Tag: cyber news
Introduction The infamous Colonial pipeline ransomware attack (2021) and SolarWinds supply chain attack (2020) were more than data leaks; they were seismic shifts in cybersecurity. These attacks exposed a critical challenge for Chief Information Security Officers (CISOs): holding their ground while maintaining control over cloud security in the accelerating world of DevOps. The problem was…
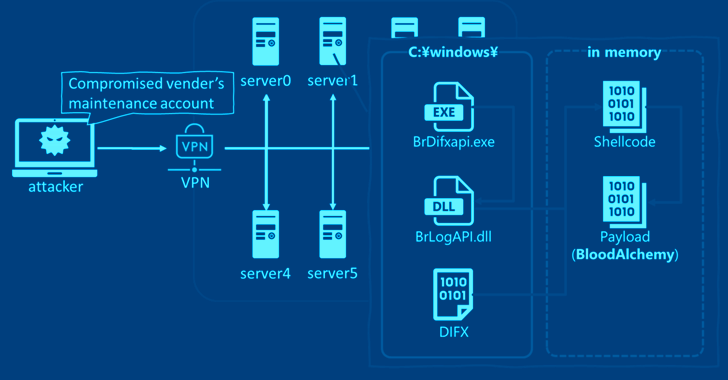
Read MoreMay 24, 2024NewsroomAPT Malware / Cyber Espionage Cybersecurity researchers have discovered that the malware known as BLOODALCHEMY used in attacks targeting government organizations in Southern and Southeastern Asia is in fact an updated version of Deed RAT, which is believed to be a successor to ShadowPad. “The origin of BLOODALCHEMY and Deed RAT is ShadowPad…
Read MoreMay 24, 2024NewsroomSupply Chain Attack / Malware Malicious actors have backdoored the installer associated with courtroom video recording software developed by Justice AV Solutions (JAVS) to deliver malware that’s associated with a known backdoor called RustDoor. The software supply chain attack, tracked as CVE-2024-4978, impacts JAVS Viewer v8.3.7, a component of the JAVS Suite 8…
Read MoreMay 23, 2024NewsroomThreat Intelligence / Vulnerability, The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a security flaw impacting Apache Flink, the open-source, unified stream-processing and batch-processing framework, to the Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. Tracked as CVE-2020-17519, the issue relates to a case of improper access control…
Read MoreMay 23, 2024NewsroomRansomware / Virtualization Ransomware attacks targeting VMware ESXi infrastructure following an established pattern regardless of the file-encrypting malware deployed. “Virtualization platforms are a core component of organizational IT infrastructure, yet they often suffer from inherent misconfigurations and vulnerabilities, making them a lucrative and highly effective target for threat actors to abuse,” cybersecurity firm…
Read MoreMay 23, 2024NewsroomCyber Espionage / Network Security The China-linked threat actor known as Sharp Panda has expanded their targeting to include governmental organizations in Africa and the Caribbean as part of an ongoing cyber espionage campaign. “The campaign adopts Cobalt Strike Beacon as the payload, enabling backdoor functionalities like C2 communication and command execution while…
Read MoreConversations about data security tend to diverge into three main threads: How can we protect the data we store on our on-premises or cloud infrastructure? What strategies and tools or platforms can reliably backup and restore data? What would losing all this data cost us, and how quickly could we get it back? All are…
Read MoreMay 23, 2024NewsroomCyber Espionage / Network Security Governmental entities in the Middle East, Africa, and Asia are the target of a Chinese advanced persistent threat (APT) group as part of an ongoing cyber espionage campaign dubbed Operation Diplomatic Specter since at least late 2022. “An analysis of this threat actor’s activity reveals long-term espionage operations…
Read MoreMay 23, 2024NewsroomEndpoint Security / Vulnerability Ivanti on Tuesday rolled out fixes to address multiple critical security flaws in Endpoint Manager (EPM) that could be exploited to achieve remote code execution under certain circumstances. Six of the 10 vulnerabilities – from CVE-2024-29822 through CVE-2024-29827 (CVSS scores: 9.6) – relate to SQL injection flaws that allow…
Read MoreFile Integrity Monitoring (FIM) is an IT security control that monitors and detects file changes in computer systems. It helps organizations audit important files and system configurations by routinely scanning and verifying their integrity. Most information security standards mandate the use of FIM for businesses to ensure the integrity of their data. IT security compliance…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm