Tag: network security
Sep 05, 2024Ravie Lakshmanan Cisco has released security updates for two critical security flaws impacting its Smart Licensing Utility that could allow unauthenticated, remote attackers to elevate their privileges or access sensitive information. A brief description of the two vulnerabilities is below – CVE-2024-20439 (CVSS score: 9.8) – The presence of an undocumented static user…
Read MoreNorth Korean threat actors have leveraged a fake Windows video conferencing application impersonating FreeConference.com to backdoor developer systems as part of an ongoing financially-driven campaign dubbed Contagious Interview. The new attack wave, spotted by Singaporean company Group-IB in mid-August 2024, is yet another indication that the activity is also leveraging native installers for Windows and…
Read MoreSep 04, 2024Ravie LakshmananVulnerability / Mobile Security Google has released its monthly security updates for the Android operating system to address a known security flaw that it said has come under active exploitation in the wild. The high-severity vulnerability, tracked as CVE-2024-32896 (CVSS score: 7.8), relates to a case of privilege escalation in the Android…
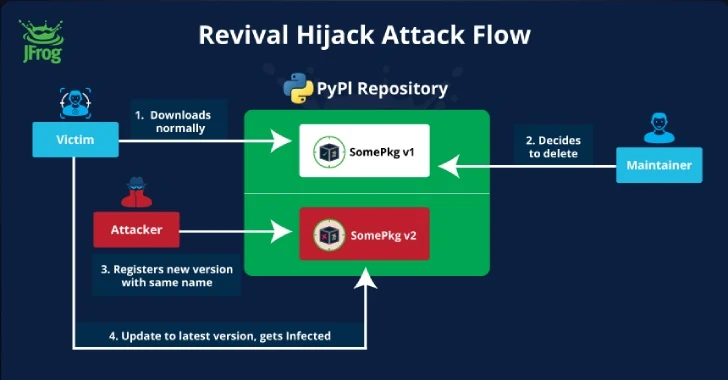
Read MoreSep 04, 2024Ravie Lakshmanan A new supply chain attack technique targeting the Python Package Index (PyPI) registry has been exploited in the wild in an attempt to infiltrate downstream organizations. It has been codenamed Revival Hijack by software supply chain security firm JFrog, which said the attack method could be used to hijack 22,000 existing…
Read MoreSep 04, 2024Ravie LakshmananVulnerability / Network Security Zyxel has released software updates to address a critical security flaw impacting certain access point (AP) and security router versions that could result in the execution of unauthorized commands. Tracked as CVE-2024-7261 (CVSS score: 9.8), the vulnerability has been described as a case of operating system (OS) command…
Read MoreSep 04, 2024The Hacker NewsSaaS Security / Browser Security Account takeover attacks have emerged as one of the most persistent and damaging threats to cloud-based SaaS environments. Yet despite significant investments in traditional security measures, many organizations continue to struggle with preventing these attacks. A new report, “Why Account Takeover Attacks Still Succeed, and Why…
Read MoreSep 04, 2024Ravie LakshmananGDPR / Privacy The Dutch Data Protection Authority (Dutch DPA) has imposed a fine of €30.5 million ($33.7 million) against facial recognition firm Clearview AI for violating the General Data Protection Regulation (GDPR) in the European Union (E.U.) by building an “illegal database with billions of photos of faces,” including those of…
Read MoreSep 04, 2024Ravie LakshmananMalware / Network Security A new malware campaign is spoofing Palo Alto Networks’ GlobalProtect VPN software to deliver a variant of the WikiLoader (aka WailingCrab) loader by means of a search engine optimization (SEO) campaign. The malvertising activity, observed in June 2024, is a departure from previously observed tactics wherein the malware…
Read MoreSep 03, 2024Ravie LakshmananEndpoint Security / Malware Cybersecurity researchers have unpacked the inner workings of a new ransomware variant called Cicada3301 that shares similarities with the now-defunct BlackCat (aka ALPHV) operation. “It appears that Cicada3301 ransomware primarily targets small to medium-sized businesses (SMBs), likely through opportunistic attacks that exploit vulnerabilities as the initial access vector,”…
Read MoreSep 03, 2024Ravie LakshmananRansomware / Malware A hacktivist group known as Head Mare has been linked to cyber attacks that exclusively target organizations located in Russia and Belarus. “Head Mare uses more up-to-date methods for obtaining initial access,” Kaspersky said in a Monday analysis of the group’s tactics and tools. “For instance, the attackers took…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm