Tag: network security
Jun 19, 2024NewsroomZero-Day Exploits / Cyber Espionage The China-nexus cyber espionage actor linked to the zero-day exploitation of security flaws in Fortinet, Ivanti, and VMware devices has been observed utilizing multiple persistence mechanisms in order to maintain unfettered access to compromised environments. “Persistence mechanisms encompassed network devices, hypervisors, and virtual machines, ensuring alternative channels remain…
Read MoreJun 19, 2024The Hacker NewsGDPR Compliance / Data Privacy Are your tags really safe with Google Tag Manager? If you’ve been thinking that using GTM means that your tracking tags and pixels are safely managed, then it might be time to think again. In this article we look at how a big-ticket seller that does…
Read MoreJun 19, 2024NewsroomCybercrime / Cryptocurrency A threat actor who goes by alias markopolo has been identified as behind a large-scale cross-platform scam that targets digital currency users on social media with information stealer malware and carries out cryptocurrency theft. The attack chains involve the use of a purported virtual meeting software named Vortax (and 23…
Read MoreJun 19, 2024NewsroomMalware / Cyber Attack Chinese-speaking users are the target of a never-before-seen threat activity cluster codenamed Void Arachne that employs malicious Windows Installer (MSI) files for virtual private networks (VPNs) to deliver a command-and-control (C&C) framework called Winos 4.0. “The campaign also promotes compromised MSI files embedded with nudifiers and deepfake pornography-generating software,…
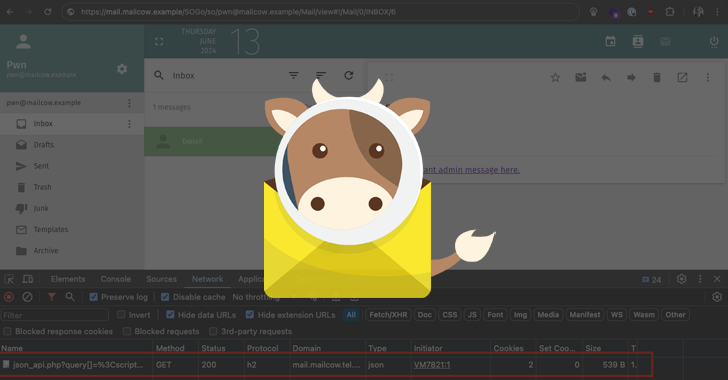
Read MoreJun 19, 2024NewsroomEmail Security / Vulnerability Two security vulnerabilities have been disclosed in the Mailcow open-source mail server suite that could be exploited by malicious actors to achieve arbitrary code execution on susceptible instances. Both shortcomings impact all versions of the software prior to version 2024-04, which was released on April 4, 2024. The issues…
Read MoreRiverbed Simplifies Channel Program, Focuses Only On Partners ‘On The Journey That We’re On’
by nlqip
‘[Riverbed] had way too many partners. We had basically been accumulating partners over probably the last 10 years or so. If a partner did a single transaction with us, we’d signed them up to the partner program even if they weren’t really interested in having a long-term strategic discussion with us,’ says Alex Thurber, Riverbed’s…
Read MoreJun 18, 2024NewsroomPrivacy / Encryption A controversial proposal put forth by the European Union to scan users’ private messages for detection child sexual abuse material (CSAM) poses severe risks to end-to-end encryption (E2EE), warned Meredith Whittaker, president of the Signal Foundation, which maintains the privacy-focused messaging service of the same name. “Mandating mass scanning of…
Read MoreJun 18, 2024NewsroomMalware / Cybercrime Threat actors are luring unsuspecting users with free or pirated versions of commercial software to deliver a malware loader called Hijack Loader, which then deploys an information stealer known as Vidar Stealer. “Adversaries had managed to trick users into downloading password-protected archive files containing trojanized copies of a Cisco Webex…
Read MoreSeventy percent of enterprises are prioritizing investment in SaaS security by establishing dedicated teams to secure SaaS applications, as part of a growing trend of maturity in this field of cybersecurity, according to a new survey released this month by the Cloud Security Alliance (CSA). Despite economic instability and major job cuts in 2023, organizations…
Read MoreJun 18, 2024NewsroomVulnerability / Cryptojacking Cybersecurity researchers have uncovered a new malware campaign that targets publicly exposed Docket API endpoints with the aim of delivering cryptocurrency miners and other payloads. Included among the tools deployed is a remote access tool that’s capable of downloading and executing more malicious programs as well as a utility to…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm