Tag: network security
As part of the annual Tech Innovator Awards evaluation process CRN selects a number of the applicants as finalists. Here’s a look at the innovative products that have made the first round of the judging. Innovation Surge The wave of development around artificial intelligence and generative AI in the last two years has shaken up…
Read MoreNew Zscaler Channel Chief Anthony Torsiello On Plans For ‘Substantial Investments’ With Partners
by nlqip
A ServiceNow veteran who joins Zscaler as of Monday, Torsiello tells CRN that the cybersecurity vendor’s growth strategy ‘starts with having a highly capable ecosystem of partners.’ Anthony Torsiello, a former longtime channel business leader at ServiceNow, has been hired by Zscaler as its new global channel chief, he said in an interview with CRN.…
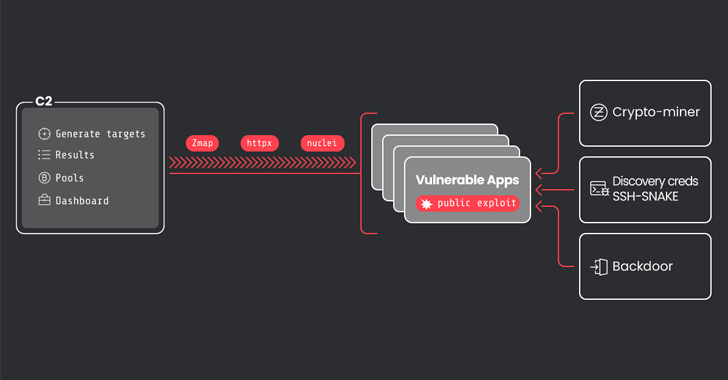
Read MoreJul 15, 2024NewsroomSaaS Security / Vulnerability A threat actor that was previously observed using an open-source network mapping tool has greatly expanded their operations to infect over 1,500 victims. Sysdig, which is tracking the cluster under the name CRYSTALRAY, said the activities have witnessed a 10x surge, adding it includes “mass scanning, exploiting multiple vulnerabilities,…
Read MoreImagine you could gain access to any Fortune 100 company for $10 or less, or even for free. Terrifying thought, isn’t it? Or exciting, depending on which side of the cybersecurity barricade you are on. Well, that’s basically the state of things today. Welcome to the infostealer garden of low-hanging fruit. Over the last few…
Read MoreJul 15, 2024NewsroomCybersecurity / Mobile Security Retail banking institutions in Singapore have three months to phase out the use of one-time passwords (OTPs) for authentication purposes when signing into online accounts to mitigate the risk of phishing attacks. The decision was announced by the Monetary Authority of Singapore (MAS) and The Association of Banks in…
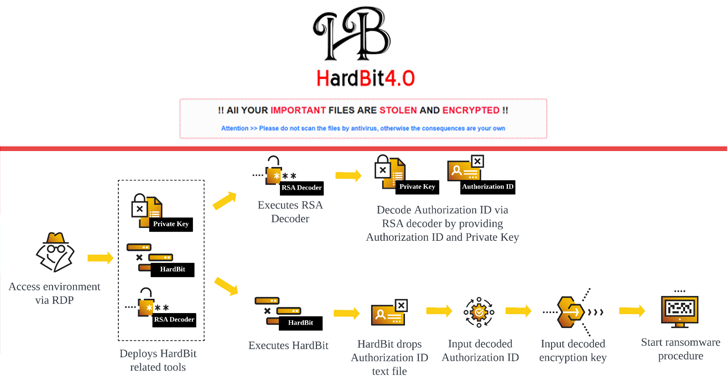
Read MoreJul 15, 2024NewsroomNetwork Security / Data Protection Cybersecurity researchers have shed light on a new version of a ransomware strain called HardBit that comes packaged with new obfuscation techniques to deter analysis efforts. “Unlike previous versions, HardBit Ransomware group enhanced the version 4.0 with passphrase protection,” Cybereason researchers Kotaro Ogino and Koshi Oyama said in…
Read MoreThe U.S. Department of Justice (DoJ) said it seized two internet domains and searched nearly 1,000 social media accounts that Russian threat actors allegedly used to covertly spread pro-Kremlin disinformation in the country and abroad on a large scale. “The social media bot farm used elements of AI to create fictitious social media profiles —…
Read MoreJul 12, 2024NewsroomVulnerability / Software Security A critical security issue has been disclosed in the Exim mail transfer agent that could enable threat actors to deliver malicious attachments to target users’ inboxes. The vulnerability, tracked as CVE-2024-39929, has a CVSS score of 9.1 out of 10.0. It has been addressed in version 4.98. “Exim through…
Read MoreJul 12, 2024The Hacker NewsDigital Security / Online Safety In today’s digital age, passwords serve as the keys to our most sensitive information, from social media accounts to banking and business systems. This immense power brings with it significant responsibility—and vulnerability. Most people don’t realize their credentials have been compromised until the damage is done.…
Read MoreJul 12, 2024NewsroomCyber Crime / Online Safety Two Russian-born Australian citizens have been arrested and charged in the country for spying on behalf of Russia as part of a “complex” law enforcement operation codenamed BURGAZADA. This includes a 40-year-old woman, an Australian Defence Force (ADF) Army Private, and her husband, a 62-year-old self-employed laborer. Media…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm