Tag: network security
Jun 03, 2024NewsroomSoftware Security / Supply Chain Cybersecurity researchers have uncovered a new suspicious package uploaded to the npm package registry that’s designed to drop a remote access trojan (RAT) on compromised systems. The package in question is glup-debugger-log, which targets users of the gulp toolkit by masquerading as a “logger for gulp and gulp…
Read MoreJun 03, 2024The Hacker NewsCyber Threat Intelligence Threat actors are evolving, yet Cyber Threat Intelligence (CTI) remains confined to each isolated point solution. Organizations require a holistic analysis across external data, inbound and outbound threats and network activity. This will enable evaluating the true state of cybersecurity in the enterprise. Cato’s Cyber Threat Research Lab…
Read MoreJun 03, 2024NewsroomEndpoint Security / Vulnerability Now-patched authorization bypass issues impacting Cox modems that could have been abused as a starting point to gain unauthorized access to the devices and run malicious commands. “This series of vulnerabilities demonstrated a way in which a fully external attacker with no prerequisites could’ve executed commands and modified the…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. The critical role of security testing within software development cannot be overstated. From protecting personal information to ensuring that critical infrastructure remains unbreachable,…
Read MoreJun 03, 2024NewsroomMalware / Cyber Attack The North Korea-linked threat actor known as Andariel has been observed using a new Golang-based backdoor called Dora RAT in its attacks targeting educational institutes, manufacturing firms, and construction businesses in South Korea. “Keylogger, Infostealer, and proxy tools on top of the backdoor were utilized for the attacks,” the…
Read MoreFake web browser updates are being used to deliver remote access trojans (RATs) and information stealer malware such as BitRAT and Lumma Stealer (aka LummaC2). “Fake browser updates have been responsible for numerous malware infections, including those of the well-known SocGholish malware,” cybersecurity firm eSentire said in a new report. “In April 2024, we observed…
Read MoreJun 01, 2024NewsroomAI-as-a-Service / Data Breach Artificial Intelligence (AI) company Hugging Face on Friday disclosed that it detected unauthorized access to its Spaces platform earlier this week. “We have suspicions that a subset of Spaces’ secrets could have been accessed without authorization,” it said in an advisory. Spaces offers a way for users to create,…
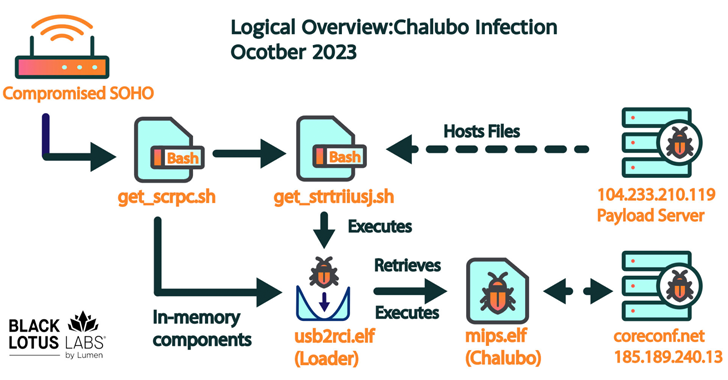
Read MoreMay 31, 2024NewsroomNetwork Security / Cyber Attack More than 600,000 small office/home office (SOHO) routers are estimated to have been bricked and taken offline following a destructive cyber attack staged by unidentified cyber actors, disrupting users’ access to the internet. The mysterious event, which took place between October 25 and 27, 2023, and impacted a…
Read MoreMicrosoft has emphasized the need for securing internet-exposed operational technology (OT) devices following a spate of cyber attacks targeting such environments since late 2023. “These repeated attacks against OT devices emphasize the crucial need to improve the security posture of OT devices and prevent critical systems from becoming easy targets,” the Microsoft Threat Intelligence team…
Read MoreMay 31, 2024NewsroomThreat Detection / Endpoint Security Digital content is a double-edged sword, providing vast benefits while simultaneously posing significant threats to organizations across the globe. The sharing of digital content has increased significantly in recent years, mainly via email, digital documents, and chat. In turn, this has created an expansive attack surface and has…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm