Tag: cyber security news today
Jul 05, 2024NewsroomSEO Poisoning / Cyber Attack, The malware known as GootLoader continues to be in active use by threat actors looking to deliver additional payloads to compromised hosts. “Updates to the GootLoader payload have resulted in several versions of GootLoader, with GootLoader 3 currently in active use,” cybersecurity firm Cybereason said in an analysis…
Read MoreJul 05, 2024NewsroomSupply Chain Attack / Malware The supply chain attack targeting widely-used Polyfill[.]io JavaScript library is wider in scope than previously thought, with new findings from Censys showing that over 380,000 hosts are embedding a polyfill script linking to the malicious domain as of July 2, 2024. This includes references to “https://cdn.polyfill[.]io” or “https://cdn.polyfill[.]com”…
Read MoreJul 05, 2024NewsroomNetwork Security / Cyber Attack Cybersecurity researchers have uncovered a new botnet called Zergeca that’s capable of conducting distributed denial-of-service (DDoS) attacks. Written in Golang, the botnet is so named for its reference to a string named “ootheca” present in the command-and-control (C2) servers (“ootheca[.]pw” and “ootheca[.]top”). “Functionally, Zergeca is not just a…
Read MoreJul 04, 2024NewsroomVulnerability / Critical Infrastructure Microsoft has revealed two security flaws in Rockwell Automation PanelView Plus that could be weaponized by remote, unauthenticated attackers to execute arbitrary code and trigger a denial-of-service (DoS) condition. “The [remote code execution] vulnerability in PanelView Plus involves two custom classes that can be abused to upload and load…
Read MoreJul 04, 2024NewsroomArtificial Intelligence / Data Privacy Brazil’s data protection authority, Autoridade Nacional de Proteção de Dados (ANPD), has temporarily banned Meta from processing users’ personal data to train the company’s artificial intelligence (AI) algorithms. The ANPD said it found “evidence of processing of personal data based on inadequate legal hypothesis, lack of transparency, limitation…
Read MoreA coordinated law enforcement operation codenamed MORPHEUS has felled close to 600 servers that were used by cybercriminal groups and were part of an attack infrastructure associated with the Cobalt Strike. The crackdown targeted older, unlicensed versions of the Cobalt Strike red teaming framework between June 24 and 28, according to Europol. Of the 690…
Read MoreJul 04, 2024NewsroomData Breach / Mobile Security Cloud communications provider Twilio has revealed that unidentified threat actors took advantage of an unauthenticated endpoint in Authy to identify data associated with Authy accounts, including users’ cell phone numbers. The company said it took steps to secure the endpoint to no longer accept unauthenticated requests. The development…
Read MoreJul 03, 2024The Hacker NewsOSINT / Artificial Intelligence Recently the Office of the Director of National Intelligence (ODNI) unveiled a new strategy for open-source intelligence (OSINT) and referred to OSINT as the “INT of first resort”. Public and private sector organizations are realizing the value that the discipline can provide but are also finding that…
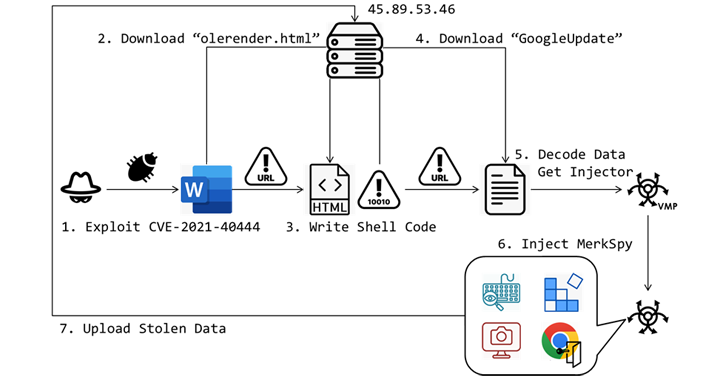
Read MoreJul 03, 2024NewsroomSpyware / Vulnerability Unknown threat actors have been observed exploiting a now-patched security flaw in Microsoft MSHTML to deliver a surveillance tool called MerkSpy as part of a campaign primarily targeting users in Canada, India, Poland, and the U.S. “MerkSpy is designed to clandestinely monitor user activities, capture sensitive information, and establish persistence…
Read MoreJul 03, 2024NewsroomMalware / SEO Poisoning The loader-as-a-service (LaaS) known as FakeBat has become one of the most widespread loader malware families distributed using the drive-by download technique this year, findings from Sekoia reveal. “FakeBat primarily aims to download and execute the next-stage payload, such as IcedID, Lumma, RedLine, SmokeLoader, SectopRAT, and Ursnif,” the company…
Read MoreRecent Posts
- Broadcom Names New Channel Chief, Sales Leader: 5 Big Things To Know
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking

![Polyfill[.]io Attack Impacts Over 380,000 Hosts, Including Major Companies](https://kartwheelnewz.info/wp-content/uploads/2024/07/Polyfillio-Attack-Impacts-Over-380000-Hosts-Including-Major-Companies.png)