Tag: cyber security news
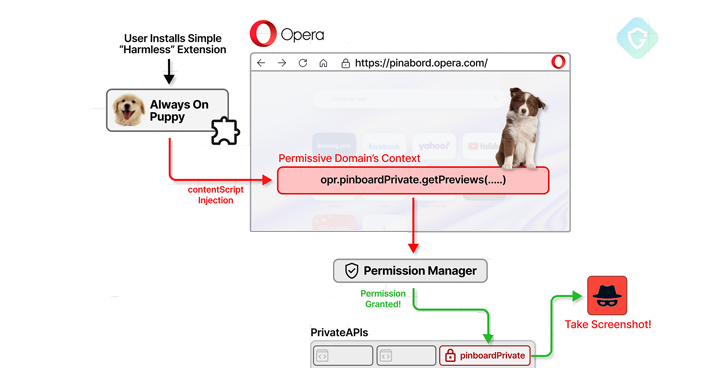
Oct 30, 2024Ravie Lakshmanan Browser Security / Vulnerability A now-patched security flaw in the Opera web browser could have enabled a malicious extension to gain unauthorized, full access to private APIs. The attack, codenamed CrossBarking, could have made it possible to conduct actions such as capturing screenshots, modifying browser settings, and account hijacking, Guardio Labs…
Read MoreOct 30, 2024The Hacker NewsVulnerability / Compliance Navigating the complexities of compliance frameworks like ISO 27001, SOC 2, or GDPR can be daunting. Luckily, Intruder simplifies the process by helping you address the key vulnerability management criteria these frameworks demand, making your compliance journey much smoother. Read on to understand how to meet the requirements…
Read MoreOct 30, 2024Ravie LakshmananCybercrim / Cryptocurrency Cybersecurity researchers have discovered a new malicious Python package that masquerades as a cryptocurrency trading tool but harbors functionality designed to steal sensitive data and drain assets from victims’ crypto wallets. The package, named “CryptoAITools,” is said to have been distributed via both Python Package Index (PyPI) and bogus…
Read MoreOct 29, 2024Ravie LakshmananAI Security / Vulnerability A little over three dozen security vulnerabilities have been disclosed in various open-source artificial intelligence (AI) and machine learning (ML) models, some of which could lead to remote code execution and information theft. The flaws, identified in tools like ChuanhuChatGPT, Lunary, and LocalAI, have been reported as part…
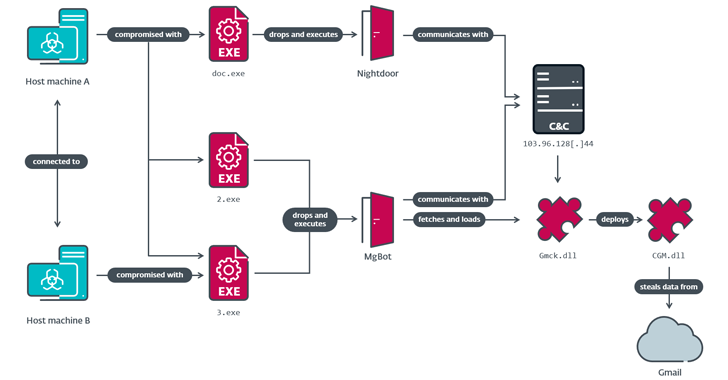
Read MoreOct 29, 2024Ravie LakshmananCybercrime / Malware The Dutch National Police, along with international partners, have announced the disruption of the infrastructure powering two information stealers tracked as RedLine and MetaStealer. The takedown, which took place on October 28, 2024, is the result of an international law enforcement task force codenamed Operation Magnus that involved authorities…
Read MoreA Sherlock Holmes Approach to Cybersecurity: Eliminate the Impossible with Exposure Validation
by nlqip
Sherlock Holmes is famous for his incredible ability to sort through mounds of information; he removes the irrelevant and exposes the hidden truth. His philosophy is plain yet brilliant: “When you have eliminated the impossible, whatever remains, however improbable, must be the truth.” Rather than following every lead, Holmes focuses on the details that are…
Read MoreOct 29, 2024Ravie LakshmananDigital Security / Data Privacy The U.S. government (USG) has issued new guidance governing the use of the Traffic Light Protocol (TLP) to handle the threat intelligence information shared between the private sector, individual researchers, and Federal Departments and Agencies. “The USG follows TLP markings on cybersecurity information voluntarily shared by an…
Read MoreOct 29, 2024Ravie LakshmananHardware Security / Vulnerability More than six years after the Spectre security flaw impacting modern CPU processors came to light, new research has found that the latest AMD and Intel processors are still susceptible to speculative execution attacks. The attack, disclosed by ETH Zürich researchers Johannes Wikner and Kaveh Razavi, aims to…
Read MoreOct 28, 2024Ravie LakshmananCloud Security / Cyber Attack A government entity and a religious organization in Taiwan were the target of a China-linked threat actor known as Evasive Panda that infected them with a previously undocumented post-compromise toolset codenamed CloudScout. “The CloudScout toolset is capable of retrieving data from various cloud services by leveraging stolen…
Read MoreOct 28, 2024Ravie LakshmananMalware / Threat Intelligence Three malicious packages published to the npm registry in September 2024 have been found to contain a known malware called BeaverTail, a JavaScript downloader and information stealer linked to an ongoing North Korean campaign tracked as Contagious Interview. The Datadog Security Research team is monitoring the activity under…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA