Tag: information security
In the digital realm, secrets (API keys, private keys, username and password combos, etc.) are the keys to the kingdom. But what if those keys were accidentally left out in the open in the very tools we use to collaborate every day? A Single Secret Can Wreak Havoc Imagine this: It’s a typical Tuesday in…
Read MoreEight vulnerabilities have been uncovered in Microsoft applications for macOS that an adversary could exploit to gain elevated privileges or access sensitive data by circumventing the operating system’s permissions-based model, which revolves around the Transparency, Consent, and Control (TCC) framework. “If successful, the adversary could gain any privileges already granted to the affected Microsoft applications,”…
Read MoreSep 03, 2024Ravie LakshmananInsider Threat / Network Security A 57-year-old man from the U.S. state of Missouri has been arrested in connection with a failed data extortion campaign that targeted his former employer. Daniel Rhyne of Kansas City, Missouri, has been charged with one count of extortion in relation to a threat to cause damage…
Read MoreThreat actors linked to the RansomHub ransomware group encrypted and exfiltrated data from at least 210 victims since its inception in February 2024, the U.S. government said. The victims span various sectors, including water and wastewater, information technology, government services and facilities, healthcare and public health, emergency services, food and agriculture, financial services, commercial facilities,…
Read MoreSep 02, 2024The Hacker NewsVulnerability Management / Webinar The world of cybersecurity is in a constant state of flux. New vulnerabilities emerge daily, and attackers are becoming more sophisticated. In this high-stakes game, security leaders need every advantage they can get. That’s where Artificial Intelligence (AI) comes in. AI isn’t just a buzzword; it’s a…
Read MoreSep 02, 2024The Hacker NewsCybercrime / CISO Insights The FBI and CISA Issue Joint Advisory on New Threats and How to Stop Ransomware Note: on August 29, the FBI and CISA issued a joint advisory as part of their ongoing #StopRansomware effort to help organizations protect against ransomware. The latest advisory, AA24-242A, describes a new…
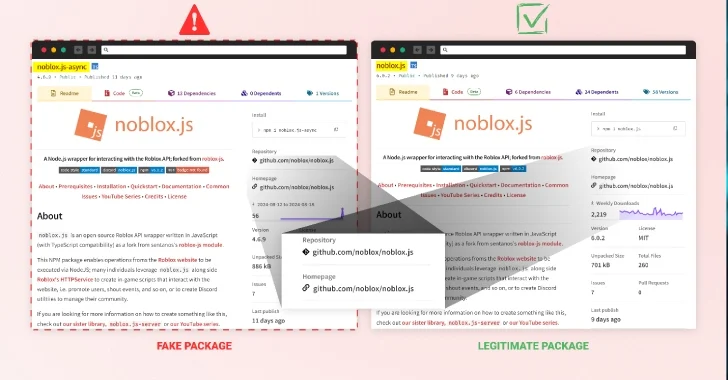
Read MoreSep 02, 2024Ravie LakshmananSoftware Security / Malware Roblox developers are the target of a persistent campaign that seeks to compromise systems through bogus npm packages, once again underscoring how threat actors continue to exploit the trust in the open-source ecosystem to deliver malware. “By mimicking the popular ‘noblox.js’ library, attackers have published dozens of packages…
Read MoreAug 31, 2024Ravie LakshmananRootkit / Threat Intelligence A recently patched security flaw in Google Chrome and other Chromium web browsers was exploited as a zero-day by North Korean actors in a campaign designed to deliver the FudModule rootkit. The development is indicative of the persistent efforts made by the nation-state adversary, which had made a…
Read MoreCybersecurity researchers have uncovered a novel malware campaign that leverages Google Sheets as a command-and-control (C2) mechanism. The activity, detected by Proofpoint starting August 5, 2024, impersonates tax authorities from governments in Europe, Asia, and the U.S., with the goal of targeting over 70 organizations worldwide by means of a bespoke tool called Voldemort that’s…
Read MoreAug 30, 2024Ravie LakshmananCyber Threat / Cyber Espionage Cybersecurity researchers have unearthed new network infrastructure set up by Iranian threat actors to support activities linked to the recent targeting of U.S. political campaigns. Recorded Future’s Insikt Group has linked the infrastructure to a threat it tracks as GreenCharlie, an Iran-nexus cyber threat group that overlaps…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm