Tag: network security
A new report from XM Cyber has found – among other insights – a dramatic gap between where most organizations focus their security efforts, and where the most serious threats actually reside. The new report, Navigating the Paths of Risk: The State of Exposure Management in 2024, is based on hundreds of thousands of attack…
Read MoreMay 17, 2024NewsroomLinux / Malware The Kimsuky (aka Springtail) advanced persistent threat (APT) group, which is linked to North Korea’s Reconnaissance General Bureau (RGB), has been observed deploying a Linux version of its GoBear backdoor as part of a campaign targeting South Korean organizations. The backdoor, codenamed Gomir, is “structurally almost identical to GoBear, with…
Read MoreMay 17, 2024NewsroomVulnerability / Network Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added two security flaws impacting D-Link routers to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The list of vulnerabilities is as follows – CVE-2014-100005 – A cross-site request forgery (CSRF) vulnerability impacting D-Link DIR-600…
Read MoreMay 16, 2024NewsroomVulnerability / Network Security Researchers have discovered a new security vulnerability stemming from a design flaw in the IEEE 802.11 Wi-Fi standard that tricks victims into connecting to a less secure wireless network and eavesdrop on their network traffic. The SSID Confusion attack, tracked as CVE-2023-52424, impacts all operating systems and Wi-Fi clients,…
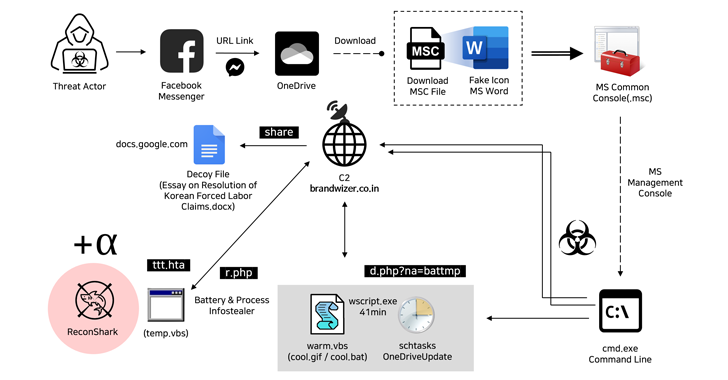
Read MoreMay 16, 2024NewsroomMalware / Cyber Espionage The North Korea-linked Kimsuky hacking group has been attributed to a new social engineering attack that employs fictitious Facebook accounts to targets via Messenger and ultimately delivers malware. “The threat actor created a Facebook account with a fake identity disguised as a public official working in the North Korean…
Read MoreSecurity researchers have disclosed almost a dozen security flaws impacting the GE HealthCare Vivid Ultrasound product family that could be exploited by malicious actors to tamper with patient data and even install ransomware under certain circumstances. “The impacts enabled by these flaws are manifold: from the implant of ransomware on the ultrasound machine to the…
Read MoreMay 16, 2024NewsroomBrowser Security / Vulnerability Google has rolled out fixes to address a set of nine security issues in its Chrome browser, including a new zero-day that has been exploited in the wild. Assigned the CVE identifier CVE-2024-4947, the vulnerability relates to a type confusion bug in the V8 JavaScript and WebAssembly engine. It…
Read MoreMay 16, 2024NewsroomRansomware / Incident Response The Microsoft Threat Intelligence team said it has observed a threat it tracks under the name Storm-1811 abusing the client management tool Quick Assist to target users in social engineering attacks. “Storm-1811 is a financially motivated cybercriminal group known to deploy Black Basta ransomware,” the company said in a…
Read More“We will deliver innovation at an unprecedented pace and scale to organizations around the globe,” Cisco CEO Chuck Robbins said on Wednesday’s earnings call. Cisco Systems CEO Chuck Robbins plans to leverage “Cisco’s robust partner and customer ecosystem in markets where Splunk had limited or no presence” to grow the business of his new security…
Read MoreCisco is “taking the next step” in making its 40-year-old GTM engine “one of most sophisticated and extensive,” Cisco CEO Chuck Robbins said in a blog post. Cisco has moved Gary Steele from the role of executive vice president and general manager of newly acquired cybersecurity subsidiary Splunk to a new role as president of…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm