Tag: cyber attacks
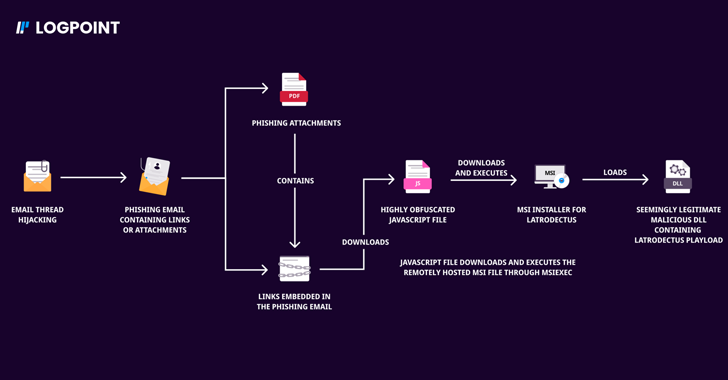
Oct 22, 2024Ravie LakshmananMalware / Threat Intelligence Two malware families that suffered setbacks in the aftermath of a coordinated law enforcement operation called Endgame have resurfaced as part of new phishing campaigns. Bumblebee and Latrodectus, which are both malware loaders, are designed to steal personal data, along with downloading and executing additional payloads onto compromised…
Read MoreOct 22, 2024Ravie LakshmananVulnerability / Enterprise Security VMware has released software updates to address an already patched security flaw in vCenter Server that could pave the way for remote code execution. The vulnerability, tracked as CVE-2024-38812 (CVSS score: 9.8), concerns a case of heap-overflow vulnerability in the implementation of the DCE/RPC protocol. “A malicious actor…
Read MoreOct 22, 2024Ravie LakshmananVulnerability / Cyber Threat The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a critical security flaw impacting ScienceLogic SL1 to its Known Exploited Vulnerabilities (KEV) catalog, following reports of active exploitation as a zero-day. The vulnerability in question, tracked as CVE-2024-9537 (CVSS v4 score: 9.3), refers to a bug…
Read MoreThe prolific Chinese nation-state actor known as APT41 (aka Brass Typhoon, Earth Baku, Wicked Panda, or Winnti) has been attributed to a sophisticated cyber attack targeting the gambling and gaming industry. “Over a period of at least six months, the attackers stealthily gathered valuable information from the targeted company including, but not limited to, network…
Read MoreOct 21, 2024Mohit KumarCybersecurity / Weekly Recap Hi there! Here’s your quick update on the latest in cybersecurity. Hackers are using new tricks to break into systems we thought were secure—like finding hidden doors in locked houses. But the good news? Security experts are fighting back with smarter tools to keep data safe. Some big…
Read MoreOct 21, 2024The Hacker NewsPenetration Testing / API Security Pentest Checklists Are More Important Than Ever Given the expanding attack surface coupled with the increasing sophistication of attacker tactics and techniques, penetration testing checklists have become essential for ensuring thorough assessments across an organization’s attack surface, both internal and external. By providing a structured approach,…
Read MoreOct 21, 2024Ravie LakshmananEncryption / Data Protection Cybersecurity researchers have discovered severe cryptographic issues in various end-to-end encrypted (E2EE) cloud storage platforms that could be exploited to leak sensitive data. “The vulnerabilities range in severity: in many cases a malicious server can inject files, tamper with file data, and even gain direct access to plaintext,”…
Read MoreOct 20, 2024Ravie LakshmananVulnerability / Email Security Unknown threat actors have been observed attempting to exploit a now-patched security flaw in the open-source Roundcube webmail software as part of a phishing attack designed to steal user credentials. Russian cybersecurity company Positive Technologies said it discovered last month that an email was sent to an unspecified…
Read MoreIn the modern enterprise, data security is often discussed using a complex lexicon of acronyms—DLP, DDR, DSPM, and many others. While these acronyms represent critical frameworks, architectures, and tools for protecting sensitive information, they can also overwhelm those trying to piece together an effective security strategy. This article aims to demystify some of the most…
Read MoreOct 19, 2024Ravie LakshmananNetwork Security / Data Breach A nascent threat actor known as Crypt Ghouls has been linked to a set of cyber attacks targeting Russian businesses and government agencies with ransomware with the twin goals of disrupting business operations and financial gain. “The group under review has a toolkit that includes utilities such…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA