Tag: data breach
Mar 14, 2024NewsroomCyber Threat / Malware The threat actor known as Blind Eagle has been observed using a loader malware called Ande Loader to deliver remote access trojans (RATs) like Remcos RAT and NjRAT. The attacks, which take the form of phishing emails, targeted Spanish-speaking users in the manufacturing industry based in North America, eSentire…
Read MoreMar 14, 2024The Hacker NewsVulnerability / Network Security Fortinet has warned of a critical security flaw impacting its FortiClientEMS software that could allow attackers to achieve code execution on affected systems. “An improper neutralization of special elements used in an SQL Command (‘SQL Injection’) vulnerability [CWE-89] in FortiClientEMS may allow an unauthenticated attacker to execute…
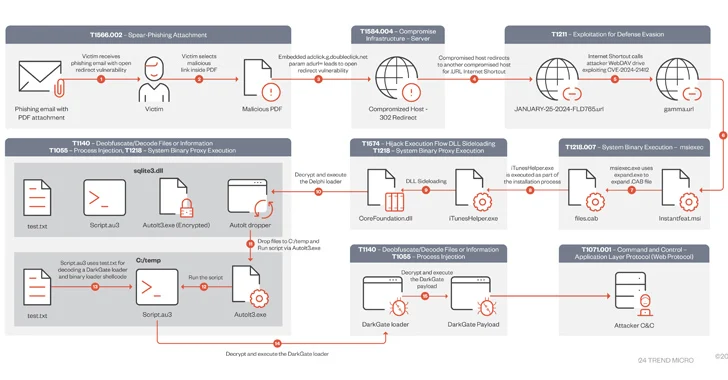
Read MoreMar 14, 2024NewsroomMalware / Cyber Attack A DarkGate malware campaign observed in mid-January 2024 leveraged a recently patched security flaw in Microsoft Windows as a zero-day using bogus software installers. “During this campaign, users were lured using PDFs that contained Google DoubleClick Digital Marketing (DDM) open redirects that led unsuspecting victims to compromised sites hosting…
Read MoreMar 13, 2024The Hacker NewsApp Security / Cyber Security One of the most common misconceptions in file upload cybersecurity is that certain tools are “enough” on their own—this is simply not the case. In our latest whitepaper OPSWAT CEO and Founder, Benny Czarny, takes a comprehensive look at what it takes to prevent malware threats…
Read MoreMar 13, 2024The Hacker NewsFinancial Fraud / Mobile Security The threat actors behind the PixPirate Android banking trojan are leveraging a new trick to evade detection on compromised devices and harvest sensitive information from users in Brazil. The approach allows it to hide the malicious app’s icon from the home screen of the victim’s device,…
Read MoreMar 13, 2024NewsroomLarge Language Model / AI Security Google’s Gemini large language model (LLM) is susceptible to security threats that could cause it to divulge system prompts, generate harmful content, and carry out indirect injection attacks. The findings come from HiddenLayer, which said the issues impact consumers using Gemini Advanced with Google Workspace as well…
Read MoreMar 13, 2024The Hacker NewsSaaS Security / Webinar Identities are the latest sweet spot for cybercriminals, now heavily targeting SaaS applications that are especially vulnerable in this attack vector. The use of SaaS applications involves a wide range of identities, including human and non-human, such as service accounts, API keys, and OAuth authorizations. Consequently, any…
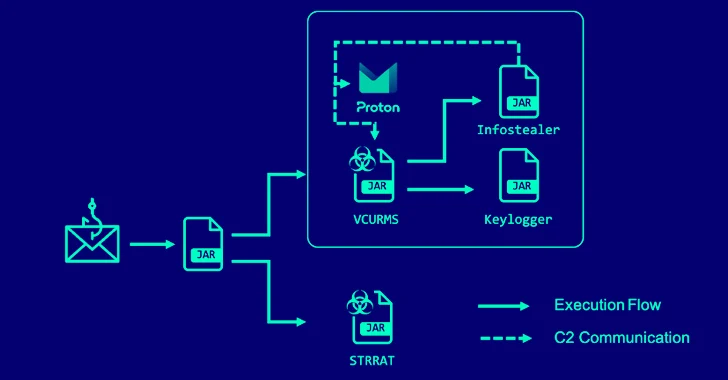
Read MoreMar 13, 2024NewsroomPhishing Attack / Threat Intelligence A new phishing campaign has been observed delivering remote access trojans (RAT) such as VCURMS and STRRAT by means of a malicious Java-based downloader. “The attackers stored malware on public services like Amazon Web Services (AWS) and GitHub, employing a commercial protector to avoid detection of the malware,”…
Read MoreMar 13, 2024NewsroomPatch Tuesday / Software Update Microsoft on Tuesday released its monthly security update, addressing 61 different security flaws spanning its software, including two critical issues impacting Windows Hyper-V that could lead to denial-of-service (DoS) and remote code execution. Of the 61 vulnerabilities, two are rated Critical, 58 are rated Important, and one is…
Read MoreMar 12, 2024The Hacker NewsCryptocurrency / Cybercrime Threat hunters have discovered a set of seven packages on the Python Package Index (PyPI) repository that are designed to steal BIP39 mnemonic phrases used for recovering private keys of a cryptocurrency wallet. The software supply chain attack campaign has been codenamed BIPClip by ReversingLabs. The packages were…
Read MoreRecent Posts
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
- QNAP pulls buggy QTS firmware causing widespread NAS issues
- N-able Exec: ‘Cybersecurity And Compliance Are A Team Sport’
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’