Tag: computer security
Apr 18, 2024NewsroomCyber Attack / Malware The infamous cybercrime syndicate known as FIN7 has been linked to a spear-phishing campaign targeting the U.S. automotive industry to deliver a known backdoor called Carbanak (aka Anunak). “FIN7 identified employees at the company who worked in the IT department and had higher levels of administrative rights,” the BlackBerry…
Read MoreAs many as 37 individuals have been arrested as part of an international crackdown on a cybercrime service called LabHost that has been used by criminal actors to steal personal credentials from victims around the world. Described as one of the largest Phishing-as-a-Service (PhaaS) providers, LabHost offered phishing pages targeting banks, high-profile organizations, and other…
Read MoreApr 18, 2024NewsroomMobile Security / Malware A new Android trojan called SoumniBot has been detected in the wild targeting users in South Korea by leveraging weaknesses in the manifest extraction and parsing procedure. The malware is “notable for an unconventional approach to evading analysis and detection, namely obfuscation of the Android manifest,” Kaspersky researcher Dmitry…
Read MoreSandboxes are synonymous with dynamic malware analysis. They help to execute malicious files in a safe virtual environment and observe their behavior. However, they also offer plenty of value in terms of static analysis. See these five scenarios where a sandbox can prove to be a useful tool in your investigations. Detecting Threats in PDFs…
Read MoreSuper Low RPO with Continuous Data Protection: Dial Back to Just Seconds Before an Attack Zerto, a Hewlett Packard Enterprise company, can help you detect and recover from ransomware in near real-time. This solution leverages continuous data protection (CDP) to ensure all workloads have the lowest recovery point objective (RPO) possible. The most valuable thing…
Read MoreApr 18, 2024NewsroomContainer Security / Cryptocurrency Threat actors are actively exploiting critical vulnerabilities in OpenMetadata to gain unauthorized access to Kubernetes workloads and leverage them for cryptocurrency mining activity. That’s according to the Microsoft Threat Intelligence team, which said the flaws have been weaponized since the start of April 2024. OpenMetadata is an open-source platform…
Read MoreApr 18, 2024NewsroomMalvertising / Endpoint Security A new Google malvertising campaign is leveraging a cluster of domains mimicking a legitimate IP scanner software to deliver a previously unknown backdoor dubbed MadMxShell. “The threat actor registered multiple look-alike domains using a typosquatting technique and leveraged Google Ads to push these domains to the top of search…
Read MoreApr 17, 2024NewsroomRansomware / Cyber Espionage A previously undocumented “flexible” backdoor called Kapeka has been “sporadically” observed in cyber attacks targeting Eastern Europe, including Estonia and Ukraine, since at least mid-2022. The findings come from Finnish cybersecurity firm WithSecure, which attributed the malware to the Russia-linked advanced persistent threat (APT) group tracked as Sandworm (aka…
Read MoreThe introduction of Open AI’s ChatGPT was a defining moment for the software industry, touching off a GenAI race with its November 2022 release. SaaS vendors are now rushing to upgrade tools with enhanced productivity capabilities that are driven by generative AI. Among a wide range of uses, GenAI tools make it easier for developers…
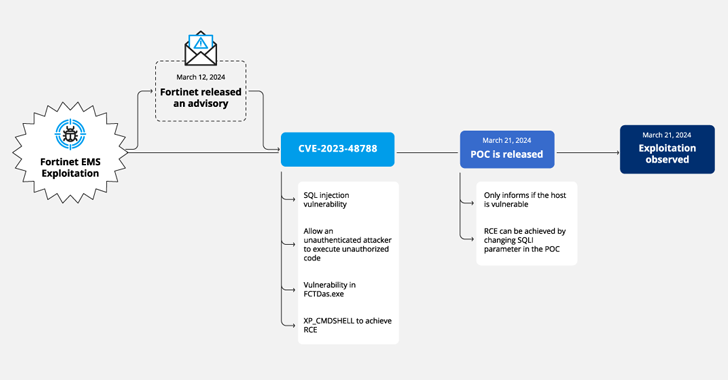
Read MoreApr 17, 2024NewsroomVulnerability / Web Application Firewall Cybersecurity researchers have discovered a new campaign that’s exploiting a recently disclosed security flaw in Fortinet FortiClient EMS devices to deliver ScreenConnect and Metasploit Powerfun payloads. The activity entails the exploitation of CVE-2023-48788 (CVSS score: 9.3), a critical SQL injection flaw that could permit an unauthenticated attacker to…
Read More