Tag: network security
Jun 24, 2024The Hacker NewsThreat Intelligence / Cybersecurity Learn about critical threats that can impact your organization and the bad actors behind them from Cybersixgill’s threat experts. Each story shines a light on underground activities, the threat actors involved, and why you should care, along with what you can do to mitigate risk. Cybersecurity professionals…
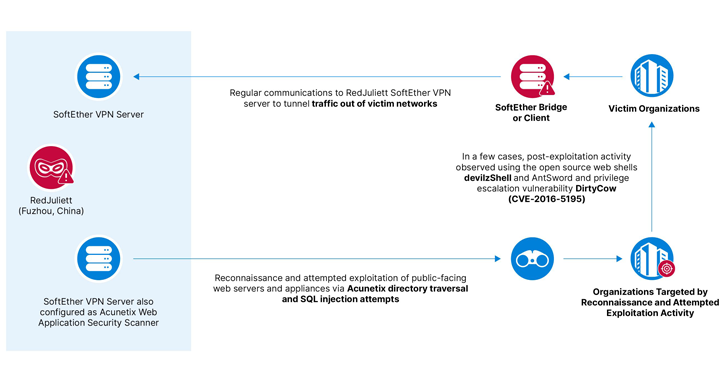
Read MoreJun 24, 2024NewsroomCyber Espionage / Hacking A likely China-linked state-sponsored threat actor has been linked to a cyber espionage campaign targeting government, academic, technology, and diplomatic organizations in Taiwan between November 2023 and April 2024. Recorded Future’s Insikt Group is tracking the activity under the name RedJuliett, describing it as a cluster that operates Fuzhou,…
Read MoreJun 24, 2024NewsroomMobile Security / Threat Intelligence Multiple threat actors, including cyber espionage groups, are employing an open-source Android remote administration tool called Rafel RAT to meet their operational objectives by masquerading it as Instagram, WhatsApp, and various e-commerce and antivirus apps. “It provides malicious actors with a powerful toolkit for remote administration and control,…
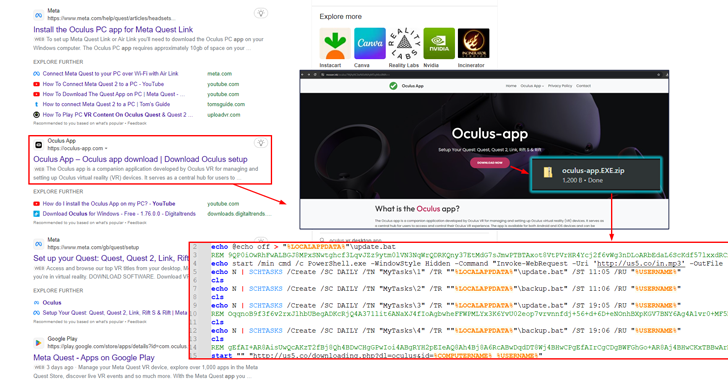
Read MoreJun 22, 2024NewsroomPhishing Attack / Adware A new campaign is tricking users searching for the Meta Quest (formerly Oculus) application for Windows into downloading a new adware family called AdsExhaust. “The adware is capable of exfiltrating screenshots from infected devices and interacting with browsers using simulated keystrokes,” cybersecurity firm eSentire said in an analysis, adding…
Read MoreJun 22, 2024NewsroomCyber Espionage / Threat Intelligence Russian organizations have been targeted by a cybercrime gang called ExCobalt using a previously unknown Golang-based backdoor known as GoRed. “ExCobalt focuses on cyber espionage and includes several members active since at least 2016 and presumably once part of the notorious Cobalt Gang,” Positive Technologies researchers Vladislav Lunin…
Read MoreJun 22, 2024NewsroomNational Security / Cyber Espionage The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) imposed sanctions against a dozen individuals serving executive and senior leadership roles at Kaspersky Lab, a day after the Russian company was banned by the Commerce Department. The move “underscores our commitment to ensure the integrity…
Read MoreThe U.S. did not sanction CEO and founder Eugene Kaspersky. The United States has blocked members of Russia-based cybersecurity vendor Kaspersky’s leadership from making transactions in the country a day after banning the company from making sales in the U.S. Twelve individuals associated with Kaspersky have been designated to the Specially Designated Nationals (SDN) list…
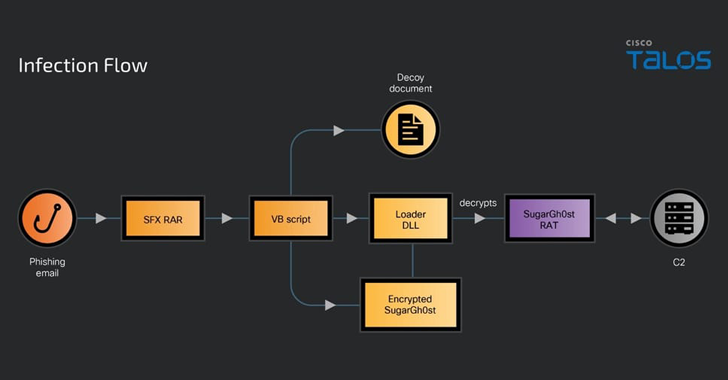
Read MoreJun 21, 2024NewsroomMalware / Threat Intelligence A previously undocumented Chinese-speaking threat actor codenamed SneakyChef has been linked to an espionage campaign primarily targeting government entities across Asia and EMEA (Europe, Middle East, and Africa) with SugarGh0st malware since at least August 2023. “SneakyChef uses lures that are scanned documents of government agencies, most of which…
Read MoreJun 21, 2024NewsroomPhishing Attack / Email Security Cybersecurity researchers have shed light on a new phishing campaign that has been identified as targeting people in Pakistan using a custom backdoor. Dubbed PHANTOM#SPIKE by Securonix, the unknown threat actors behind the activity have leveraged military-related phishing documents to activate the infection sequence. “While there are many…
Read MoreJun 21, 2024NewsroomMalware / Malvertising A malvertising campaign is leveraging trojanized installers for popular software such as Google Chrome and Microsoft Teams to drop a backdoor called Oyster (aka Broomstick and CleanUpLoader). That’s according to findings from Rapid7, which identified lookalike websites hosting the malicious payloads that users are redirected to after searching for them…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm