Tag: ransomware malware
Mar 02, 2024NewsroomSpyware / Privacy A U.S. judge has ordered NSO Group to hand over its source code for Pegasus and other products to Meta as part of the social media giant’s ongoing litigation against the Israeli spyware vendor. The decision, which marks a major legal victory for Meta, which filed the lawsuit in October…
Read MoreMar 02, 2024NewsroomCybercrime / Social Engineering The U.S. Department of Justice (DoJ) on Friday unsealed an indictment against an Iranian national for his alleged involvement in a multi-year cyber-enabled campaign designed to compromise U.S. governmental and private entities. More than a dozen entities are said to have been targeted, including the U.S. Departments of the…
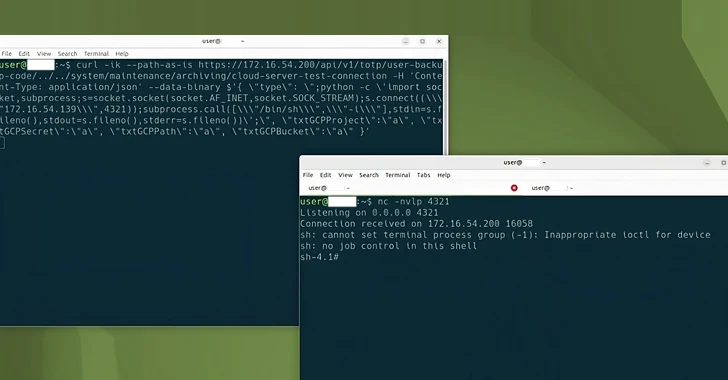
Read MoreMar 01, 2024NewsroomPhishing Kit / Cryptocurrency A novel phishing kit has been observed impersonating the login pages of well-known cryptocurrency services as part of an attack cluster designed to primarily target mobile devices. “This kit enables attackers to build carbon copies of single sign-on (SSO) pages, then use a combination of email, SMS, and voice…
Read MoreMar 01, 2024NewsroomLinux / Cyber Threat Cybersecurity researchers have discovered a new Linux variant of a remote access trojan (RAT) called BIFROSE (aka Bifrost) that uses a deceptive domain mimicking VMware. “This latest version of Bifrost aims to bypass security measures and compromise targeted systems,” Palo Alto Networks Unit 42 researchers Anmol Maurya and Siddharth…
Read MoreMore than a decade ago, the concept of the ‘blameless’ postmortem changed how tech companies recognize failures at scale. John Allspaw, who coined the term during his tenure at Etsy, argued postmortems were all about controlling our natural reaction to an incident, which is to point fingers: “One option is to assume the single cause…
Read MoreMar 01, 2024NewsroomRootkit / Threat Intelligence The Five Eyes (FVEY) intelligence alliance has issued a new cybersecurity advisory warning of cyber threat actors exploiting known security flaws in Ivanti Connect Secure and Ivanti Policy Secure gateways, noting that the Integrity Checker Tool (ICT) can be deceived to provide a false sense of security. “Ivanti ICT…
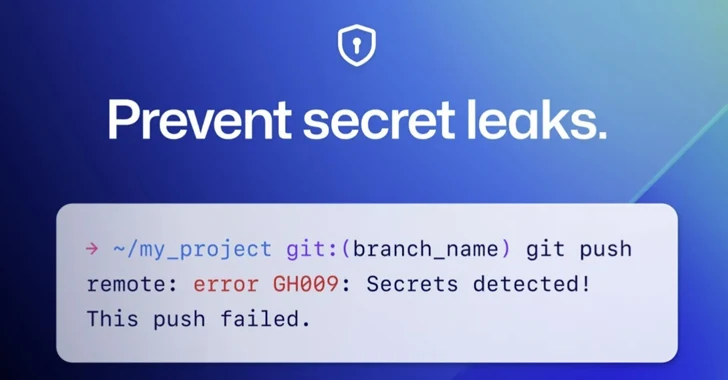
Read MoreMar 01, 2024NewsroomDevSecOps / Cybersecurity GitHub on Thursday announced that it’s enabling secret scanning push protection by default for all pushes to public repositories. “This means that when a supported secret is detected in any push to a public repository, you will have the option to remove the secret from your commits or, if you…
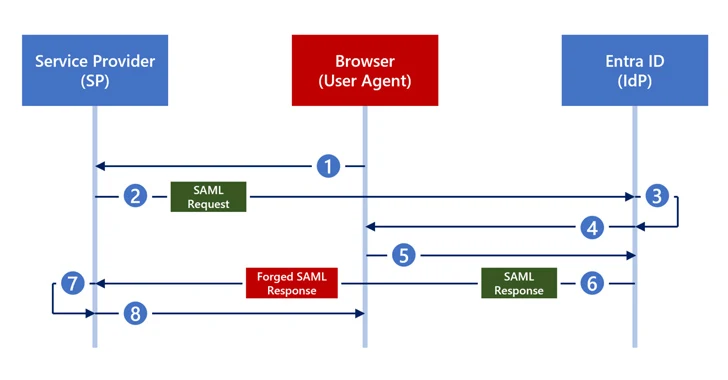
Read MoreFeb 29, 2024NewsroomThreat Intelligence / Cyber Threat Cybersecurity researchers have disclosed a new attack technique called Silver SAML that can be successful even in cases where mitigations have been applied against Golden SAML attacks. Silver SAML “enables the exploitation of SAML to launch attacks from an identity provider like Entra ID against applications configured to…
Read MoreFeb 29, 2024The Hacker NewsAttack Surface / Incident Response As an IT leader, staying on top of the latest cybersecurity developments is essential to keeping your organization safe. But with threats coming from all around — and hackers dreaming up new exploits every day — how do you create proactive, agile cybersecurity strategies? And what…
Read MoreFeb 29, 2024NewsroomRootkit / Threat Intelligence The notorious Lazarus Group actors exploited a recently patched privilege escalation flaw in the Windows Kernel as a zero-day to obtain kernel-level access and disable security software on compromised hosts. The vulnerability in question is CVE-2024-21338 (CVSS score: 7.8), which can permit an attacker to gain SYSTEM privileges. It…
Read More