Tag: network security
The content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. In today’s digital world, businesses face the challenge of managing ever-expanding volumes of data efficiently and securely. Traditional on-premise storage solutions often come…
Read MoreThe U.S. Department of Justice (DoJ) on Wednesday said it dismantled what it described as “likely the world’s largest botnet ever,” which consisted of an army of 19 million infected devices that was leased to other threat actors to commit a wide array of offenses. The botnet, which has a global footprint spanning more than…
Read MoreMay 30, 2024NewsroomCredential Stuffing / Incident Response Okta is warning that a cross-origin authentication feature in Customer Identity Cloud (CIC) is susceptible to credential stuffing attacks orchestrated by threat actors. “We observed that the endpoints used to support the cross-origin authentication feature being attacked via credential stuffing for a number of our customers,” the Identity…
Read MoreMay 29, 2024NewsroomSoftware Security / Supply Chain Cybersecurity researchers have warned of a new malicious Python package that has been discovered in the Python Package Index (PyPI) repository to facilitate cryptocurrency theft as part of a broader campaign. The package in question is pytoileur, which has been downloaded 316 times as of writing. Interestingly, the…
Read MoreThe cybersecurity vendor says that a now-fixed VPN vulnerability has been exploited in attacks. Check Point has released emergency patches for a VPN vulnerability that the cybersecurity vendor said has been exploited in a small number of attacks. Initially disclosed by Check Point on Monday, the company released more details Tuesday as well as fixes…
Read MoreMay 29, 2024NewsroomEnterprise Security / Vulnerability Check Point is warning of a zero-day vulnerability in its Network Security gateway products that threat actors have exploited in the wild. Tracked as CVE-2024-24919, the issue impacts CloudGuard Network, Quantum Maestro, Quantum Scalable Chassis, Quantum Security Gateways, and Quantum Spark appliances. “The vulnerability potentially allows an attacker to…
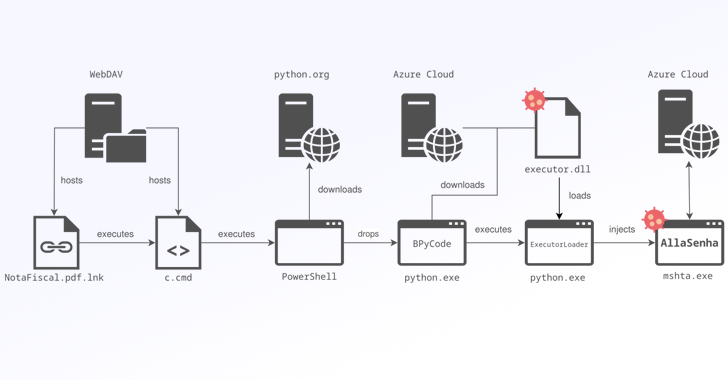
Read MoreBrazilian banking institutions are the target of a new campaign that distributes a custom variant of the Windows-based AllaKore remote access trojan (RAT) called AllaSenha. The malware is “specifically aimed at stealing credentials that are required to access Brazilian bank accounts, [and] leverages Azure cloud as command-and-control (C2) infrastructure,” French cybersecurity company HarfangLab said in…
Read MoreA recent study by Wing Security found that 63% of businesses may have former employees with access to organizational data, and that automating SaaS Security can help mitigate offboarding risks. Employee offboarding is typically seen as a routine administrative task, but it can pose substantial security risks, if not handled correctly. Failing to quickly and…
Read MoreMay 29, 2024NewsroomCybercrime / Cybersecurity The U.S. Department of Justice (DoJ) has sentenced a 31-year-old to 10 years in prison for laundering more than $4.5 million through business email compromise (BEC) schemes and romance scams. Malachi Mullings, 31, of Sandy Springs, Georgia pleaded guilty to the money laundering offenses in January 2023. According to court…
Read MoreA never-before-seen North Korean threat actor codenamed Moonstone Sleet has been attributed as behind cyber attacks targeting individuals and organizations in the software and information technology, education, and defense industrial base sectors with ransomware and bespoke malware previously associated with the infamous Lazarus Group. “Moonstone Sleet is observed to set up fake companies and job…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm