Tag: ransomware malware
May 20, 2024The Hacker NewsSoftware Security / Vulnerability All developers want to create secure and dependable software. They should feel proud to release their code with the full confidence they did not introduce any weaknesses or anti-patterns into their applications. Unfortunately, developers are not writing their own code for the most part these days. 96%…
Read MoreMay 20, 2024NewsroomMalvertising / Cryptocurrency A “multi-faceted campaign” has been observed abusing legitimate services like GitHub and FileZilla to deliver an array of stealer malware and banking trojans such as Atomic (aka AMOS), Vidar, Lumma (aka LummaC2), and Octo by impersonating credible software like 1Password, Bartender 5, and Pixelmator Pro. “The presence of multiple malware…
Read MoreMay 20, 2024NewsroomCyber Attack / Malware Cybersecurity researchers have observed a spike in email phishing campaigns starting early March 2024 that delivers Latrodectus, a nascent malware loader believed to be the successor to the IcedID malware. “These campaigns typically involve a recognizable infection chain involving oversized JavaScript files that utilize WMI’s ability to invoke msiexec.exe…
Read MoreThe U.S. Department of Justice (DoJ) has charged two arrested Chinese nationals for allegedly orchestrating a pig butchering scam that laundered at least $73 million from victims through shell companies. The individuals, Daren Li, 41, and Yicheng Zhang, 38, were arrested in Atlanta and Los Angeles on April 12 and May 16, respectively. The foreign…
Read MoreMay 19, 2024NewsroomBanking Troja / Email Security The threat actors behind the Windows-based Grandoreiro banking trojan have returned in a global campaign since March 2024 following a law enforcement takedown in January. The large-scale phishing attacks, likely facilitated by other cybercriminals via a malware-as-a-service (MaaS) model, target over 1,500 banks across the world, spanning more…
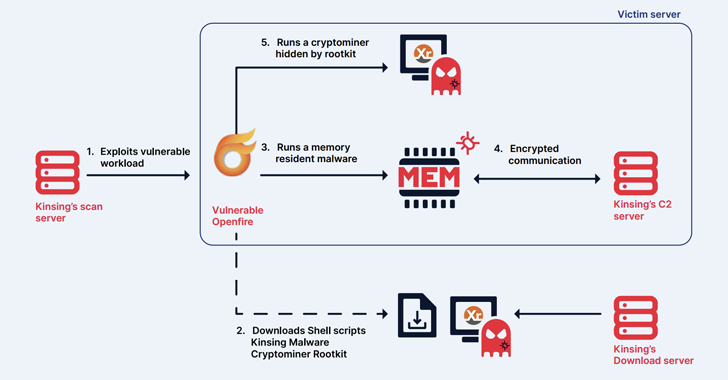
Read MoreMay 17, 2024NewsroomCryptojacking / Malware The cryptojacking group known as Kinsing has demonstrated its ability to continuously evolve and adapt, proving to be a persistent threat by swiftly integrating newly disclosed vulnerabilities to exploit arsenal and expand its botnet. The findings come from cloud security firm Aqua, which described the threat actor as actively orchestrating…
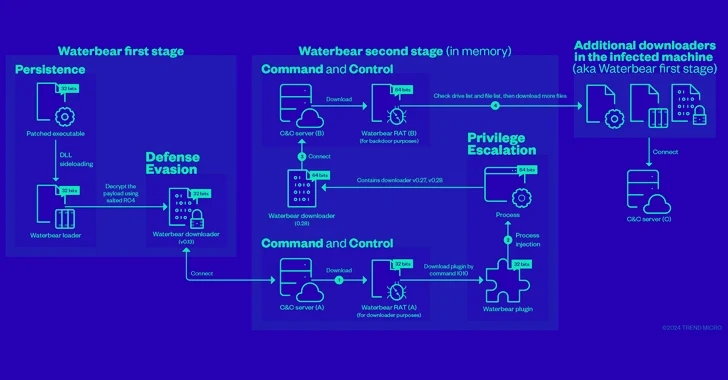
Read MoreCybersecurity researchers have shed more light on a remote access trojan (RAT) known as Deuterbear used by the China-linked BlackTech hacking group as part of a cyber espionage campaign targeting the Asia-Pacific region this year. “Deuterbear, while similar to Waterbear in many ways, shows advancements in capabilities such as including support for shellcode plugins, avoiding…
Read MoreA new report from XM Cyber has found – among other insights – a dramatic gap between where most organizations focus their security efforts, and where the most serious threats actually reside. The new report, Navigating the Paths of Risk: The State of Exposure Management in 2024, is based on hundreds of thousands of attack…
Read MoreMay 17, 2024NewsroomLinux / Malware The Kimsuky (aka Springtail) advanced persistent threat (APT) group, which is linked to North Korea’s Reconnaissance General Bureau (RGB), has been observed deploying a Linux version of its GoBear backdoor as part of a campaign targeting South Korean organizations. The backdoor, codenamed Gomir, is “structurally almost identical to GoBear, with…
Read MoreMay 17, 2024NewsroomVulnerability / Network Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added two security flaws impacting D-Link routers to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The list of vulnerabilities is as follows – CVE-2014-100005 – A cross-site request forgery (CSRF) vulnerability impacting D-Link DIR-600…
Read MoreRecent Posts
- Hackers abuse Avast anti-rootkit driver to disable defenses
- Microsoft testing Windows 11 support for third-party passkeys
- Windows 11 24H2 update blocked on PCs with Assassin’s Creed, Star Wars Outlaws
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day