Tag: network security
Google has revealed that it took down 1,320 YouTube channels and 1,177 Blogger blogs as part of a coordinated influence operation connected to the People’s Republic of China (PRC). “The coordinated inauthentic network uploaded content in Chinese and English about China and U.S. foreign affairs,” Google Threat Analysis Group (TAG) researcher Billy Leonard said in…
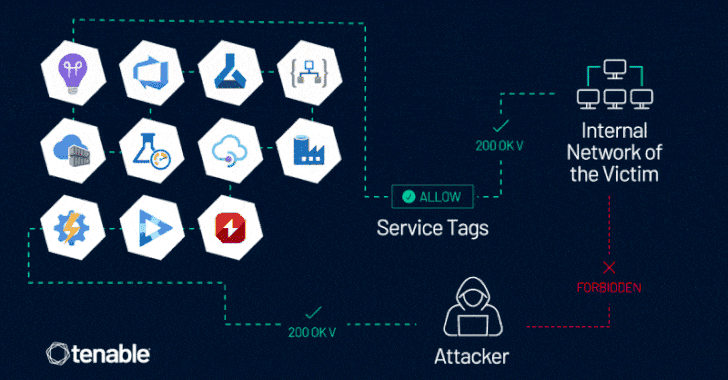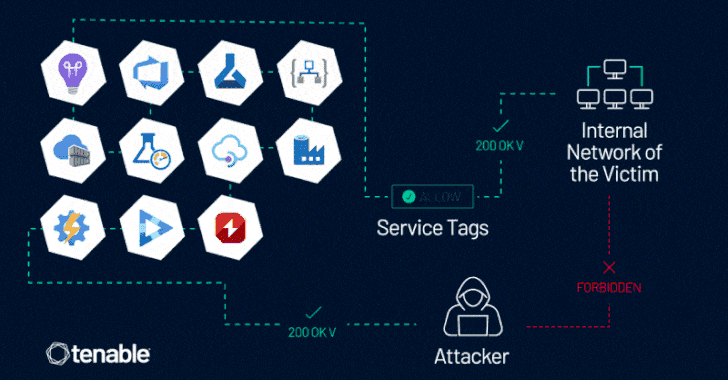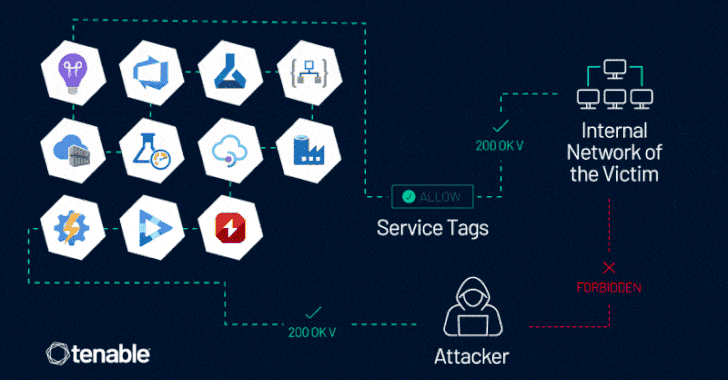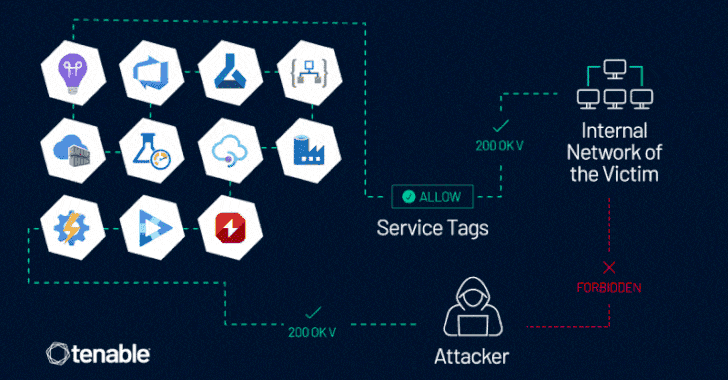
Read MoreJun 10, 2024NewsroomCloud Security / Vulnerability Microsoft is warning about the potential abuse of Azure Service Tags by malicious actors to forge requests from a trusted service and get around firewall rules, thereby allowing them to gain unauthorized access to cloud resources. “This case does highlight an inherent risk in using service tags as a…
Read MoreStaying Sharp: Cybersecurity CPEs Explained Perhaps even more so than in other professional domains, cybersecurity professionals constantly face new threats. To ensure you stay on top of your game, many certification programs require earning Continuing Professional Education (CPE) credits. CPEs are essentially units of measurement used to quantify the time and effort professionals spend on…
Read MoreWhat is Operational Technology? Operational Technology (OT) is the backbone of our modern world as we know it today. Think about the daily operations of a factory, the precise control of our power grids, and even the supply of clean water to our homes. All of these modern capabilities are made possible and efficient due…
Read MoreJun 10, 2024NewsroomCyber Espionage / Malware Cybersecurity researchers have disclosed details of a threat actor known as Sticky Werewolf that has been linked to cyber attacks targeting entities in Russia and Belarus. The phishing attacks were aimed at a pharmaceutical company, a Russian research institute dealing with microbiology and vaccine development, and the aviation sector,…
Read MoreJun 08, 2024NewsroomVulnerability / Programming Details have emerged about a new critical security flaw impacting PHP that could be exploited to achieve remote code execution under certain circumstances. The vulnerability, tracked as CVE-2024-4577, has been described as a CGI argument injection vulnerability affecting all versions of PHP installed on the Windows operating system. According to…
Read MoreJun 08, 2024NewsroomArtificial Intelligence / Privacy Microsoft on Friday said it will disable its much-criticized artificial intelligence (AI)-powered Recall feature by default and make it an opt-in. Recall, currently in preview and coming exclusively to Copilot+ PCs on June 18, 2024, functions as an “explorable visual timeline” by capturing screenshots of what appears on users’…
Read More‘If you listen to really smart people around the globe, they’ll tell you that [AI] is one of those technologies that is actually going to live up to the hype. And so the $1 billion global AI investment fund we just announced this week, that’s just the start for us, frankly,’ Cisco Executive Vice President…
Read MoreCybersecurity researchers have disclosed that the LightSpy spyware allegedly targeting Apple iOS users is in fact a previously undocumented macOS variant of the implant. The findings come from both Huntress Labs and ThreatFabric, which separately analyzed the artifacts associated with the cross-platform malware framework that likely possesses capabilities to infect Android, iOS, Windows, macOS, Linux,…
Read MoreJun 07, 2024The Hacker NewsCyber Hygiene / Webinar 2023 was a year of unprecedented cyberattacks. Ransomware crippled businesses, DDoS attacks disrupted critical services, and data breaches exposed millions of sensitive records. The cost of these attacks? Astronomical. The damage to reputations? Irreparable. But here’s the shocking truth: many of these attacks could have been prevented…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm