Tag: cyber news
Feb 22, 2024NewsroomQuantum Computing / Encryption Apple has announced a new post-quantum cryptographic protocol called PQ3 that it said will be integrated into iMessage to secure the messaging platform against future attacks arising from the threat of a practical quantum computer. “With compromise-resilient encryption and extensive defenses against even highly sophisticated quantum attacks, PQ3 is…
Read MoreFeb 22, 2024NewsroomMalware / Cyber Espionage An installer for a tool likely used by the Russian Consular Department of the Ministry of Foreign Affairs (MID) has been backdoored to deliver a remote access trojan called Konni RAT (aka UpDog). The findings come from German cybersecurity company DCSO, which linked the activity as originating from the…
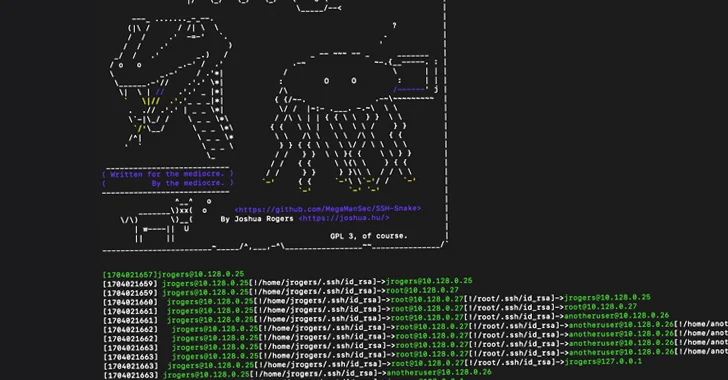
Read MoreFeb 22, 2024NewsroomNetwork Security / Penetration Testing A recently open-sourced network mapping tool called SSH-Snake has been repurposed by threat actors to conduct malicious activities. “SSH-Snake is a self-modifying worm that leverages SSH credentials discovered on a compromised system to start spreading itself throughout the network,” Sysdig researcher Miguel Hernández said. “The worm automatically searches…
Read MoreIn the past 2 years, we have observed a significant surge in hacktivism activity due to ongoing wars and geopolitical conflicts in various regions. Since the war against Ukraine began, we have witnessed a notable mobilization of non-state and state-backed actors alike, forming new groups or joining existing hacker collectives. We understand hacktivism as a…
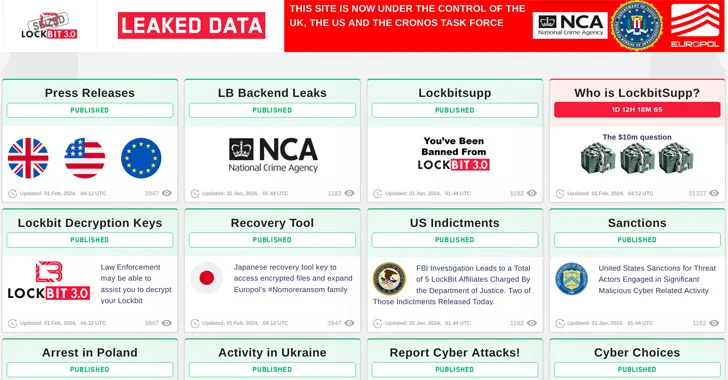
Read MoreThe U.S. State Department has announced monetary rewards of up to $15 million for information that could lead to the identification of key leaders within the LockBit ransomware group and the arrest of any individual participating in the operation. “Since January 2020, LockBit actors have executed over 2,000 attacks against victims in the United States,…
Read MoreFeb 21, 2024Newsroom Cybersecurity researchers have identified two authentication bypass flaws in open-source Wi-Fi software found in Android, Linux, and ChromeOS devices that could trick users into joining a malicious clone of a legitimate network or allow an attacker to join a trusted network without a password. The vulnerabilities, tracked as CVE-2023-52160 and CVE-2023-52161, have…
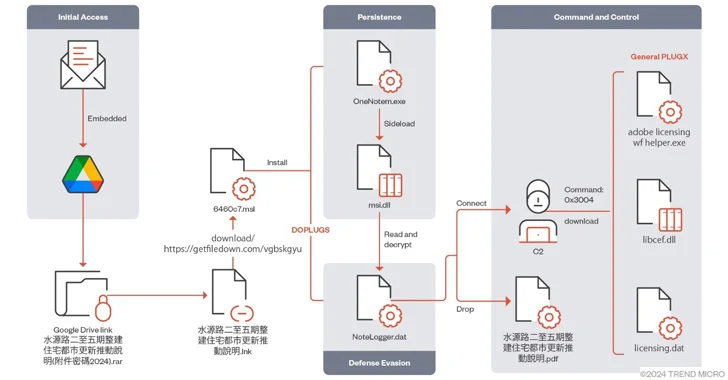
Read MoreFeb 21, 2024NewsroomMalware / Cyber Espionage The China-linked threat actor known as Mustang Panda has targeted various Asian countries using a variant of the PlugX (aka Korplug) backdoor dubbed DOPLUGS. “The piece of customized PlugX malware is dissimilar to the general type of the PlugX malware that contains a completed backdoor command module, and that…
Read MoreWith SaaS applications now making up the vast majority of technology used by employees in most organizations, tasks related to identity governance need to happen across a myriad of individual SaaS apps. This presents a huge challenge for centralized IT teams who are ultimately held responsible for managing and securing app access, but can’t possibly…
Read MoreCybersecurity for Healthcare—Diagnosing the Threat Landscape and Prescribing Solutions for Recovery
by nlqip
On Thanksgiving Day 2023, while many Americans were celebrating, hospitals across the U.S. were doing quite the opposite. Systems were failing. Ambulances were diverted. Care was impaired. Hospitals in three states were hit by a ransomware attack, and in that moment, the real-world repercussions came to light—it wasn’t just computer networks that were brought to…
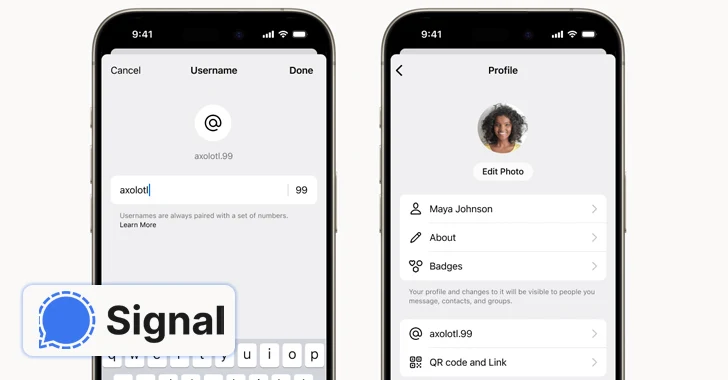
Read MoreFeb 21, 2024NewsroomSecure Communication / Anonymity End-to-end encrypted (E2EE) messaging app Signal said it’s piloting a new feature that allows users to create unique usernames (not to be confused with profile names) and keep the phone numbers away from prying eyes. “If you use Signal, your phone number will no longer be visible to everyone…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA