Tag: software vulnerability
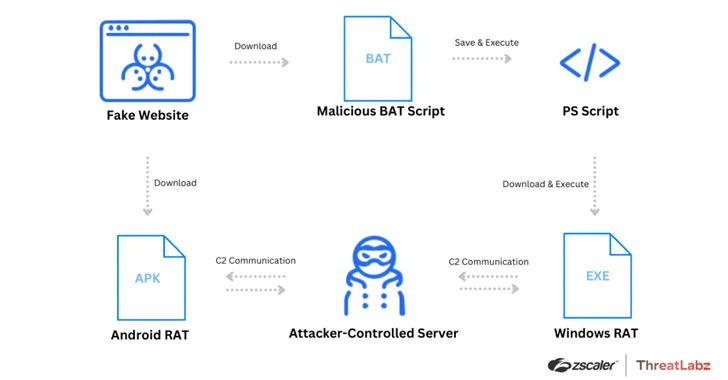
Mar 07, 2024NewsroomMalware / Network Security Threat actors have been leveraging fake websites advertising popular video conferencing software such as Google Meet, Skype, and Zoom to deliver a variety of malware targeting both Android and Windows users since December 2023. “The threat actor is distributing Remote Access Trojans (RATs) including SpyNote RAT for Android platforms,…
Read MoreMar 06, 2024NewsroomServer Security / Cryptocurrency Threat actors are targeting misconfigured and vulnerable servers running Apache Hadoop YARN, Docker, Atlassian Confluence, and Redis services as part of an emerging malware campaign designed to deliver a cryptocurrency miner and spawn a reverse shell for persistent remote access. “The attackers leverage these tools to issue exploit code,…
Read MoreMar 06, 2024NewsroomCyber Crime / Ransomware The threat actors behind the BlackCat ransomware have shut down their darknet website and likely pulled an exit scam after uploading a bogus law enforcement seizure banner. “ALPHV/BlackCat did not get seized. They are exit scamming their affiliates,” security researcher Fabian Wosar said. “It is blatantly obvious when you…
Read MoreAn in-depth look into a proactive website security solution that continuously detects, prioritizes, and validates web threats, helping to mitigate security, privacy, and compliance risks. [Reflectiz shields websites from client-side attacks, supply chain risks, data breaches, privacy violations, and compliance issues] You Can’t Protect What You Can’t See Today’s websites are connected to dozens of…
Read MoreMar 06, 2024The Hacker NewsData Security / Cloud Security Every Google Workspace administrator knows how quickly Google Drive becomes a messy sprawl of loosely shared confidential information. This isn’t anyone’s fault; it’s inevitable as your productivity suite is purposefully designed to enable real-time collaboration – both internally and externally. For Security & Risk Management teams,…
Read MoreMar 06, 2024NewsroomCyber Attack / Malware A financial entity in Vietnam was the target of a previously undocumented threat actor called Lotus Bane that was first detected in March 2023. Singapore-headquartered Group-IB described the hacking outfit as an advanced persistent threat group that’s believed to have been active since at least 2022. The exact specifics…
Read MoreMar 06, 2024NewsroomSoftware Security / Vulnerability VMware has released patches to address four security flaws impacting ESXi, Workstation, and Fusion, including two critical flaws that could lead to code execution. Tracked as CVE-2024-22252 and CVE-2024-22253, the vulnerabilities have been described as use-after-free bugs in the XHCI USB controller. They carry a CVSS score of 9.3…
Read MoreMar 06, 2024NewsroomPrivacy / Spyware The U.S. Department of Treasury’s Office of Foreign Assets Control (OFAC) sanctioned two individuals and five entities associated with the Intellexa Alliance for their role in “developing, operating, and distributing” commercial spyware designed to target government officials, journalists, and policy experts in the country. “The proliferation of commercial spyware poses…
Read MoreThe cybercrime group called GhostSec has been linked to a Golang variant of a ransomware family called GhostLocker. “TheGhostSec and Stormous ransomware groups are jointly conducting double extortion ransomware attacks on various business verticals in multiple countries,” Cisco Talos researcher Chetan Raghuprasad said in a report shared with The Hacker News. “GhostLocker and Stormous ransomware…
Read MoreMar 06, 2024NewsroomVulnerability / Zero Day Apple has released security updates to address several security flaws, including two vulnerabilities that it said have been actively exploited in the wild. The shortcomings are listed below – CVE-2024-23225 – A memory corruption issue in Kernel that an attacker with arbitrary kernel read and write capability can exploit…
Read More