Tag: network security
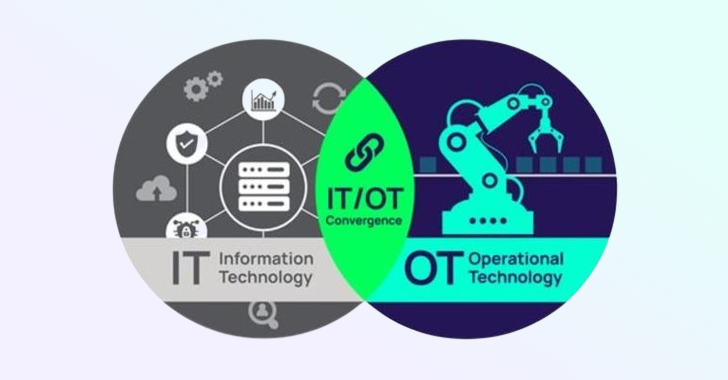
Operational Technology (OT) refers to the hardware and software used to change, monitor, or control the enterprise’s physical devices, processes, and events. Unlike traditional Information Technology (IT) systems, OT systems directly impact the physical world. This unique characteristic of OT brings additional cybersecurity considerations not typically present in conventional IT security architectures. The convergence of…
Read MoreApr 04, 2024NewsroomNetwork Security / Vulnerability Ivanti has released security updates to address four security flaws impacting Connect Secure and Policy Secure Gateways that could result in code execution and denial-of-service (DoS). The list of flaws is as follows – CVE-2024-21894 (CVSS score: 8.2) – A heap overflow vulnerability in the IPSec component of Ivanti…
Read MoreApr 03, 2024NewsroomMobile Security / Zero Day Google has disclosed that two Android security flaws impacting its Pixel smartphones have been exploited in the wild by forensic companies. The high-severity zero-day vulnerabilities are as follows – CVE-2024-29745 – An information disclosure flaw in the bootloader component CVE-2024-29748 – A privilege escalation flaw in the firmware…
Read MoreApr 03, 2024NewsroomData Breach / Incident Response The U.S. Cyber Safety Review Board (CSRB) has criticized Microsoft for a series of security lapses that led to the breach of nearly two dozen companies across Europe and the U.S. by a China-based nation-state group called Storm-0558 last year. The findings, released by the Department of Homeland…
Read MoreApr 03, 2024NewsroomBrowser Security / Session Hijacking Google on Tuesday said it’s piloting a new feature in Chrome called Device Bound Session Credentials (DBSC) to help protect users against session cookie theft by malware. The prototype – currently tested against “some” Google Account users running Chrome Beta – is built with an aim to make…
Read MoreApr 03, 2024The Hacker NewsCybersecurity / Penetration Testing Attack surface management (ASM) and vulnerability management (VM) are often confused, and while they overlap, they’re not the same. The main difference between attack surface management and vulnerability management is in their scope: vulnerability management checks a list of known assets, while attack surface management assumes you…
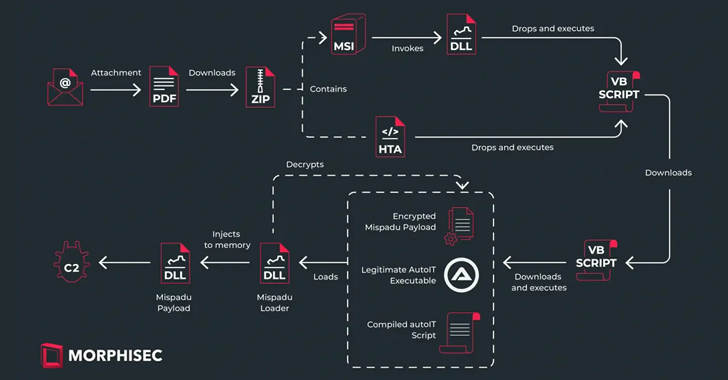
Read MoreThe banking trojan known as Mispadu has expanded its focus beyond Latin America (LATAM) and Spanish-speaking individuals to target users in Italy, Poland, and Sweden. Targets of the ongoing campaign include entities spanning finance, services, motor vehicle manufacturing, law firms, and commercial facilities, according to Morphisec. “Despite the geographic expansion, Mexico remains the primary target,”…
Read MoreApr 03, 2024NewsroomWeb Security / Vulnerability A critical security flaw impacting the LayerSlider plugin for WordPress could be abused to extract sensitive information from databases, such as password hashes. The flaw, designated as CVE-2024-2879, carries a CVSS score of 9.8 out of a maximum of 10.0. It has been described as a case of SQL…
Read MoreApr 02, 2024NewsroomFirmware Security / Vulnerability The malicious code inserted into the open-source library XZ Utils, a widely used package present in major Linux distributions, is also capable of facilitating remote code execution, a new analysis has revealed. The audacious supply chain compromise, tracked as CVE-2024-3094 (CVSS score: 10.0), came to light last week when…
Read MoreApr 02, 2024NewsroomCyber Espionage / Threat Intelligence A threat activity cluster tracked as Earth Freybug has been observed using a new malware called UNAPIMON to fly under the radar. “Earth Freybug is a cyberthreat group that has been active since at least 2012 that focuses on espionage and financially motivated activities,” Trend Micro security researcher…
Read More