Tag: cyber news
Jul 10, 2024NewsroomCybersecurity / Phishing Attack Google on Wednesday announced that it’s making available passkeys for high-risk users to enroll in its Advanced Protection Program (APP). “Users traditionally needed a physical security key for APP — now they can choose a passkey to secure their account,” Shuvo Chatterjee, product lead of APP, said. Passkeys are…
Read MoreJul 10, 2024NewsroomOnline Scam / Blockchain Cryptocurrency analysts have shed light on an online marketplace called HuiOne Guarantee that’s widely used by cybercriminals in Southeast Asia, particularly those linked to pig butchering scams. “Merchants on the platform offer technology, data, and money laundering services, and have engaged in transactions totaling at least $11 billion,” Elliptic…
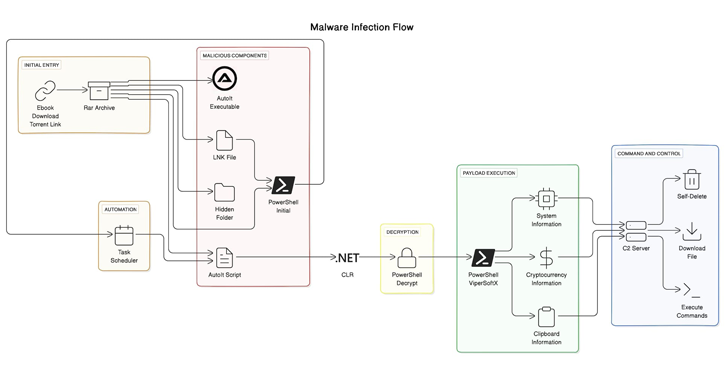
Read MoreJul 10, 2024NewsroomEndpoint Security / Threat Intelligence The sophisticated malware known as ViperSoftX has been observed being distributed as eBooks over torrents. “A notable aspect of the current variant of ViperSoftX is that it uses the Common Language Runtime (CLR) to dynamically load and run PowerShell commands, thereby creating a PowerShell environment within AutoIt for…
Read MoreJul 10, 2024NewsroomVulnerability / Network Security Select versions of the OpenSSH secure networking suite are susceptible to a new vulnerability that can trigger remote code execution (RCE). The vulnerability, tracked as CVE-2024-6409 (CVSS score: 7.0), is distinct from CVE-2024-6387 (aka RegreSSHion) and relates to a case of code execution in the privsep child process due…
Read MoreJul 09, 2024NewsroomVulnerability / Network Security Cybersecurity researchers have discovered a security vulnerability in the RADIUS network authentication protocol called BlastRADIUS that could be exploited by an attacker to stage Mallory-in-the-middle (MitM) attacks and bypass integrity checks under certain circumstances. “The RADIUS protocol allows certain Access-Request messages to have no integrity or authentication checks,” InkBridge…
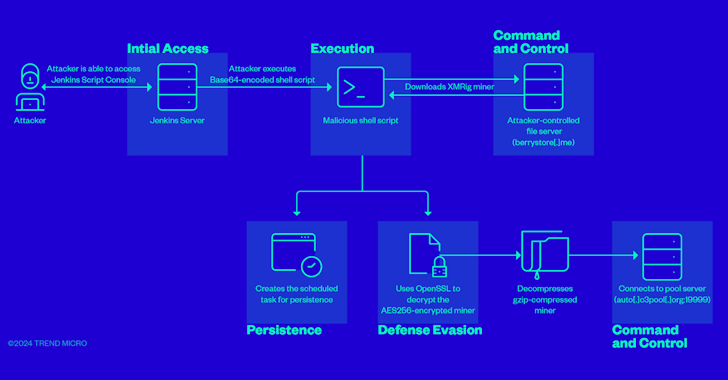
Read MoreJul 09, 2024NewsroomCI/CD Security / Server Security Cybersecurity researchers have found that it’s possible for attackers to weaponize improperly configured Jenkins Script Console instances to further criminal activities such as cryptocurrency mining. “Misconfigurations such as improperly set up authentication mechanisms expose the ‘/script’ endpoint to attackers,” Trend Micro’s Shubham Singh and Sunil Bharti said in…
Read MoreJul 09, 2024Newsroom Military personnel from Middle East countries are the target of an ongoing surveillanceware operation that delivers an Android data-gathering tool called GuardZoo. The campaign, believed to have commenced as early as October 2019, has been attributed to a Houthi-aligned threat actor based on the application lures, command-and-control (C2) server logs, targeting footprint,…
Read MoreClear Web vs. Deep Web vs. Dark Web Threat intelligence professionals divide the internet into three main components: Clear Web – Web assets that can be viewed through public search engines, including media, blogs, and other pages and sites. Deep Web – Websites and forums that are unindexed by search engines. For example, webmail, online…
Read MoreJul 09, 2024NewsroomCyber Espionage / Threat Intelligence Cybersecurity agencies from Australia, Canada, Germany, Japan, New Zealand, South Korea, the U.K., and the U.S. have released a joint advisory about a China-linked cyber espionage group called APT40, warning about its ability to co-opt exploits for newly disclosed security flaws within hours or days of public release.…
Read MoreJul 09, 2024NewsroomSupply Chain Attack / Web Security Unknown threat actors have been found propagating trojanized versions of jQuery on npm, GitHub, and jsDelivr in what appears to be an instance of a “complex and persistent” supply chain attack. “This attack stands out due to the high variability across packages,” Phylum said in an analysis…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm