Tag: how to hack
May 03, 2024NewsroomVulnerability / Software Security HPE Aruba Networking (formerly Aruba Networks) has released security updates to address critical flaws impacting ArubaOS that could result in remote code execution (RCE) on affected systems. Of the 10 security defects, four are rated critical in severity – CVE-2024-26304 (CVSS score: 9.8) – Unauthenticated Buffer Overflow Vulnerability in…
Read MoreMay 02, 2024NewsroomVulnerability / Android Several popular Android applications available in Google Play Store are susceptible to a path traversal-affiliated vulnerability that could be exploited by a malicious app to overwrite arbitrary files in the vulnerable app’s home directory. “The implications of this vulnerability pattern include arbitrary code execution and token theft, depending on an…
Read MoreMay 02, 2024NewsroomRansomware / Cyber Crime A Ukrainian national has been sentenced to more than 13 years in prison and ordered to pay $16 million in restitution for carrying out thousands of ransomware attacks and extorting victims. Yaroslav Vasinskyi (aka Rabotnik), 24, along with his co-conspirators part of the REvil ransomware group orchestrated more than…
Read MoreA never-before-seen botnet called Goldoon has been observed targeting D-Link routers with a nearly decade-old critical security flaw with the goal of using the compromised devices for further attacks. The vulnerability in question is CVE-2015-2051 (CVSS score: 9.8), which affects D-Link DIR-645 routers and allows remote attackers to execute arbitrary commands by means of specially…
Read MoreMay 02, 2024NewsroomCyber Attack / Data Breach Cloud storage services provider Dropbox on Wednesday disclosed that Dropbox Sign (formerly HelloSign) was breached by unidentified threat actors, who accessed emails, usernames, and general account settings associated with all users of the digital signature product. The company, in a filing with the U.S. Securities and Exchange Commission…
Read MoreLike antivirus software, vulnerability scans rely on a database of known weaknesses. That’s why websites like VirusTotal exist, to give cyber practitioners a chance to see whether a malware sample is detected by multiple virus scanning engines, but this concept hasn’t existed in the vulnerability management space. The benefits of using multiple scanning engines Generally…
Read MoreMay 02, 2024NewsroomVulnerability / Data Breach The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical flaw impacting GitLab to its Known Exploited Vulnerabilities (KEV) catalog, owing to active exploitation in the wild. Tracked as CVE-2023-7028 (CVSS score: 10.0), the maximum severity vulnerability could facilitate account takeover by sending password reset emails to…
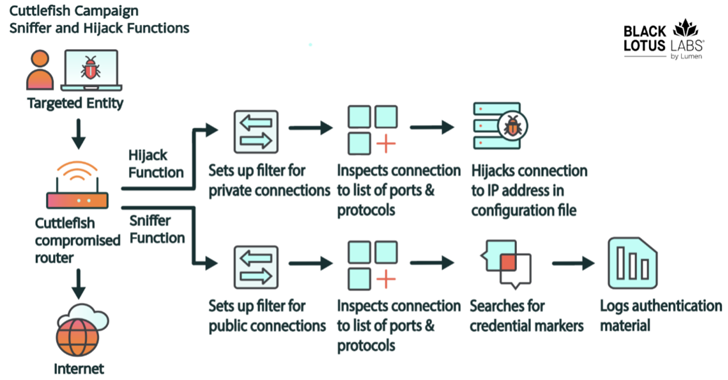
Read MoreMay 02, 2024NewsroomCyber Espionage / Network Security A new malware called Cuttlefish is targeting small office and home office (SOHO) routers with the goal of stealthily monitoring all traffic through the devices and gather authentication data from HTTP GET and POST requests. “This malware is modular, designed primarily to steal authentication material found in web…
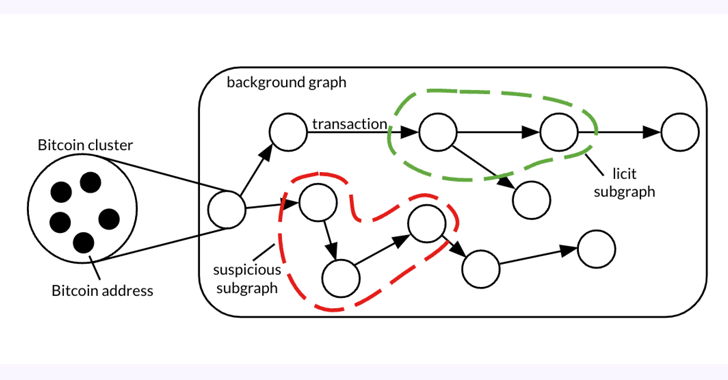
Read MoreMay 01, 2024NewsroomFinancial Crime / Forensic Analysis A forensic analysis of a graph dataset containing transactions on the Bitcoin blockchain has revealed clusters associated with illicit activity and money laundering, including detecting criminal proceeds sent to a crypto exchange and previously unknown wallets belonging to a Russian darknet market. The findings come from Elliptic in…
Read MoreMay 01, 2024NewsroomMalware / Android Cybersecurity researchers have discovered a previously undocumented malware targeting Android devices that uses compromised WordPress sites as relays for its actual command-and-control (C2) servers for detection evasion. The malware, codenamed Wpeeper, is an ELF binary that leverages the HTTPS protocol to secure its C2 communications. “Wpeeper is a typical backdoor…
Read MoreRecent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict