Tag: network security
Aug 19, 2024Ravie LakshmananCybercrime / Network Security Cybersecurity researchers have discovered new infrastructure linked to a financially motivated threat actor known as FIN7. The two clusters of potential FIN7 activity “indicate communications inbound to FIN7 infrastructure from IP addresses assigned to Post Ltd (Russia) and SmartApe (Estonia), respectively,” Team Cymru said in a report published…
Read MoreOpenAI on Friday said it banned a set of accounts linked to what it said was an Iranian covert influence operation that leveraged ChatGPT to generate content that, among other things, focused on the upcoming U.S. presidential election. “This week we identified and took down a cluster of ChatGPT accounts that were generating content for…
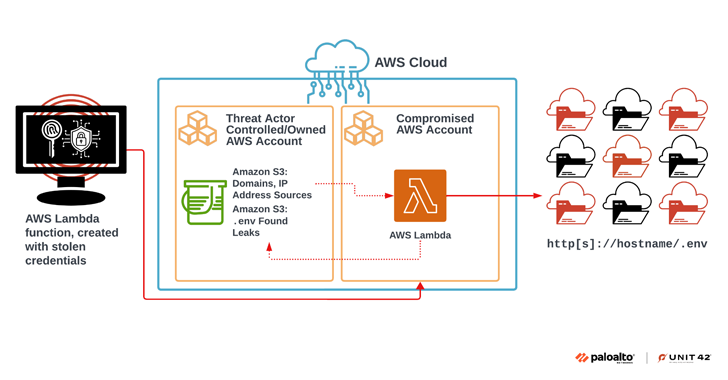
Read MoreAug 16, 2024Ravie LakshmananCloud Security / Application Security A large-scale extortion campaign has compromised various organizations by taking advantage of publicly accessible environment variable files (.env) that contain credentials associated with cloud and social media applications. “Multiple security missteps were present in the course of this campaign, including the following: Exposing environment variables, using long-lived…
Read MoreCisco CEO Chuck Robbins cited ‘several $100 million-plus transactions in the quarter.’ Deep cuts at Cisco Systems appear aimed at readying the 40-year-old networking giant for increased customer demand to modernize technology for improved security and artificial intelligence growth – areas where Cisco partners can see business gains in the new fiscal year. These are…
Read MoreAug 16, 2024Ravie LakshmananDark Web / Data Breach A 27-year-old Russian national has been sentenced to over three years in prison for peddling financial information, login credentials, and other personally identifying information (PII) on a now-defunct dark web marketplace called Slilpp. Georgy Kavzharadze, 27, of Moscow, Russia, pleaded guilty to one count of conspiracy to…
Read MoreAug 16, 2024Ravie LakshmananMalware / Data Theft Cybersecurity researchers have shed light on a sophisticated information stealer campaign that impersonates legitimate brands to distribute malware like DanaBot and StealC. The activity cluster, orchestrated by Russian-speaking cybercriminals and collectively codenamed Tusk, is said to encompass several sub-campaigns, leveraging the reputation of the platforms to trick users…
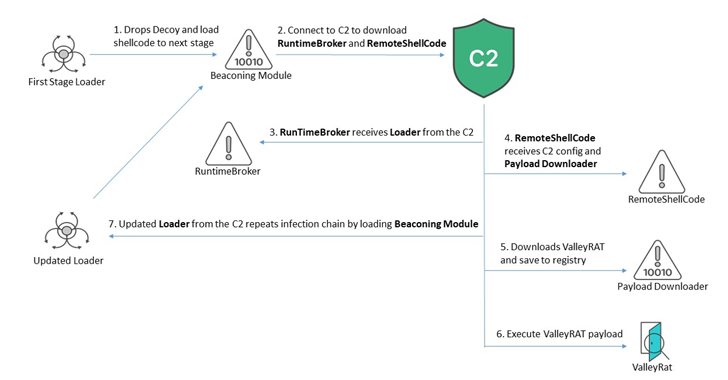
Read MoreAug 16, 2024Ravie LakshmananCyber Attack / Malware Chinese-speaking users are the target of an ongoing campaign that distributes malware known as ValleyRAT. “ValleyRAT is a multi-stage malware that utilizes diverse techniques to monitor and control its victims and deploy arbitrary plugins to cause further damage,” Fortinet FortiGuard Labs researchers Eduardo Altares and Joie Salvio said.…
Read MoreSaaS applications have become indispensable for organizations aiming to enhance productivity and streamline operations. However, the convenience and efficiency these applications offer come with inherent security risks, often leaving hidden gaps that can be exploited. Conducting thorough due diligence on SaaS apps is essential to identify and mitigate these risks, ensuring the protection of your…
Read MoreAug 16, 2024Ravie LakshmananMalware / Browser Security Cybersecurity researchers have uncovered new stealer malware that’s designed to specifically target Apple macOS systems. Dubbed Banshee Stealer, it’s offered for sale in the cybercrime underground for a steep price of $3,000 a month and works across both x86_64 and ARM64 architectures. “Banshee Stealer targets a wide range…
Read MoreAug 16, 2024Ravie LakshmananMobile Security / Software Security A large percentage of Google’s own Pixel devices shipped globally since September 2017 included dormant software that could be used to stage nefarious attacks and deliver various kinds of malware. The issue manifests in the form of a pre-installed Android app called “Showcase.apk” that comes with excessive…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm