Tag: cyber attacks
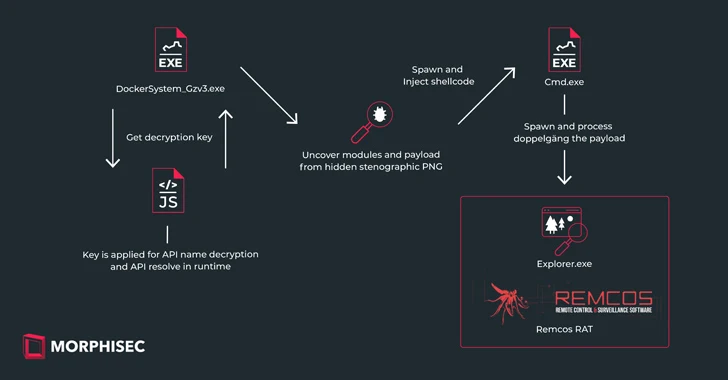
Feb 26, 2024The Hacker NewsSteganography / Malware Ukrainian entities based in Finland have been targeted as part of a malicious campaign distributing a commercial remote access trojan known as Remcos RAT using a malware loader called IDAT Loader. The attack has been attributed to a threat actor tracked by the Computer Emergency Response Team of…
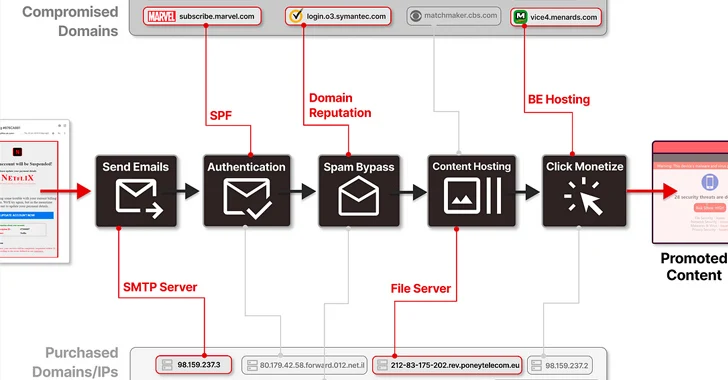
Read MoreMore than 8,000 subdomains belonging to legitimate brands and institutions have been hijacked as part of a sophisticated distribution architecture for spam proliferation and click monetization. Guardio Labs is tracking the coordinated malicious activity, which has been ongoing since at least September 2022, under the name SubdoMailing. The emails range from “counterfeit package delivery alerts…
Read MoreFeb 26, 2024The Hacker NewsSoftware Security / Cryptocurrency A set of fake npm packages discovered on the Node.js repository has been found to share ties with North Korean state-sponsored actors, new findings from Phylum show. The packages are named execution-time-async, data-time-utils, login-time-utils, mongodb-connection-utils, and mongodb-execution-utils. One of the packages in question, execution-time-async, masquerades as its…
Read MoreLast year, the Open Worldwide Application Security Project (OWASP) published multiple versions of the “OWASP Top 10 For Large Language Models,” reaching a 1.0 document in August and a 1.1 document in October. These documents not only demonstrate the rapidly evolving nature of Large Language Models, but the evolving ways in which they can be…
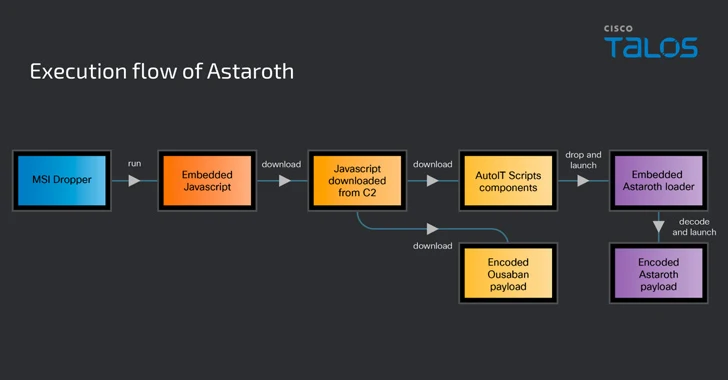
Read MoreCybersecurity researchers are warning about a spike in email phishing campaigns that are weaponizing the Google Cloud Run service to deliver various banking trojans such as Astaroth (aka Guildma), Mekotio, and Ousaban (aka Javali) to targets across Latin America (LATAM) and Europe. “The infection chains associated with these malware families feature the use of malicious…
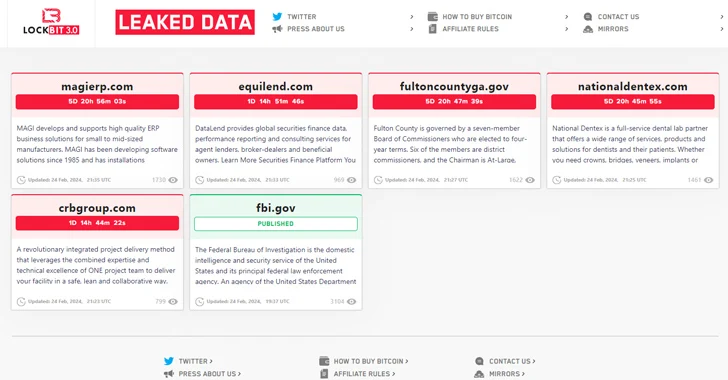
Read MoreThe threat actors behind the LockBit ransomware operation have resurfaced on the dark web using new infrastructure, days after an international law enforcement exercise seized control of its servers. To that end, the notorious group has moved its data leak portal to a new .onion address on the TOR network, listing 12 new victims as…
Read MoreLockBitSupp, the individual(s) behind the persona representing the LockBit ransomware service on cybercrime forums such as Exploit and XSS, “has engaged with law enforcement,” authorities said. The development comes following the takedown of the prolific ransomware-as-a-service (RaaS) operation as part of a coordinated international operation codenamed Cronos. Over 14,000 rogue accounts on third-party services like…
Read MoreFeb 24, 2024NewsroomActive Directory / Data Protection Microsoft has expanded free logging capabilities to all U.S. federal agencies using Microsoft Purview Audit irrespective of the license tier, more than six months after a China-linked cyber espionage campaign targeting two dozen organizations came to light. “Microsoft will automatically enable the logs in customer accounts and increase…
Read MoreFeb 23, 2024NewsroomSupply Chain Attack / Malware A dormant package available on the Python Package Index (PyPI) repository was updated nearly after two years to propagate an information stealer malware called Nova Sentinel. The package, named django-log-tracker, was first published to PyPI in April 2022, according to software supply chain security firm Phylum, which detected…
Read MoreCreated by John Tuckner and the team at workflow and automation platform Tines, the SOC Automation Capability Matrix (SOC ACM) is a set of techniques designed to help security operations teams understand their automation capabilities and respond more effectively to incidents. A customizable, vendor-agnostic tool featuring lists of automation opportunities, it’s been shared and recommended…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA