Tag: network security
Apr 29, 2024NewsroomProgramming / Supply Chain A security vulnerability has been discovered in the R programming language that could be exploited by a threat actor to create a malicious RDS (R Data Serialization) file such that it results in code execution when loaded and referenced. The flaw, assigned the CVE identifier CVE-2024-27322, “involves the use…
Read MoreApr 29, 2024NewsroomDNS Security / Cyber Espionage A previously undocumented cyber threat dubbed Muddling Meerkat has been observed undertaking sophisticated domain name system (DNS) activities in a likely effort to evade security measures and conduct reconnaissance of networks across the world since October 2019. Cloud security firm Infoblox described the threat actor as likely affiliated…
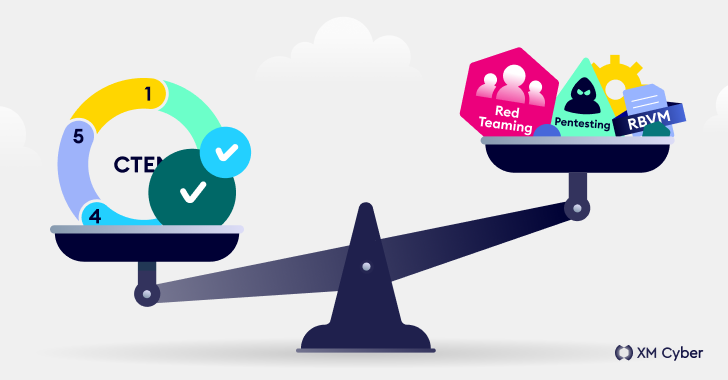
Read MoreNavigating the Threat Landscape: Understanding Exposure Management, Pentesting, Red Teaming and RBVM
by nlqip
It comes as no surprise that today’s cyber threats are orders of magnitude more complex than those of the past. And the ever-evolving tactics that attackers use demand the adoption of better, more holistic and consolidated ways to meet this non-stop challenge. Security teams constantly look for ways to reduce risk while improving security posture,…
Read MoreApr 29, 2024NewsroomSandbox / Vulnerability Multiple critical security flaws have been disclosed in the Judge0 open-source online code execution system that could be exploited to obtain code execution on the target system. The three flaws, all critical in nature, allow an “adversary with sufficient access to perform a sandbox escape and obtain root permissions on…
Read MoreApr 28, 2024NewsroomCredential Stuffing / Data Breach Identity and access management (IAM) services provider Okta has warned of a spike in the “frequency and scale” of credential stuffing attacks aimed at online services. These unprecedented attacks, observed over the last month, are said to be facilitated by “the broad availability of residential proxy services, lists…
Read MoreApr 27, 2024NewsroomCyber Attack / Malware Cybersecurity researchers have discovered a targeted operation against Ukraine that has been found leveraging a nearly seven-year-old flaw in Microsoft Office to deliver Cobalt Strike on compromised systems. The attack chain, which took place at the end of 2023 according to Deep Instinct, employs a PowerPoint slideshow file (“signal-2023-12-20-160512.ppsx”)…
Read MoreApr 27, 2024NewsroomMalware / Software Security An ongoing social engineering campaign is targeting software developers with bogus npm packages under the guise of a job interview to trick them into downloading a Python backdoor. Cybersecurity firm Securonix is tracking the activity under the name DEV#POPPER, linking it to North Korean threat actors. “During these fraudulent…
Read MoreApr 26, 2024NewsroomSupply Chain Attack / Software Security Several security vulnerabilities disclosed in Brocade SANnav storage area network (SAN) management application could be exploited to compromise susceptible appliances. The 18 flaws impact all versions up to and including 2.3.0, according to independent security researcher Pierre Barre, who discovered and reported them. The issues range from…
Read MoreApr 26, 2024NewsroomNetwork Security / Zero Day Palo Alto Networks has shared remediation guidance for a recently disclosed critical security flaw impacting PAN-OS that has come under active exploitation. The vulnerability, tracked as CVE-2024-3400 (CVSS score: 10.0), could be weaponized to obtain unauthenticated remote shell command execution on susceptible devices. It has been addressed in…
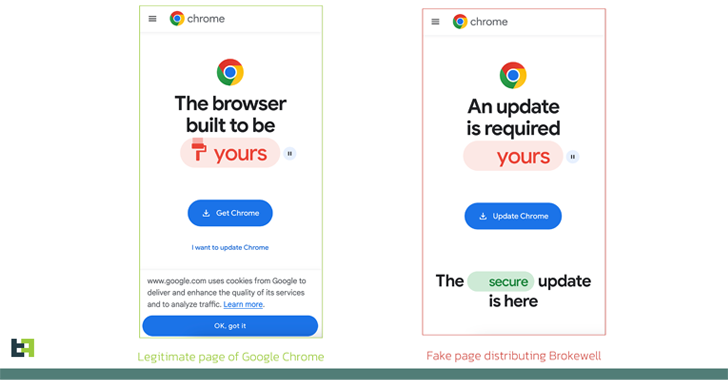
Read MoreApr 26, 2024NewsroomMobile Security / Cybercrime Fake browser updates are being used to push a previously undocumented Android malware called Brokewell. “Brokewell is a typical modern banking malware equipped with both data-stealing and remote-control capabilities built into the malware,” Dutch security firm ThreatFabric said in an analysis published Thursday. The malware is said to be…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm