Tag: cyber attacks
One of the most effective ways for information technology (IT) professionals to uncover a company’s weaknesses before the bad guys do is penetration testing. By simulating real-world cyberattacks, penetration testing, sometimes called pentests, provides invaluable insights into an organization’s security posture, revealing weaknesses that could potentially lead to data breaches or other security incidents. Vonahi…
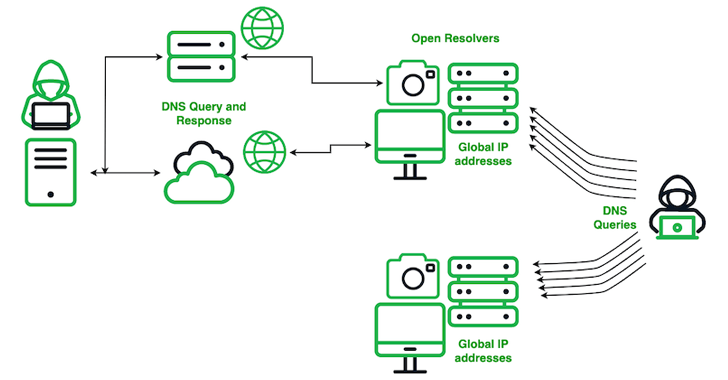
Read MoreCybersecurity researchers have shed more light on a Chinese actor codenamed SecShow that has been observed conducting Domain Name System (DNS) on a global scale since at least June 2023. The adversary, according to Infoblox security researchers Dr. Renée Burton and Dave Mitchell, operates from the China Education and Research Network (CERNET), a project funded…
Read MoreJun 11, 2024The Hacker NewsEndpoint Security / Incident Response Managed service providers (MSPs) are on the front lines of soaring demand for cybersecurity services as cyberattacks increase in volume and sophistication. Cynet has emerged as the security vendor of choice for MSPs to capitalize on existing relationships with SMB clients and profitably expand their client…
Read MoreJun 11, 2024NewsroomCloud Computing / Artificial Intelligence Apple has announced the launch of a “groundbreaking cloud intelligence system” called Private Cloud Compute (PCC) that’s designed for processing artificial intelligence (AI) tasks in a privacy-preserving manner in the cloud. The tech giant described PCC as the “most advanced security architecture ever deployed for cloud AI compute…
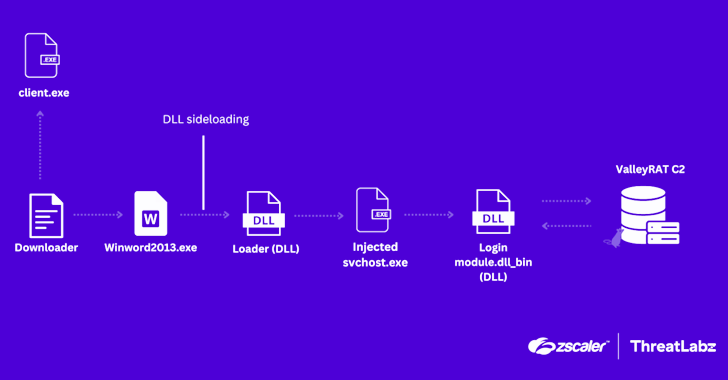
Read MoreJun 11, 2024NewsroomMalware / Cyber Attack Cybersecurity researchers have uncovered an updated version of malware called ValleyRAT that’s being distributed as part of a new campaign. “In the latest version, ValleyRAT introduced new commands, such as capturing screenshots, process filtering, forced shutdown, and clearing Windows event logs,” Zscaler ThreatLabz researchers Muhammed Irfan V A and…
Read MoreJun 11, 2024NewsroomMobile Security / Technology Arm is warning of a security vulnerability impacting Mali GPU Kernel Driver that it said has been actively exploited in the wild. Tracked as CVE-2024-4610, the use-after-free issue impacts the following products – “A local non-privileged user can make improper GPU memory processing operations to gain access to already…
Read MoreJun 11, 2024NewsroomData Theft / Cloud Security As many as 165 customers of Snowflake are said to have had their information potentially exposed as part of an ongoing campaign designed to facilitate data theft and extortion, indicating the operation has broader implications than previously thought. Google-owned Mandiant, which is assisting the cloud data warehousing platform…
Read MoreJun 10, 2024NewsroomPhishing Attack / Cybercrime Cybersecurity researchers have spotted a phishing attack distributing the More_eggs malware by masquerading it as a resume, a technique originally detected more than two years ago. The attack, which was unsuccessful, targeted an unnamed company in the industrial services industry in May 2024, Canadian cybersecurity firm eSentire disclosed last…
Read MoreGoogle has revealed that it took down 1,320 YouTube channels and 1,177 Blogger blogs as part of a coordinated influence operation connected to the People’s Republic of China (PRC). “The coordinated inauthentic network uploaded content in Chinese and English about China and U.S. foreign affairs,” Google Threat Analysis Group (TAG) researcher Billy Leonard said in…
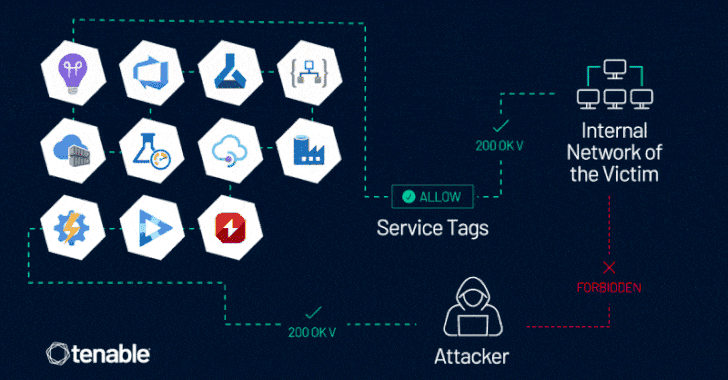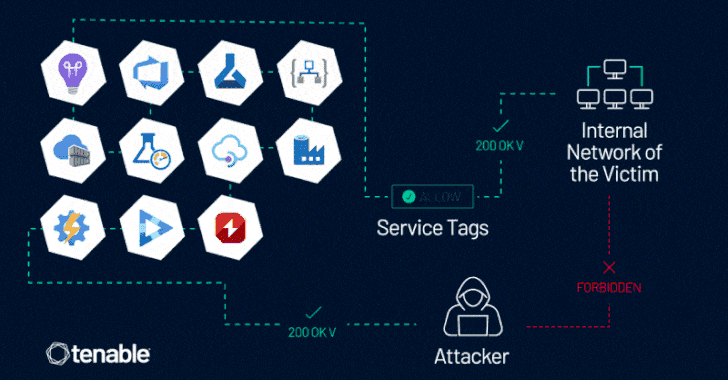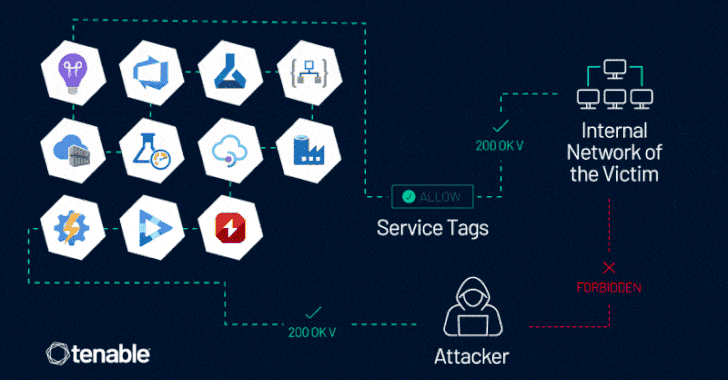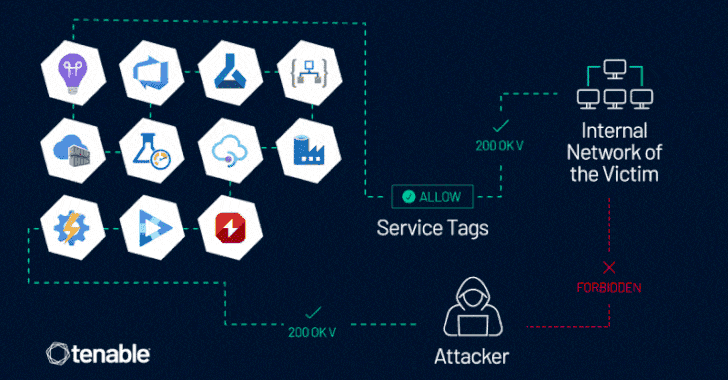
Read MoreJun 10, 2024NewsroomCloud Security / Vulnerability Microsoft is warning about the potential abuse of Azure Service Tags by malicious actors to forge requests from a trusted service and get around firewall rules, thereby allowing them to gain unauthorized access to cloud resources. “This case does highlight an inherent risk in using service tags as a…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm