Tag: cyber security news today
Jun 14, 2024The Hacker News Data is growing faster than ever. Remember when petabytes (that’s 1,000,000 gigabytes!) were only for tech giants? Well, that’s so last decade! Today, businesses of all sizes are swimming in petabytes. But this isn’t just about storage anymore. This data is ALIVE—it’s constantly accessed, analyzed, shared, and even used to…
Read MoreJun 14, 2024The Hacker NewsCybersecurity / Regulatory Compliance As cyber threats loom large and data breaches continue to pose increasingly significant risks. Organizations and industries that handle sensitive information and valuable assets make prime targets for cybercriminals seeking financial gain or strategic advantage. Which is why many highly regulated sectors, from finance to utilities, are…
Read MoreJun 14, 2024NewsroomDevice Security / Authentication An analysis of a hybrid biometric access system from Chinese manufacturer ZKTeco has uncovered two dozen security flaws that could be used by attackers to defeat authentication, steal biometric data, and even deploy malicious backdoors. “By adding random user data to the database or using a fake QR code,…
Read MoreThreat actors linked to North Korea have accounted for one-third of all the phishing activity targeting Brazil since 2020, as the country’s emergence as an influential power has drawn the attention of cyber espionage groups. “North Korean government-backed actors have targeted the Brazilian government and Brazil’s aerospace, technology, and financial services sectors,” Google’s Mandiant and…
Read MoreJun 14, 2024NewsroomArtificial Intelligence / Data Protection Microsoft on Thursday revealed that it’s delaying the rollout of the controversial artificial intelligence (AI)-powered Recall feature for Copilot+ PCs. To that end, the company said it intends to shift from general availability preview available first in the Windows Insider Program (WIP) in the coming weeks. “We are…
Read MoreJun 13, 2024NewsroomThreat Intelligence / Mobile Security The threat actor known as Arid Viper has been attributed to a mobile espionage campaign that leverages trojanized Android apps to deliver a spyware strain dubbed AridSpy. “The malware is distributed through dedicated websites impersonating various messaging apps, a job opportunity app, and a Palestinian Civil Registry app,”…
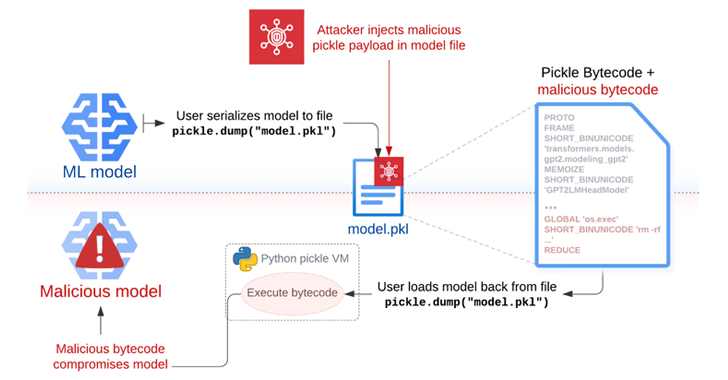
Read MoreJun 13, 2024NewsroomVulnerability / Software Security The security risks posed by the Pickle format have once again come to the fore with the discovery of a new “hybrid machine learning (ML) model exploitation technique” dubbed Sleepy Pickle. The attack method, per Trail of Bits, weaponizes the ubiquitous format used to package and distribute machine learning…
Read MoreJun 13, 2024NewsroomSaaS Security / Shadow IT Recent supply chain cyber-attacks are prompting cyber security regulations in the financial sector to tighten compliance requirements, and other industries are expected to follow. Many companies still don’t have efficient methods to manage related time-sensitive SaaS security and compliance tasks. Free SaaS risk assessment tools are an easy…
Read MoreJun 13, 2024NewsroomMalware / Cyber Attack The nascent malware known as SSLoad is being delivered by means of a previously undocumented loader called PhantomLoader, according to findings from cybersecurity firm Intezer. “The loader is added to a legitimate DLL, usually EDR or AV products, by binary patching the file and employing self-modifying techniques to evade…
Read MoreJun 13, 2024NewsroomThreat Intelligence / Cyber Attack Threat actors with ties to Pakistan have been linked to a long-running malware campaign dubbed Operation Celestial Force since at least 2018. The activity, still ongoing, entails the use of an Android malware called GravityRAT and a Windows-based malware loader codenamed HeavyLift, according to Cisco Talos, which are…
Read MoreRecent Posts
- Safeguarding Healthcare Organizations from IoMT Risks
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks