CISA warns of actively exploited Linux privilege elevation flaw
by nlqip

The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has added two vulnerabilities in its Known Exploited Vulnerabilities (KEV) catalog, including a Linux kernel privilege elevation flaw.
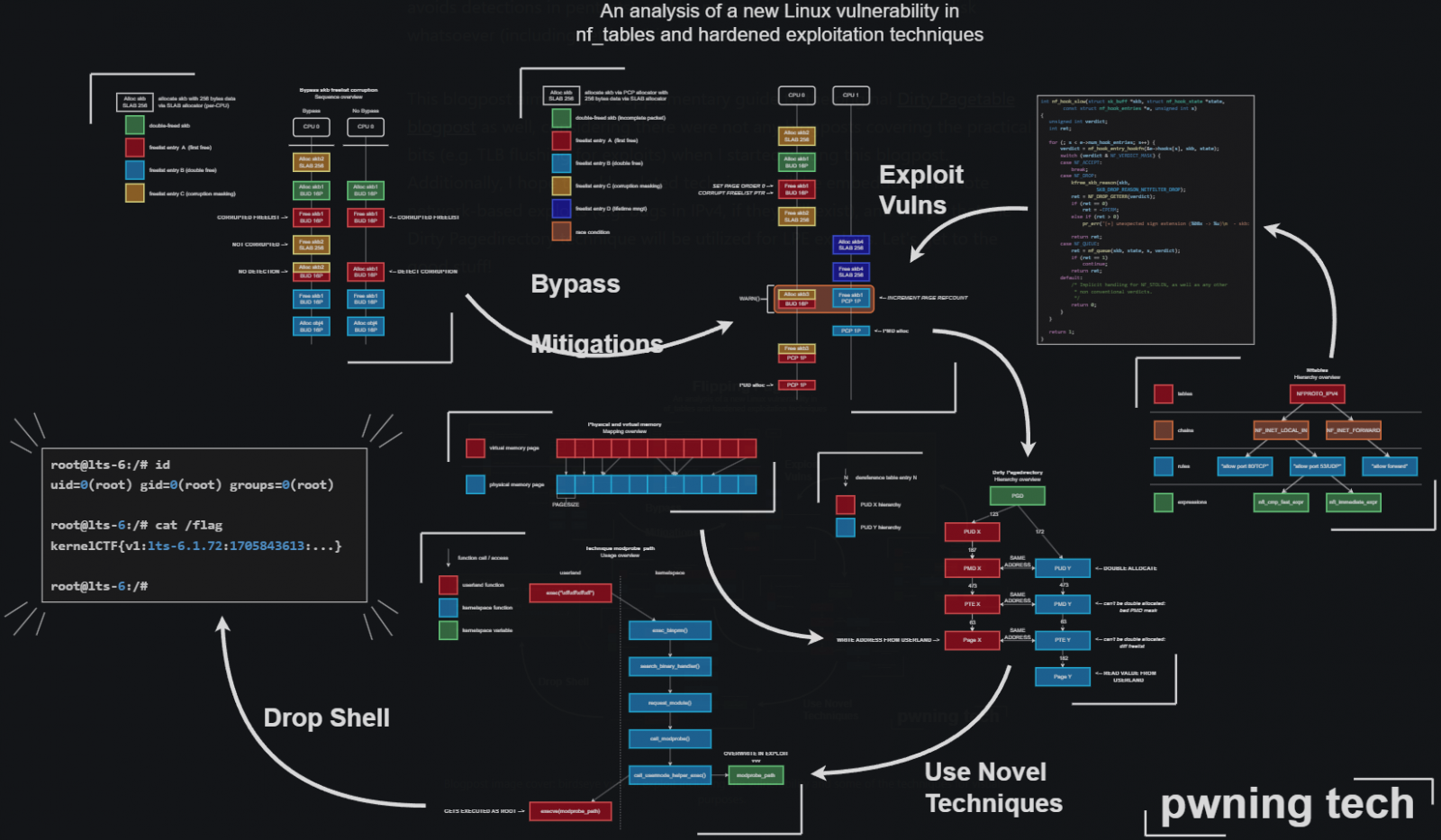
The high-severity flaw tracked as CVE-2024-1086 was first disclosed on January 31, 2024, as a use-after-free problem in the netfilter: nf_tables component, but was first introduced by a commit in February 2014.
Netfilter is a framework provided by the Linux kernel that allows various networking-related operations, such as packet filtering, network address translation (NAT), and packet mangling.
The vulnerability is caused because the ‘nft_verdict_init()’ function allows positive values to be used as a drop error within the hook verdict, causing the ‘nf_hook_slow()’ function to execute a double free when NF_DROP is issued with a drop error that resembles NF_ACCEPT.
Exploitation of CVE-2024-1086 allows an attacker with local access to achieve privilege escalation on the target system, potentially gaining root-level access.
The issue was fixed via a commit submitted in January 2024, which rejects QUEUE/DROP verdict parameters, thus preventing exploitation.
The fix has been backported to multiple stable kernel versions as listed below:
- v5.4.269 and later
- v5.10.210 and later
- v6.6.15 and later
- v4.19.307 and later
- v6.1.76 and later
- v5.15.149 and later
- v6.7.3 and later
In late March 2024, a security researcher using the alias ‘Notselwyn’ published a detailed write-up and proof-of-concept (PoC) exploit on GitHub, showcasing how to achieve local privilege escalation by exploiting the flaw on Linux kernel versions between 5.14 and 6.6.
While most Linux distrobutions pushed out fixes fairly quickly, Red Hat had not pushed out a fix until March, making it possible that threat actors used the public exploit on compromised systems.
CISA did not share specific details about how the vulnerability is exploited, but BleepingComputer has seen posts on hacking forums about the public exploits.
The cybersecurity agency has now given federal agencies until June 20, 2024, to apply the available patches.
If updating is not possible, admins are recommended to apply the following mitigations:
- Blocklist ‘nf_tables’ if it’s not needed/actively used.
- Restrict access to user namespaces to limit the attack surface.
- Load the Linux Kernel Runtime Guard (LKRG) module (can cause instability)
The second flaw CISA added on the KEV catalog this time, also setting the due date to June 20, is CVE-2024-24919, an information disclosure vulnerability impacting VPN devices from Check Point.
Following the vendor’s disclosure and security update release for this flaw, researchers from Watchtowr Labs published their analysis, underlining that the vulnerability is far worse than what Check Point’s bulletin reflected.
Source link
lol
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has added two vulnerabilities in its Known Exploited Vulnerabilities (KEV) catalog, including a Linux kernel privilege elevation flaw. The high-severity flaw tracked as CVE-2024-1086 was first disclosed on January 31, 2024, as a use-after-free problem in the netfilter: nf_tables component, but was first introduced by a commit…
Recent Posts
- Telegram for Android hit by a zero-day exploit – Week in security with Tony Anscombe
- French Authorities Launch Operation to Remove PlugX Malware from Infected Systems
- Malicious PyPI Package Targets macOS to Steal Google Cloud Credentials
- Secure Boot no more? Leaked key, faulty practices put 900 PC/server models in jeopardy
- Crooks Bypassed Google’s Email Verification to Create Workspace Accounts, Access 3rd-Party Services – Krebs on Security
