Tag: how to hack
May 15, 2024The Hacker NewsEnterprise Security / Cloud Computing While cloud adoption has been top of mind for many IT professionals for nearly a decade, it’s only in recent months, with industry changes and announcements from key players, that many recognize the time to make the move is now. It may feel like a daunting…
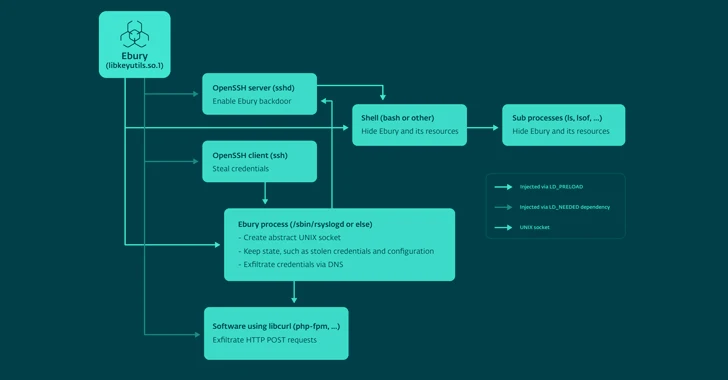
Read MoreA malware botnet called Ebury is estimated to have compromised 400,000 Linux servers since 2009, out of which more than 100,000 were still compromised as of late 2023. The findings come from Slovak cybersecurity firm ESET, which characterized it as one of the most advanced server-side malware campaigns for financial gain. “Ebury actors have been…
Read MoreMay 15, 2024NewsroomCryptocurrency / Anonymity A Dutch court on Tuesday sentenced one of the co-founders of the now-sanctioned Tornado Cash cryptocurrency mixer service to 5 years and 4 months in prison. While the name of the defendant was redacted in the verdict, it’s known that Alexey Pertsev, a 31-year-old Russian national, has been awaiting trial…
Read MoreMay 15, 2024NewsroomPatch Tuesday / Vulnerability Microsoft has addressed a total of 61 new security flaws in its software as part of its Patch Tuesday updates for May 2024, including two zero-days which have been actively exploited in the wild. Of the 61 flaws, one is rated Critical, 59 are rated Important, and one is…
Read MoreMay 14, 2024NewsroomBluetooth / Vulnerability Multiple security flaws have been disclosed in VMware Workstation and Fusion products that could be exploited by threat actors to access sensitive information, trigger a denial-of-service (DoS) condition, and execute code under certain circumstances. The four vulnerabilities impact Workstation versions 17.x and Fusion versions 13.x, with fixes available in version…
Read MoreMay 14, 2024NewsroomVulnerability / Zero Day Google on Monday shipped emergency fixes to address a new zero-day flaw in the Chrome web browser that has come under active exploitation in the wild. The high-severity vulnerability, tracked as CVE-2024-4761, is an out-of-bounds write bug impacting the V8 JavaScript and WebAssembly engine. It was reported anonymously on…
Read MoreMay 14, 2024NewsroomNetwork Monitoring / Vulnerability The maintainers of the Cacti open-source network monitoring and fault management framework have addressed a dozen security flaws, including two critical issues that could lead to the execution of arbitrary code. The most severe of the vulnerabilities are listed below – CVE-2024-25641 (CVSS score: 9.1) – An arbitrary file…
Read MoreCybersecurity researchers have uncovered an ongoing social engineering campaign that bombards enterprises with spam emails with the goal of obtaining initial access to their environments for follow-on exploitation. “The incident involves a threat actor overwhelming a user’s email with junk and calling the user, offering assistance,” Rapid7 researchers Tyler McGraw, Thomas Elkins, and Evan McCann…
Read MoreMay 14, 2024The Hacker NewsCyber Threat / Machine Learning Deploying advanced authentication measures is key to helping organizations address their weakest cybersecurity link: their human users. Having some form of 2-factor authentication in place is a great start, but many organizations may not yet be in that spot or have the needed level of authentication…
Read MoreApple and Google Launch Cross-Platform Feature to Detect Unwanted Bluetooth Tracking Devices
by nlqip
May 14, 2024NewsroomLocation Tracking / Privacy Apple and Google on Monday officially announced the rollout of a new feature that notifies users across both iOS and Android if a Bluetooth tracking device is being used to stealthily keep tabs on them without their knowledge or consent. “This will help mitigate the misuse of devices designed…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA