Tag: software vulnerability
Aug 15, 2024The Hacker NewsIdentity Security / Threat Detection The Emergence of Identity Threat Detection and Response Identity Threat Detection and Response (ITDR) has emerged as a critical component to effectively detect and respond to identity-based attacks. Threat actors have shown their ability to compromise the identity infrastructure and move laterally into IaaS, Saas, PaaS…
Read MoreAug 15, 2024Ravie LakshmananCyber Espionage / Data Theft A previously unknown threat actor has been attributed to a spate of attacks targeting Azerbaijan and Israel with an aim to steal sensitive data. The attack campaign, detected by NSFOCUS on July 1, 2024, leveraged spear-phishing emails to single out Azerbaijani and Israeli diplomats. The activity is…
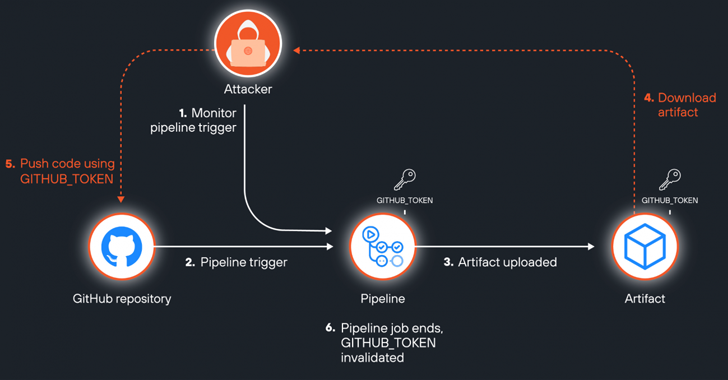
Read MoreAug 15, 2024Ravie LakshmananCloud Security / DevOps A newly discovered attack vector in GitHub Actions artifacts dubbed ArtiPACKED could be exploited to take over repositories and gain access to organizations’ cloud environments. “A combination of misconfigurations and security flaws can make artifacts leak tokens, both of third party cloud services and GitHub tokens, making them…
Read MoreAug 15, 2024Ravie LakshmananNetwork Security / Cybercrime Cybersecurity researchers have discovered a new variant of the Gafgyt botnet that’s targeting machines with weak SSH passwords to ultimately mine cryptocurrency on compromised instances using their GPU computational power. This indicates that the “IoT botnet is targeting more robust servers running on cloud native environments,” Aqua Security…
Read MoreAug 14, 2024Ravie LakshmananMalware / Network Security An ongoing social engineering campaign with alleged links to the Black Basta ransomware group has been linked to “multiple intrusion attempts” with the goal of conducting credential theft and deploying a malware dropper called SystemBC. “The initial lure being utilized by the threat actors remains the same: an…
Read MoreAug 14, 2024The Hacker NewsPassword Security / Cyber Security Simply relying on traditional password security measures is no longer sufficient. When it comes to protecting your organization from credential-based attacks, it is essential to lock down the basics first. Securing your Active Directory should be a priority – it is like making sure a house…
Read MoreA coalition of law enforcement agencies coordinated by the U.K. National Crime Agency (NCA) has led to the arrest and extradition of a Belarussian and Ukrainian dual-national believed to be associated with Russian-speaking cybercrime groups. Maksim Silnikau (aka Maksym Silnikov), 38, went by the online monikers J.P. Morgan, xxx, and lansky. He was extradited to…
Read MoreMonitoring evolving DDoS trends is essential for anticipating threats and adapting defensive strategies. The comprehensive Gcore Radar Report for the first half of 2024 provides detailed insights into DDoS attack data, showcasing changes in attack patterns and the broader landscape of cyber threats. Here, we share a selection of findings from the full report. Key…
Read MoreAug 14, 2024Ravie LakshmananThreat Intelligence / Cyber Attack The China-backed threat actor known as Earth Baku has diversified its targeting footprint beyond the Indo-Pacific region to include Europe, the Middle East, and Africa starting in late 2022. Newly targeted countries as part of the activity include Italy, Germany, the U.A.E., and Qatar, with suspected attacks…
Read MoreAug 14, 2024Ravie LakshmananVulnerability / Network Security Ivanti has rolled out security updates for a critical flaw in Virtual Traffic Manager (vTM) that could be exploited to achieve an authentication bypass and create rogue administrative users. The vulnerability, tracked as CVE-2024-7593, has a CVSS score of 9.8 out of a maximum of 10.0. “Incorrect implementation…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm