Tag: how to hack
Mar 22, 2024NewsroomAmazon Web Services / Vulnerability Cybersecurity researchers have shared details of a now-patched security vulnerability in Amazon Web Services (AWS) Managed Workflows for Apache Airflow (MWAA) that could be potentially exploited by a malicious actor to hijack victims’ sessions and achieve remote code execution on underlying instances. The vulnerability, now addressed by AWS,…
Read MoreThe ThreatLocker® Zero Trust Endpoint Protection Platform implements a strict deny-by-default, allow-by-exception security posture to give organizations the ability to set policy-based controls within their environment and mitigate countless cyber threats, including zero-days, unseen network footholds, and malware attacks as a direct result of user error. With the capabilities of the ThreatLocker® Zero Trust Endpoint…
Read MoreMar 22, 2024NewsroomPrivacy / Encryption The U.S. Department of Justice (DoJ), along with 16 other state and district attorneys general, on Thursday accused Apple of illegally maintaining a monopoly over smartphones, thereby undermining, among others, security and privacy of users when messaging non-iPhone users. “Apple wraps itself in a cloak of privacy, security, and consumer…
Read MoreMar 22, 2024NewsroomLinux / Cyber Warfare The data wiping malware called AcidPour may have been deployed in attacks targeting four telecom providers in Ukraine, new findings from SentinelOne show. The cybersecurity firm also confirmed connections between the malware and AcidRain, tying it to threat activity clusters associated with Russian military intelligence. “AcidPour’s expanded capabilities would…
Read MoreMar 21, 2024NewsroomThreat Intelligence / Malware The Russia-linked threat actor known as Turla infected several systems belonging to an unnamed European non-governmental organization (NGO) in order to deploy a backdoor called TinyTurla-NG. “The attackers compromised the first system, established persistence and added exclusions to antivirus products running on these endpoints as part of their preliminary…
Read MoreMar 21, 2024NewsroomSoftware Security / Open Source New research has discovered over 800 packages in the npm registry which have discrepancies from their registry entries, out of which 18 have been found to exploit a technique called manifest confusion. The findings come from cybersecurity firm JFrog, which said the issue could be exploited by threat…
Read MoreMar 21, 2024NewsroomThreat Intelligence / Vulnerability Cybersecurity researchers have shed light on a tool referred to as AndroxGh0st that’s used to target Laravel applications and steal sensitive data. “It works by scanning and taking out important information from .env files, revealing login details linked to AWS and Twilio,” Juniper Threat Labs researcher Kashinath T Pattan…
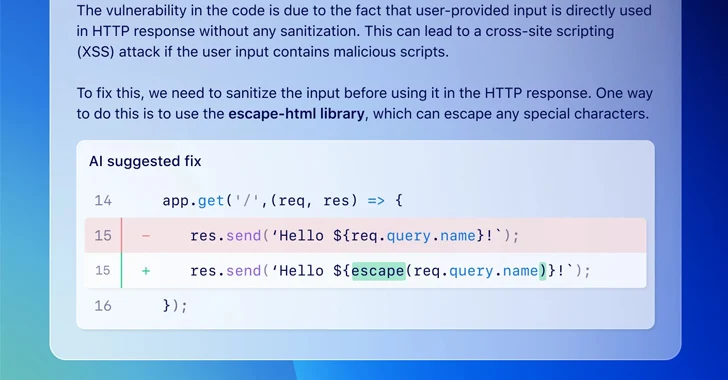
Read MoreMar 21, 2024NewsroomMachine Learning / Software Security GitHub on Wednesday announced that it’s making available a feature called code scanning autofix in public beta for all Advanced Security customers to provide targeted recommendations in an effort to avoid introducing new security issues. “Powered by GitHub Copilot and CodeQL, code scanning autofix covers more than 90%…
Read MoreIn today’s digital-first business environment dominated by SaaS applications, organizations increasingly depend on third-party vendors for essential cloud services and software solutions. As more vendors and services are added to the mix, the complexity and potential vulnerabilities within the SaaS supply chain snowball quickly. That’s why effective vendor risk management (VRM) is a critical strategy…
Read MoreWhen you read reports about cyber-attacks affecting operational technology (OT), it’s easy to get caught up in the hype and assume every single one is sophisticated. But are OT environments all over the world really besieged by a constant barrage of complex cyber-attacks? Answering that would require breaking down the different types of OT cyber-attacks…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA