. When is a ‘Thank you’ not a ‘Thank you’? When…
Read MoreMay 07, 2024NewsroomOnline Security / Data Breach Google on Monday announced that it’s simplifying the process of enabling two-factor authentication (2FA) for users with personal and Workspace accounts. Also called, 2-Step Verification (2SV), it aims to add an extra layer of security to users’ accounts to prevent takeover attacks in case the passwords are stolen.…
Read MoreMay 07, 2024NewsroomCryptocurrency / Cybercrime A Russian operator of a now-dismantled BTC-e cryptocurrency exchange has pleaded guilty to money laundering charges from 2011 to 2017. Alexander Vinnik, 44, was charged in January 2017 and taken into custody in Greece in July 2017. He was subsequently extradited to the U.S. in August 2022. Vinnik and his…
Read MoreMay 06, 2024NewsroomVulnerability / Server Security More than 50% of the 90,310 hosts have been found exposing a Tinyproxy service on the internet that’s vulnerable to a critical unpatched security flaw in the HTTP/HTTPS proxy tool. The issue, tracked as CVE-2023-49606, carries a CVSS score of 9.8 out of a maximum of 10, per Cisco…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm