Tag: network security
Aug 22, 2024Ravie LakshmananVulnerability / Network Security SolarWinds has issued patches to address a new security flaw in its Web Help Desk (WHD) software that could allow remote unauthenticated users to gain unauthorized access to susceptible instances. “The SolarWinds Web Help Desk (WHD) software is affected by a hardcoded credential vulnerability, allowing [a] remote unauthenticated…
Read MoreAug 22, 2024Ravie LakshmananHardware Security / Supply Chain Attack Cybersecurity researchers have uncovered a hardware backdoor within a particular model of MIFARE Classic contactless cards that could allow authentication with an unknown key and open hotel rooms and office doors. The attacks have been demonstrated against FM11RF08S, a new variant of MIFARE Classic that was…
Read MoreAug 22, 2024Ravie LakshmananNetwork Security / Zero-Day Details have emerged about a China-nexus threat group’s exploitation of a recently disclosed, now-patched security flaw in Cisco switches as a zero-day to seize control of the appliance and evade detection. The activity, attributed to Velvet Ant, was observed early this year and involved the weaponization of CVE-2024-20399…
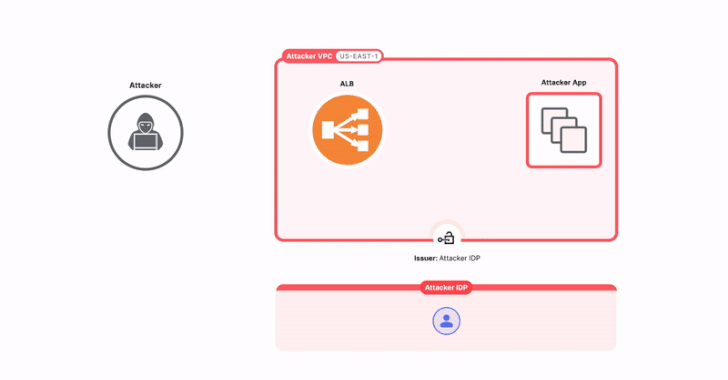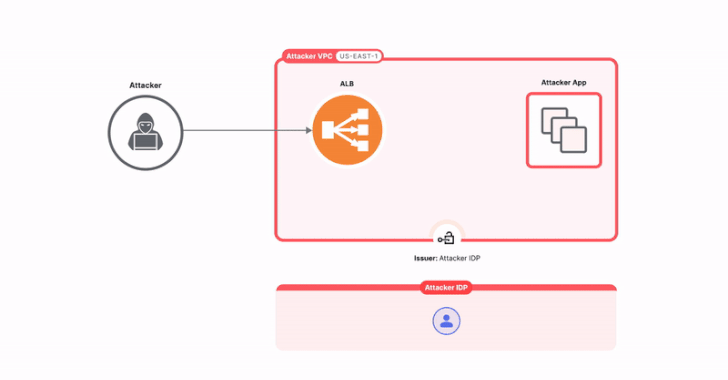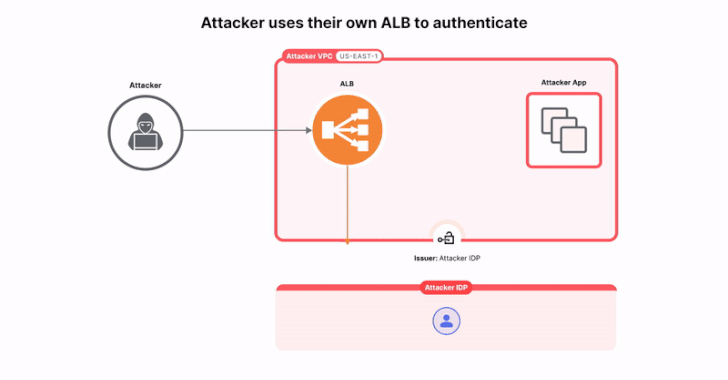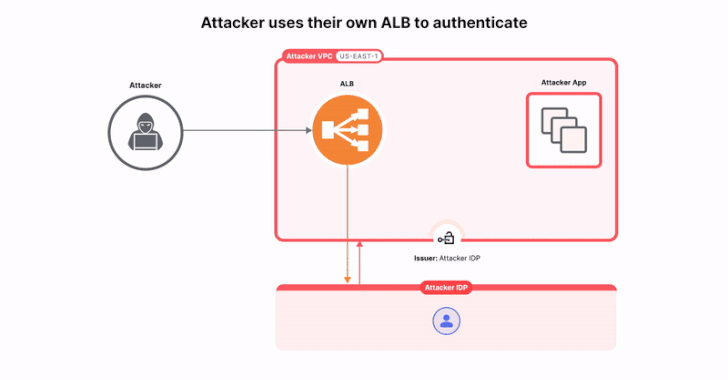
Read MoreAug 22, 2024Ravie LakshmananCloud Security / Application Security As many as 15,000 applications using Amazon Web Services’ (AWS) Application Load Balancer (ALB) for authentication are potentially susceptible to a configuration-based issue that could expose them to sidestep access controls and compromise applications. That’s according to findings from Israeli cybersecurity company Miggo, which dubbed the problem…
Read MoreWhat is Continuous Attack Surface Penetration Testing or CASPT? Continuous Penetration Testing or Continuous Attack Surface Penetration Testing (CASPT) is an advanced security practice that involves the continuous, automated, and ongoing penetration testing services of an organization’s digital assets to identify and mitigate security vulnerabilities. CASPT is designed for enterprises with an evolving attack surface…
Read MoreAug 22, 2024Ravie LakshmananEnterprise Software / Vulnerability GitHub has released fixes to address a set of three security flaws impacting its Enterprise Server product, including one critical bug that could be abused to gain site administrator privileges. The most severe of the shortcomings has been assigned the CVE identifier CVE-2024-6800, and carries a CVSS score…
Read MoreAug 22, 2024Ravie LakshmananWebsite Security / Vulnerability Cybersecurity researchers have disclosed a critical security flaw in the LiteSpeed Cache plugin for WordPress that could permit unauthenticated users to gain administrator privileges. “The plugin suffers from an unauthenticated privilege escalation vulnerability which allows any unauthenticated visitor to gain Administrator level access after which malicious plugins could…
Read MoreAug 22, 2024Ravie LakshmananBrowser Security / Vulnerability Google has rolled out security fixes to address a high-severity security flaw in its Chrome browser that it said has come under active exploitation in the wild. Tracked as CVE-2024-7971, the vulnerability has been described as a type confusion bug in the V8 JavaScript and WebAssembly engine. “Type…
Read MoreAug 22, 2024Ravie LakshmananDatabase Security / Cryptocurrency Cybersecurity researchers have unpacked a new malware strain dubbed PG_MEM that’s designed to mine cryptocurrency after brute-forcing their way into PostgreSQL database instances. “Brute-force attacks on Postgres involve repeatedly attempting to guess the database credentials until access is gained, exploiting weak passwords,” Aqua security researcher Assaf Morag said…
Read MoreAug 21, 2024Ravie LakshmananCyber Espionage / Malware A new remote access trojan called MoonPeak has been discovered as being used by a state-sponsored North Korean threat activity cluster as part of a new campaign. Cisco Talos attributed the malicious cyber campaign to a hacking group it tracks as UAT-5394, which it said exhibits some level…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm