Tag: the hacker news
Mar 18, 2024NewsroomCyber Warfare / Malware The Russia-linked threat actor known as APT28 has been linked to multiple ongoing phishing campaigns that employ lure documents imitating government and non-governmental organizations (NGOs) in Europe, the South Caucasus, Central Asia, and North and South America. “The uncovered lures include a mixture of internal and publicly available documents,…
Read MoreMar 16, 2024NewsroomMalware / Cybercrime Cybersecurity researchers have found a number of GitHub repositories offering cracked software that are used to deliver an information stealer called RisePro. The campaign, codenamed gitgub, includes 17 repositories associated with 11 different accounts, according to G DATA. The repositories in question have since been taken down by the Microsoft-owned…
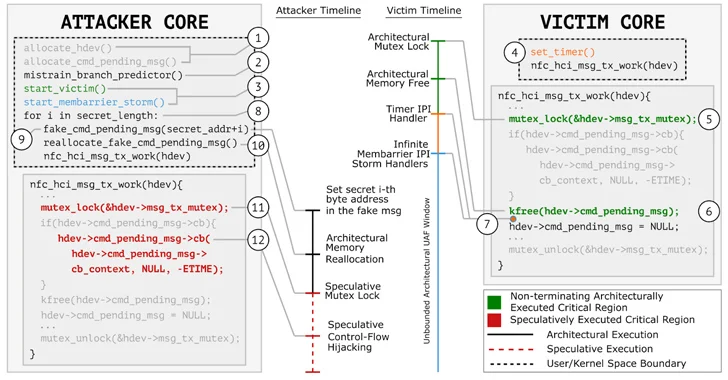
Read MoreMar 15, 2024NewsroomHardware Security / Data Protection A group of researchers has discovered a new data leakage attack impacting modern CPU architectures supporting speculative execution. Dubbed GhostRace (CVE-2024-2193), it is a variation of the transient execution CPU vulnerability known as Spectre v1 (CVE-2017-5753). The approach combines speculative execution and race conditions. “All the common synchronization…
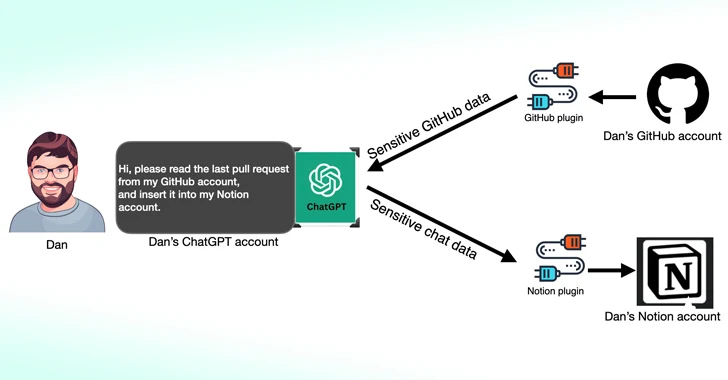
Read MoreMar 15, 2024NewsroomData Privacy / Artificial Intelligence Cybersecurity researchers have found that third-party plugins available for OpenAI ChatGPT could act as a new attack surface for threat actors looking to gain unauthorized access to sensitive data. According to new research published by Salt Labs, security flaws found directly in ChatGPT and within the ecosystem could…
Read MoreMar 15, 2024NewsroomBrowser Security / Phishing Attack Google on Thursday announced an enhanced version of Safe Browsing to provide real-time, privacy-preserving URL protection and safeguard users from visiting potentially malicious sites. “The Standard protection mode for Chrome on desktop and iOS will check sites against Google’s server-side list of known bad sites in real-time,” Google’s…
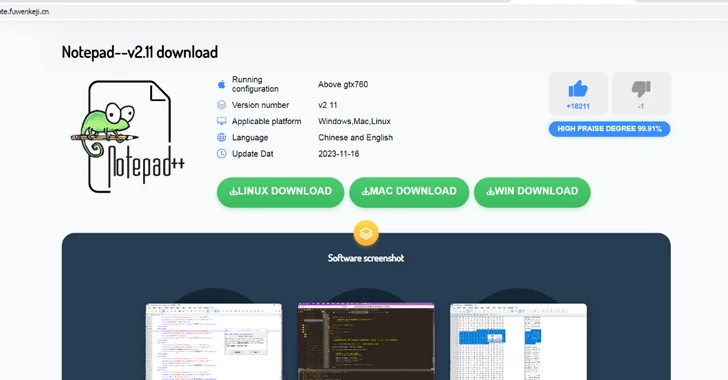
Read MoreMar 15, 2024NewsroomMalvertising / Threat Intelligence Chinese users looking for legitimate software such as Notepad++ and VNote on search engines like Baidu are being targeted with malicious ads and bogus links to distribute trojanized versions of the software and ultimately deploy Geacon, a Golang-based implementation of Cobalt Strike. “The malicious site found in the notepad++…
Read MoreMar 14, 2024NewsroomRansomware / Cyber Crime A 34-year-old Russian-Canadian national has been sentenced to nearly four years in jail in Canada for his participation in the LockBit global ransomware operation. Mikhail Vasiliev, an Ontario resident, was originally arrested in November 2022 and charged by the U.S. Department of Justice (DoJ) with “conspiring with others to…
Read MoreMar 14, 2024NewsroomContainer Security / Vulnerability Details have been made public about a now-patched high-severity flaw in Kubernetes that could allow a malicious attacker to achieve remote code execution with elevated privileges under specific circumstances. “The vulnerability allows remote code execution with SYSTEM privileges on all Windows endpoints within a Kubernetes cluster,” Akamai security researcher…
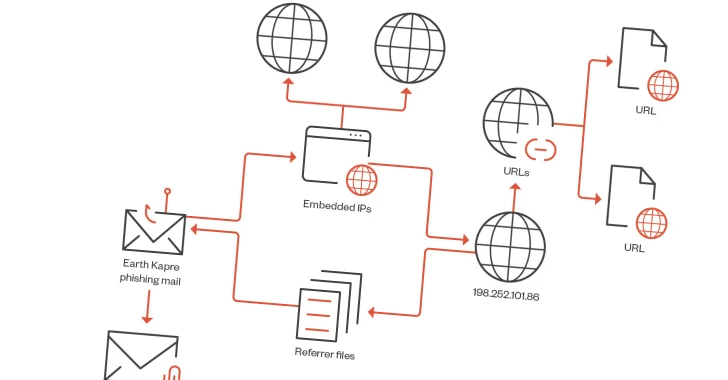
Read MoreMar 14, 2024NewsroomCyber Espionage / Malware The Russian-speaking cybercrime group called RedCurl is leveraging a legitimate Microsoft Windows component called the Program Compatibility Assistant (PCA) to execute malicious commands. “The Program Compatibility Assistant Service (pcalua.exe) is a Windows service designed to identify and address compatibility issues with older programs,” Trend Micro said in an analysis…
Read MoreBeing a CISO is a balancing act: ensuring organizations are secure without compromising users’ productivity. This requires taking multiple elements into consideration, like cost, complexity, performance and user experience. CISOs around the globe use Cato SSE 360, as part of the Cato SASE Cloud platform to balance these factors without compromise. This article details how…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm