Tag: cyber updates
The current SOC model relies on a scarce resource: human analysts. These professionals are expensive, in high demand, and increasingly difficult to retain. Their work is not only highly technical and high-risk, but also soul-crushingly repetitive, dealing with a constant flood of alerts and incidents. As a result, SOC analysts often leave in search of…
Read MoreOct 10, 2024Ravie LakshmananCybercrime / Malware Cybersecurity researchers have shed light on a new digital skimmer campaign that leverages Unicode obfuscation techniques to conceal a skimmer dubbed Mongolian Skimmer. “At first glance, the thing that stood out was the script’s obfuscation, which seemed a bit bizarre because of all the accented characters,” Jscrambler researchers said…
Read MoreOct 10, 2024Ravie LakshmananVulnerability / Network Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added a critical security flaw impacting Fortinet products to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The vulnerability, tracked as CVE-2024-23113 (CVSS score: 9.8), relates to cases of remote code execution that affects FortiOS,…
Read MoreOct 10, 2024Ravie LakshmananVulnerability / Browser Security Mozilla has revealed that a critical security flaw impacting Firefox and Firefox Extended Support Release (ESR) has come under active exploitation in the wild. The vulnerability, tracked as CVE-2024-9680, has been described as a use-after-free bug in the Animation timeline component. “An attacker was able to achieve code…
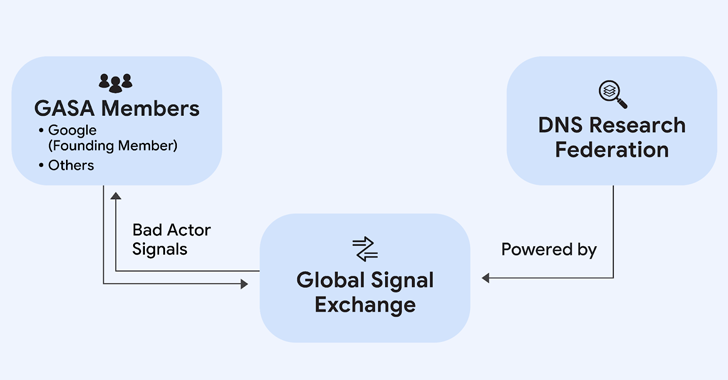
Read MoreOct 09, 2024Ravie LakshmananCybercrime / Threat Detection Google on Wednesday announced a new partnership with the Global Anti-Scam Alliance (GASA) and DNS Research Federation (DNS RF) to combat online scams. The initiative, which has been codenamed the Global Signal Exchange (GSE), is designed to create real-time insights into scams, fraud, and other forms of cybercrime…
Read MoreOct 09, 2024Ravie LakshmananIndustrial Security / Critical Infrastructure Details have emerged about multiple security vulnerabilities in two implementations of the Manufacturing Message Specification (MMS) protocol that, if successfully exploited, could have severe impacts in industrial environments. “The vulnerabilities could allow an attacker to crash an industrial device or in some cases, enable remote code execution,”…
Read MoreOct 09, 2024Ravie LakshmananPhishing Attack / Malware Threat actors with ties to North Korea have been observed targeting job seekers in the tech industry to deliver updated versions of known malware families tracked as BeaverTail and InvisibleFerret. The activity cluster, tracked as CL-STA-0240, is part of a campaign dubbed Contagious Interview that Palo Alto Networks…
Read MoreOct 09, 2024The Hacker NewsSaaS Security / Identity Security Social media accounts help shape a brand’s identity and reputation. These public forums engage directly with customers as they are a hub to connect, share content and answer questions. However, despite the high profile role these accounts have, many organizations overlook social media account security. Many…
Read MoreOct 09, 2024Ravie LakshmananVulnerability / Zero-Day Microsoft has released security updates to fix a total of 118 vulnerabilities across its software portfolio, two of which have come under active exploitation in the wild. Of the 118 flaws, three are rated Critical, 113 are rated Important, and two are rated Moderate in severity. The Patch Tuesday…
Read MoreMicrosoft Detects Growing Use of File Hosting Services in Business Email Compromise Attacks
by nlqip
Oct 09, 2024Ravie LakshmananEnterprise Security / Identity Theft Microsoft is warning of cyber attack campaigns that abuse legitimate file hosting services such as SharePoint, OneDrive, and Dropbox that are widely used in enterprise environments as a defense evasion tactic. The end goal of the campaigns are broad and varied, allowing threat actors to compromise identities…
Read More