Tag: Cybersecurity
The content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. Cloud computing has become a boon to organizations due to its flexibility, scalability, and cost-effectiveness. However, without proper oversight, it evolves into an…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. From stolen personal data to entire corporate databases, Raid Forums was a digital black market where the most valuable commodities weren’t physical goods…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. As we gear up to celebrate Internet Day on October 29th, let’s take a moment to appreciate how much the Internet has revolutionized…
Read MoreWhen you think of a cyberattack, you probably envision a sophisticated hacker behind a Matrix-esque screen actively penetrating networks with their technical prowess. However, the reality of many attacks is far more mundane. A simple email with an innocent subject line such as “Missed delivery attempt” sits in an employee’s spam folder. They open it…
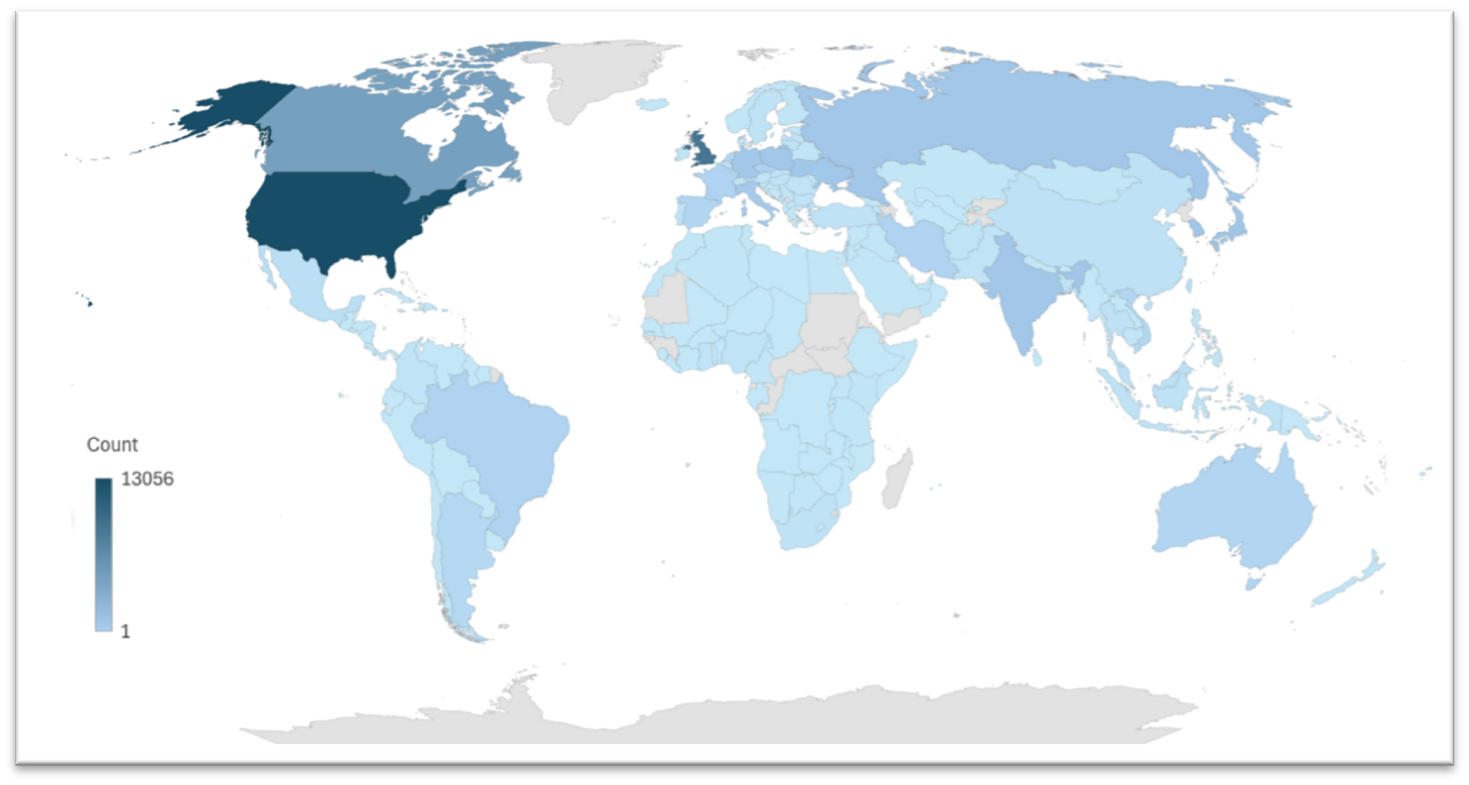
Read MoreExecutive Summary Seven years after its first appearance, the proxy server botnet Ngioweb continues its impactful presence on the internet with barely any relevant changes in its original code. Threat actors have continued to actively use Nbioweb extensively to scan for vulnerable devices (including a new arsenal of exploits) which can be turned into new…
Read MoreMarks, who was most recently vice president of global channels at SentinelOne, tells CRN that he sees a ‘tremendous’ opportunity ahead for MSP and MSSP partners working with the cybersecurity vendor. Cynomi, an MSP-focused startup whose vCISO platform is tailored toward securing small and medium-sized enterprises, announced Tuesday it has hired a veteran of the…
Read MoreThe provider of power management technologies confirmed that a developer platform was impacted by ‘unauthorized access.’ Schneider Electric confirmed Monday that a developer platform used by the company was impacted by a “cybersecurity incident” that is now under investigation. According to a BleepingComputer report, a threat actor has claimed, during a conversation with the media…
Read MoreCRN showcases the hottest 100 edge computing companies, including the top 25 cybersecurity companies, 25 IoT and 5G vendors, and 50 hardware, software and services edge companies. Companies at the forefront of the global edge computing market range from cloud giants and cybersecurity superstars to hybrid work specialists and AI startups. With market research firm…
Read MoreCRN’s list of the 50 hottest hardware, software and services companies in edge computing this year ranges from innovative startups like Reskube to edge specialists such as Scale Computing to market leaders like Cisco Systems, Dell Technologies and Microsoft. Today’s innovative software and hardware companies continue to invest in edge computing technologies in 2024 as…
Read MoreFor the week ending Nov. 1, CRN takes a look at the companies that brought their ‘A’ game to the channel including Cisco Systems, Blue Mantis, Kaseya, ATSG, Evolve IP, and Siemens. The Week Ending Nov. 1 Topping this week’s Came to Win list is Cisco Systems with the launch of Cisco 360, the company’s…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA