Month: May 2024
MS-ISAC ADVISORY NUMBER: 2024-065 DATE(S) ISSUED: 05/31/2024 OVERVIEW: A vulnerability has been discovered in Check Point Security Gateway Products that could allow for credential access. A Check Point Security Gateway sits between an organization’s environment and the Internet to enforce policy and block threats and malware. Successful exploitation of this vulnerability could allow for credential…
Read MoreInfinidat is using AMD processors for its latest InfiniBox G4 for the first time to increase performance and cut power consumption, and is adding a new controller upgrade program, a new consumption-based pricing model, and integration of its data protection capabilities with third-party cybersecurity software. High-performance storage technology developer Infinidat has expanded its portfolio with…
Read MoreLive Nation has confirmed that Ticketmaster suffered a data breach after its data was stolen from a third-party cloud database provider, which is believed to be Snowflake. “On May 20, 2024, Live Nation Entertainment, Inc. (the “Company” or “we”) identified unauthorized activity within a third-party cloud database environment containing Company data (primarily from its Ticketmaster…
Read MoreStalkerware app pcTattletale announces it is ‘out of business’ after suffering data breach and website defacement
by nlqip
US spyware vendor pcTattletale has shut down its operations following a serious data breach that exposed sensitive information about its customers, as well as data stolen from some of their victims. pcTattletale was promoted as “employee and child monitoring software” designed to “protect your business and family.” Of course, what it actually was, was a…
Read MoreFriday Squid Blogging: Baby Colossal Squid This video might be a juvenile colossal squid. As usual, you can also use this squid post to talk about the security stories in the news that I haven’t covered. Read my blog posting guidelines here. Tags: squid, video Posted on May 31, 2024 at 5:02 PM • 0…
Read MoreJapanese crypto exchange DMM Bitcoin is warning that 4,502.9 Bitcoin (BTC), or approximately $308 million (48.2 billion yen), has been stolen from one of its wallets today, making it the most significant cryptocurrency heist of 2024. “At approximately 1:26 p.m. on Friday, May 31, 2024, we detected an unauthorized leak of Bitcoin (BTC) from our wallet,” DMM…
Read MoreThe U.S. Cybersecurity & Infrastructure Security Agency (CISA) has added two vulnerabilities in its Known Exploited Vulnerabilities (KEV) catalog, including a Linux kernel privilege elevation flaw. The high-severity flaw tracked as CVE-2024-1086 was first disclosed on January 31, 2024, as a use-after-free problem in the netfilter: nf_tables component, but was first introduced by a commit…
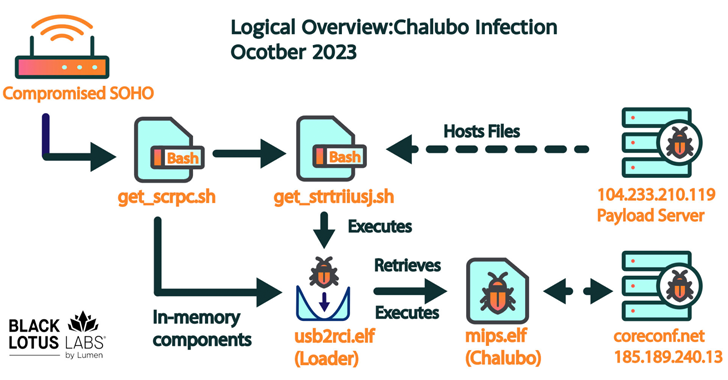
Read MoreMay 31, 2024NewsroomNetwork Security / Cyber Attack More than 600,000 small office/home office (SOHO) routers are estimated to have been bricked and taken offline following a destructive cyber attack staged by unidentified cyber actors, disrupting users’ access to the internet. The mysterious event, which took place between October 25 and 27, 2023, and impacted a…
Read MoreFor the week ending May 31, CRN takes a look at the companies that brought their ‘A’ game to the channel including T-Mobile, CloudFlare, Cisco Systems, Lenovo and CoreWeave, along with all the companies that made this year’s CRN Solution Provider 500. The Week Ending May 31 Topping this week’s Came to Win is T-Mobile…
Read More‘Customers choose NetApp to support them at every phase of the AI lifecycle due to our high-performance, all-flash storage complemented by comprehensive data management capabilities that support requirements from data preparation, model training and tuning, retrieval augmented generation (RAG), and inferencing, as well as requirements for responsible AI including model and data versioning, data governance,…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA