Tag: cyber news
Jun 13, 2024NewsroomCyber Crime / Ransomware The Cyber Police of Ukraine has announced the arrest of a local man who is suspected to have offered their services to LockBit and Conti ransomware groups. The unnamed 28-year-old native of the Kharkiv region allegedly specialized in the development of crypters to encrypt and obfuscate malicious payloads in…
Read MoreJun 13, 2024NewsroomMobile Security / Vulnerability Google has warned that a security flaw impacting Pixel Firmware has been exploited in the wild as a zero-day. The high-severity vulnerability, tagged as CVE-2024-32896, has been described as an elevation of privilege issue in Pixel Firmware. The company did not share any additional details related to the nature…
Read MoreJun 13, 2024NewsroomCyber Attack / Malware A previously undocumented cross-platform malware codenamed Noodle RAT has been put to use by Chinese-speaking threat actors either for espionage or cybercrime for years. While this backdoor was previously categorized as a variant of Gh0st RAT and Rekoobe, Trend Micro security researcher Hara Hiroaki said “this backdoor is not…
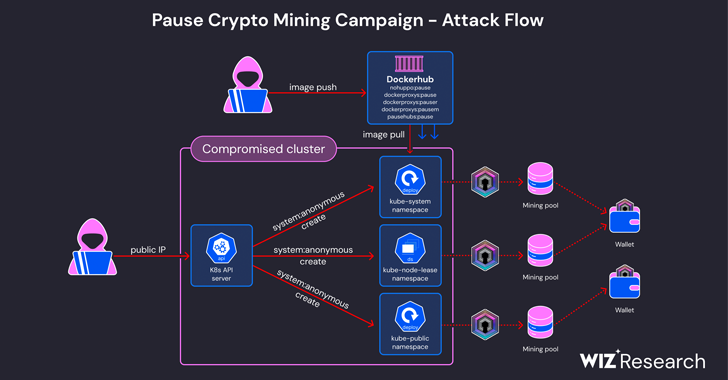
Read MoreJun 12, 2024NewsroomKubernetes / Endpoint Security Cybersecurity researchers have warned of an ongoing cryptojacking campaign targeting misconfigured Kubernetes clusters to mine Dero cryptocurrency. Cloud security firm Wiz, which shed light on the activity, said it’s an updated variant of a financially motivated operation that was first documented by CrowdStrike in March 2023. “In this incident,…
Read MoreJun 12, 2024NewsroomRansomware / Endpoint Security Threat actors linked to the Black Basta ransomware may have exploited a recently disclosed privilege escalation flaw in the Microsoft Windows Error Reporting Service as zero-day, according to new findings from Symantec. The security flaw in question is CVE-2024-26169 (CVSS score: 7.8), an elevation of privilege bug in the…
Read MoreLast week, the notorious hacker gang, ShinyHunters, sent shockwaves across the globe by allegedly plundering 1.3 terabytes of data from 560 million Ticketmaster users. This colossal breach, with a price tag of $500,000, could expose the personal information of a massive swath of the live event company’s clientele, igniting a firestorm of concern and outrage.…
Read MoreJun 12, 2024Newsroom State-sponsored threat actors backed by China gained access to 20,000 Fortinet FortiGate systems worldwide by exploiting a known critical security flaw between 2022 and 2023, indicating that the operation had a broader impact than previously known. “The state actor behind this campaign was already aware of this vulnerability in FortiGate systems at…
Read MoreJun 12, 2024NewsroomCyber Attack / Malware Cybersecurity researchers have disclosed details of an ongoing phishing campaign that leverages recruiting- and job-themed lures to deliver a Windows-based backdoor named WARMCOOKIE. “WARMCOOKIE appears to be an initial backdoor tool used to scout out victim networks and deploy additional payloads,” Elastic Security Labs researcher Daniel Stepanic said in…
Read MoreJun 12, 2024NewsroomPatch Tuesday / Vulnerability Microsoft has released security updates to address 51 flaws as part of its Patch Tuesday updates for June 2024. Of the 51 vulnerabilities, one is rated Critical and 50 are rated Important. This is in addition to 17 vulnerabilities resolved in the Chromium-based Edge browser over the past month.…
Read MoreOne of the most effective ways for information technology (IT) professionals to uncover a company’s weaknesses before the bad guys do is penetration testing. By simulating real-world cyberattacks, penetration testing, sometimes called pentests, provides invaluable insights into an organization’s security posture, revealing weaknesses that could potentially lead to data breaches or other security incidents. Vonahi…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm